In this post, we will explore FILS – Fast Initial Link Setup, which was originally defined in IEEE 802.11ai in 2016 and later incorporated into the IEEE 802.11-2020 main standard. A Wi-Fi client connecting to an AP has to go through the Discovery, Authentication/Association, and IP Addressing process as shown below.
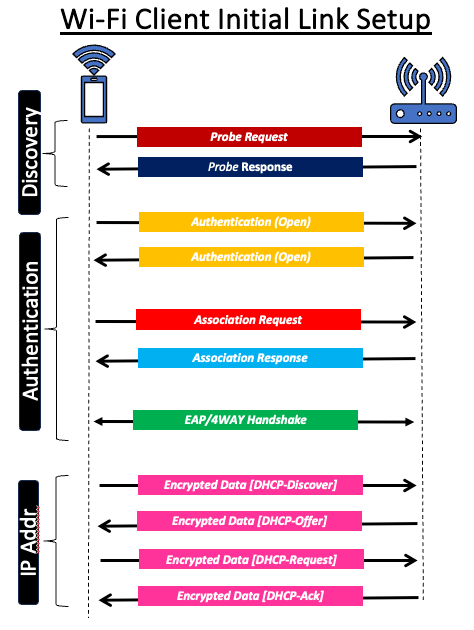
FILS encompasses a collection of mechanisms that enable 802.11 networks to minimize the time required for the initial link setup. This protocol plays a crucial role in enhancing the speed of link setup in all of the 3 phases listed above. Namely
- FILS Discovery (Passive scanning of APs)
- FILS Authentication (Shared Key & Public Key)
- FILS HLP (Higher Layer Setup – eg DHCP for IP Addr)
In densely populated areas like railway stations, large public venues, and conference halls, where Wi-Fi users regularly come and go from the network, managing Wi-Fi can be quite a task. In today’s Wi-Fi setup, client devices (STAs) actively probe to discover access points (APs), and APs have to respond to each client individually. In an environment like the one pictured below (a photo I took while passing through Tokyo Station), when APs have to respond to all those client STA probe requests, it can consume a significant amount of airtime and place a heavy burden on APs.

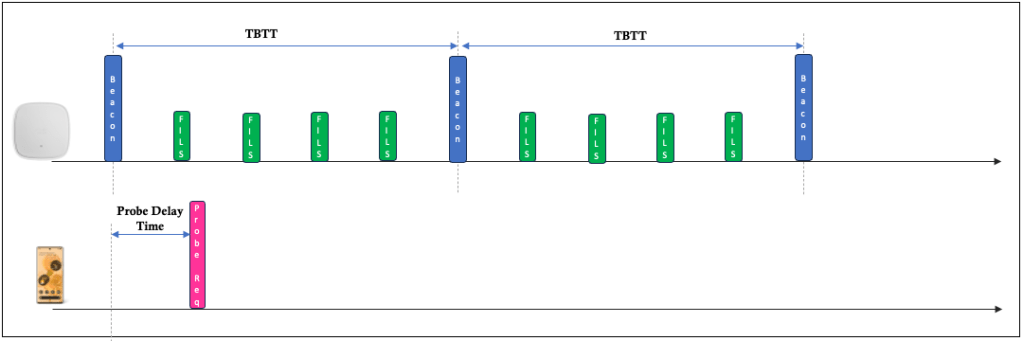
With FILS Discovery, “Probe Deferral and Suppression” should be implemented by AP. Client STA may support it. With that, before client STA sends a probe request, it must listen for broadcast beacon and probe responses for a time known as Probe Delay time before sending probe request.
When client STA sends probe requests it must list the APs that it already knows about. This will allow APs to suppress their responses.
AP that supports FILS, sends FILS discovery frame every 20 TU (~20ms). The first FILS discovery frame 20TU after the TBTT (Target Beacon Transmission Time).
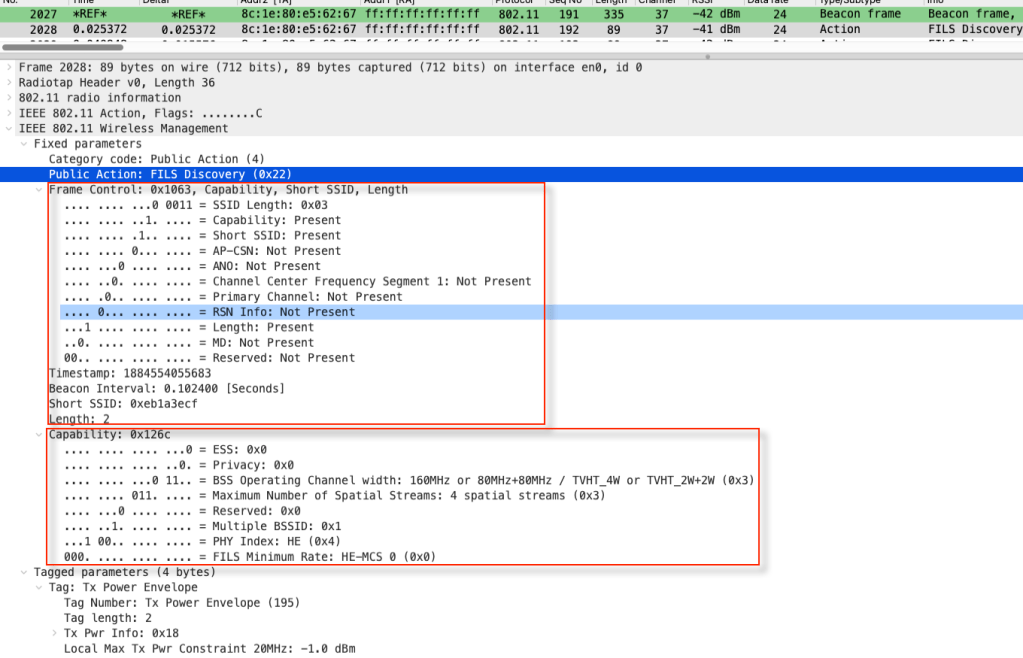
There is an action frame type called “Public Action Frames” defined by IEEE 802.11-2020 (ref Table 9-364) for general communication (AP to unassociated STA ). Public Action Field value 34 (or hex 0x22) is assigned for FILS Discovery. The below diagram shows the FILS discovery frame contents.

Here is a PCAP of Cisco AP that enabled FILS discovery on the 6GHz band. As you can see FILS discovery messages are broadcast by AP in ~20ms intervals.

Note that FILS discovery messages are small in size compared to beacon frames (335 bytes vs. 89 bytes in length in my example). FILS Discovery frame format is shown in the below diagram.

In our example, if you look at the details of the “FILS Discovery or FD ” frame you will see that “FD Frame control” information subfield with below information field in it.
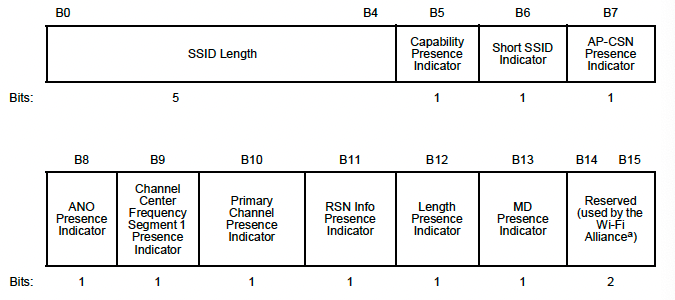
If the “Capability Presence Indicator” is set to 1 then you will see “FILS Discovery Capability” subfield with the information shown below.
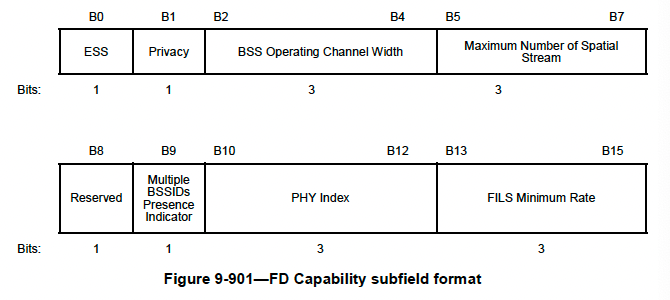
In our sample PCAP, “Capability Presence” is set to 1, therefore “FD – Capability” information exists in it. Operating bandwidth indicates the BSS operation channel width [ 0-20MHz, 1-40MHz, 2 -80MHz, 3-160MHz]. In this example, value 3 indicates we use 160MHz channel width. The spatial Stream (SS) subfield indicates the SS supported by AP [0: 1SS, 1: 2SS, 2: 3SS, 3: 4SS, 4: 5-8SS].
PHY Index subfield defined PHY is in use [ 0 – HR/DSSS, 1– ERP-OFDM, 2 – HT, 3– VHT, 4 – HE]. FILS min rate indicates the minimum rate used by AP and in subsequent transmission between AP Y FILS STA. Value 0-4 indicated MCS0-MCS4 respectively for HT/VHT/HE PHY.
IEEE defined 4 AKM suite selectors (ref table 9.151 in IEEE 802.11-2020) for FILS.
- 00-0F-AC [14] – FILS with SHA-256 and AES-SIV-256
- 00-0F-AC [15] – FILS with SHA-384 and AES-SIV-512
- 00-0F-AC [16] – FT over FILS with SHA-256 and AES-SIV-256
- 00-0F-AC [17] – FT over FILS with SHA-384 and AES-SIV-512
If FILS Authentication has been implemented, that information will be included in FD RSN information subfield. FD RSN information subfield format is shown below. Since most of the vendors have not implemented those FILS AKM, in the captures above you do not see those information subfields.

AKM suite selector value indicates the AKM type being used.
[0] – Use AKM from RSN IE beacon/probe response
[1] – AKM Suite 14 (FILS with SHA-256)
[2] – AKM Suite 15 (FILS with SHA-384)
[3] – AKM suite 14 or 15
[4] – AKM suite 17 (FT over FILS with SHA-384)
[62] – Vendor Specific
[63] – No AKM suite selected
Client STA lists FILS support on the “Probe Request” frame under the “Extended Capabilities” field – Octet 10. As you can see below Pixel 6 supports FILS and listed its support in Probe Request (frame#2385). However current version of Wireshark does not decode the “FILS Request Parameter” field properly (as these are all new)

That field should have the following information fields as per the IEEE 802.11-2020 standard

FILS is part of the Wi-Fi Alliance certification called “Wi-Fi Optimized Connectivity” or known as OCE Optimized Connectivity Experience. We will look at that certification in a separate post.
In our next post, we will explore how FILS is being used for 6GHz AP discovery.
Reference
1. Faster Connection – WLPC 2018 talk by Veli-Pekka Ketonen (7 Signal).

This feature was new to me!
Thanks for sharing.
also u can edit the post, found this typos “Publick, disvoery, Prsence”
have a nice day!
Hi db,
Thank you very much for detailed look and pointing those typos. I have corrected it in the post
Thanks again
Rasika
Thank you for always informative posts.. This is great!
HI Jayrbi,
Thank you very much for your kind words
KIT
Rasika
Thank you for the post.
if the STA receives the discovery frame, the STA does not send the probe request? for broadcasting?.
The procedure is quite confusing