Tags
In this post, we will look at WiFi Alliance WPA3-SAE (also known as WPA3-Personal) to replace WPA2-Personal which is susceptible to offline dictionary attack. It is based on SAE – Simultaneous Authentication of Equals, an password based authentication and key establishment protocol initially introduced in IEEE 802.11s for mesh networks.
In WPA2-Personal, PMK is derived from the password hence a major weakness of that mechanism (it is very easy to decrypt WPA2-PSK traffic). With WPA3-Personal, PMK is not depend on the password.
WiFi Alliance also introduced WPA3-SAE Transition Mode which we will look at in a later post. Protected Management Frames (PMF) is mandatory in WPA3-SAE mode.
Cisco introduced WPA3 support to its AireOS based controllers from version 8.10.x onward (It is 16.12 onward for IOS-XE based controllers). In this post we use AireOS based WLAN configuration to study WPA3-SAE operation. Pls note that following restriction applies when you configure WPA3-SAE in AireOS 8.10.x version.
– IPSK with SAE is not supported
– FT with SAE is not supported
Here is the WLAN security configuration on my SSID.
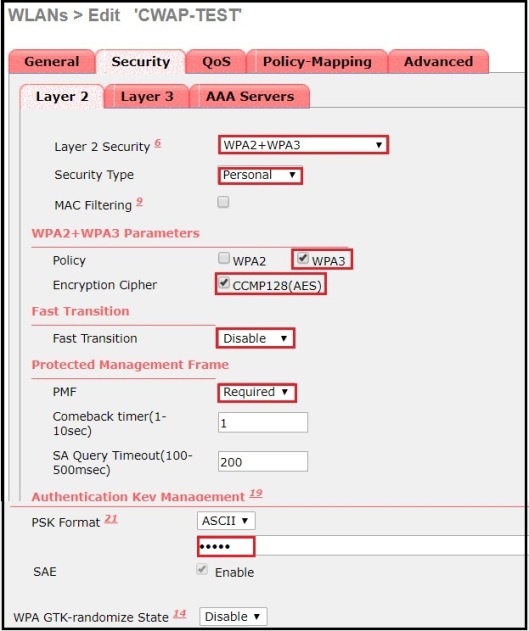
Here is a packet capture when client is connecting to above SSID (follow this post to see packets as 802.11 frames). If you look at the frame exchange,you will see it includes 4 Authentication frames, Association Request, Association Response followed by 4-Way Handshake (M1-M4 messages).
If you look at details of a Beacon frame, you will notice AKM Suite is 00-0F-AC:8 (SAE) under RSNE. Also note that both MFP Required & MFP Capable set to true (In other words management frame protection is mandatory with SAE).
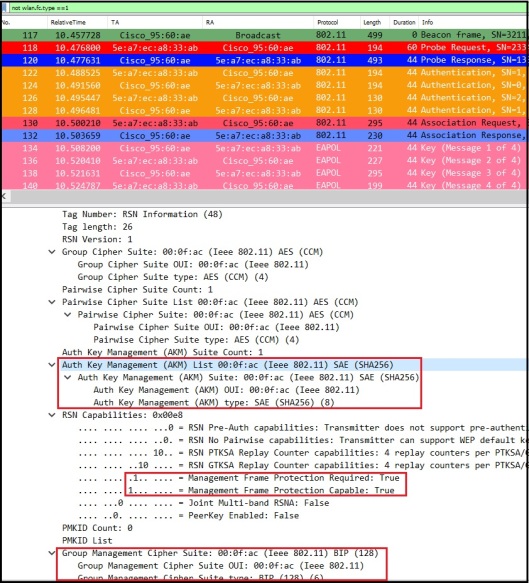
Cipher Suites
In RSNE, there are three type of cipher suites
1. Group Data Cipher Suite – contain cipher suite selector used by BSS to protect group addressed frames.
2. Pairwise Cipher Suit List– contain series of cipher suite selectors that indicate pairwise cipher suites.
3. Group Management Cipher Suite – cipher suite selector used by BSS to protect group addressed robust management frames.
When management frame protection is negotiated, the negotiated pairwise cipher suite is used to protect individually addressed robust Management frames, and the group management cipher suite is used to protect group addressed robust Management frames.
Cipher Suite Selectors defined in IEEE802.11-2016 standard (table 9.131) shown below. Highlighted Group Data Cipher Suite, Pairwise Cipher Suite (CCMP-128) and Group Management Cipher Suite (BIP-CMAC-128) used in given BSS in my capture.
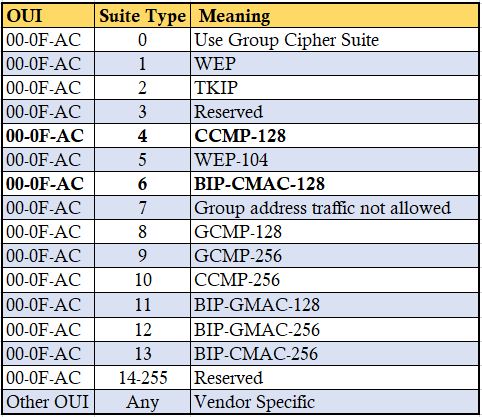
AKM Suite
AKM Suite Count field indicate the number of AKM suite selectors in the AKM Suite list field. AKM Suite list field contains a series of AKM suite selectors.
Table below shown AKM suite defined in IEEE 802.11-2016 standard. Highlighted AKM is the one seen in our capture (00-0F-AC:8 which is SAE). Note that 00-0F-AC:9 also for SAE with FT support. WPA3-SAE Certification does not require to have FT support.
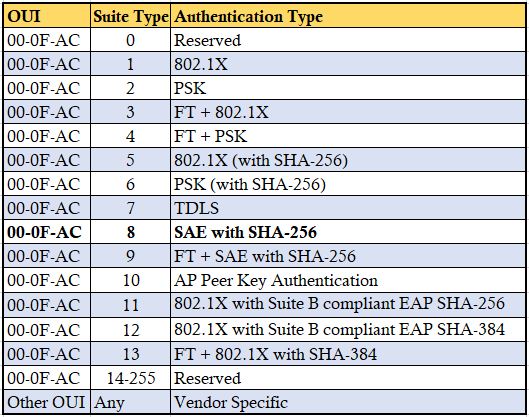
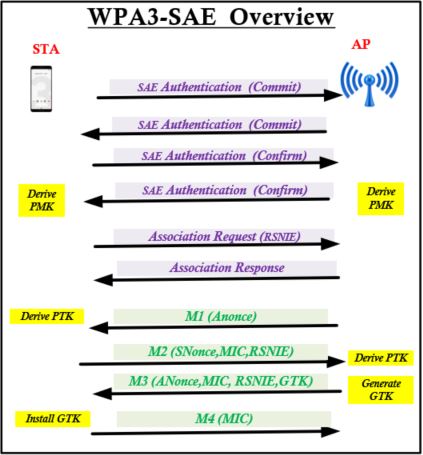
If you look at those Authentication frames, you will notice there are 4 frames in total. Note that Authentication Algorithm number is 3, which is used for SAE. Below shows different Auth Algorithm numbers used in WiFi.
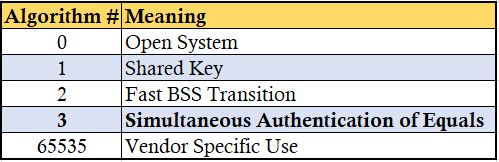
Prior to exchange SAE auth messages, both side generate a secret element PWE (Password Element) & two secret values (rand & mask). A group is selected and minimum ECDH-Group 19 support (256 bit) must be there for interoperablity.
First two auth messages are SAE message type “Commit or 1” (Auth Seq No 1) and other two are SAE message type “Confirm or 2” (Auth Seq No 2). Her is the first Authentication frame details. Commit message contain Grooup ID, a Scalar & an element (FFE) that is produced using PWE (equivalent to public key)
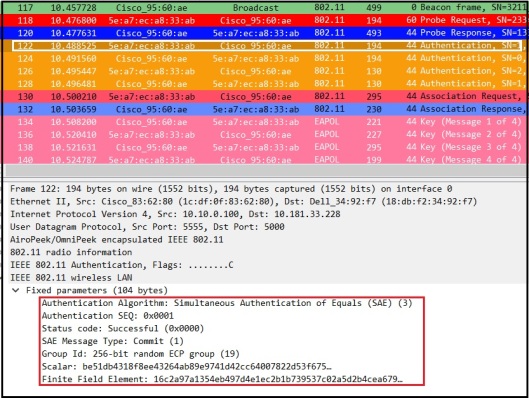
AP also send an authentication frame that include Group Number & its pubic key (FFE)
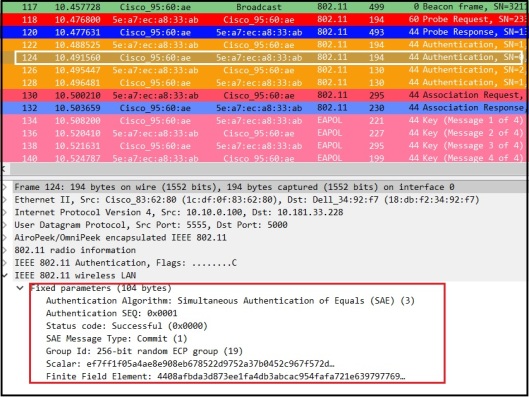
Through “Confirm” messages both side confirm that they have same keys. It includes a hash of the key generated where other party can verify it once received.
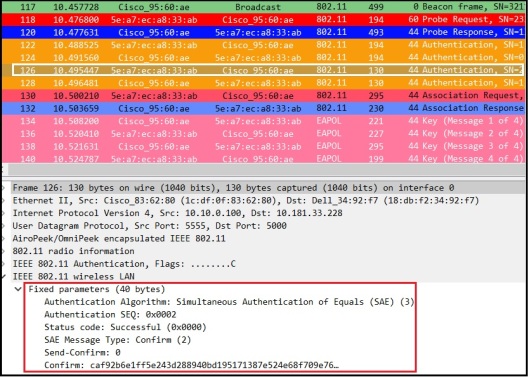
Here is the “Confirm” message goes from AP to STA.
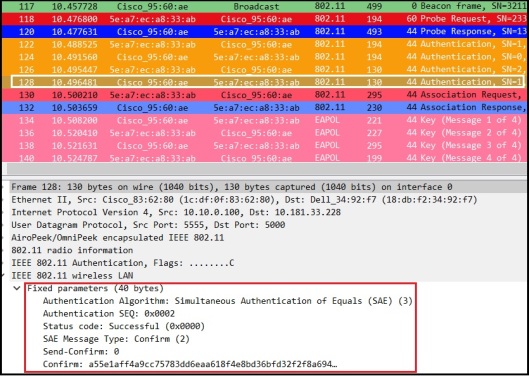
Once SAE message exchange complete, client send Association Request. Note that AKM 00-0F-AC:8 is used to indicate SAE is in use.
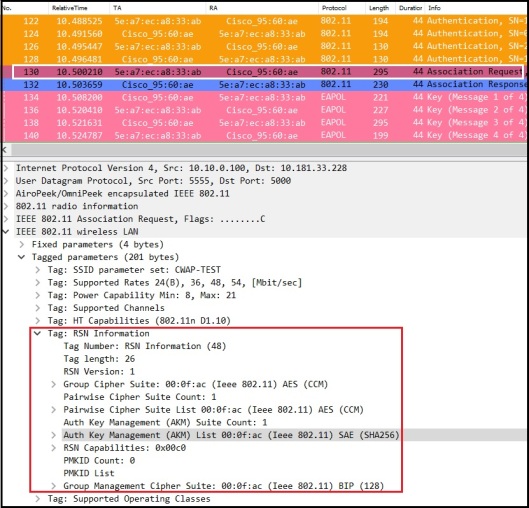
You will see “successful”status in association response.
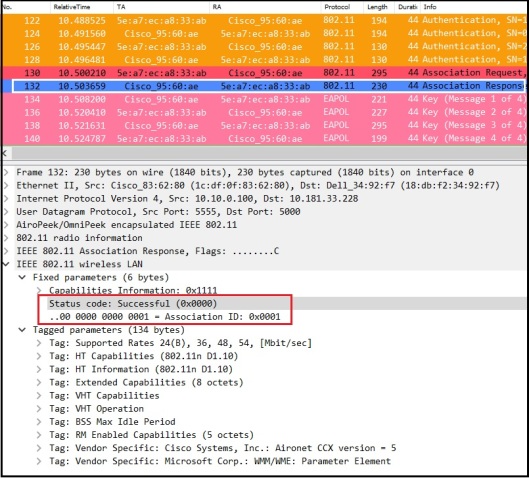
Then AP & STA go through 4 way handshake to derive its encryption keys. Once encryption keys derive, all data traffic will be encrypted. In this method, there is no way of decrypting that traffic, even if SSID password being compromised.
Here is when AirCheckG2 is trying to connect to this SSID. Since it is not supporting WPA3 (with v4.0 firmware) , it won’t able to connect. Once exchange two open Auth frames, it is sending Association Request with AKM as PSK (00-0F-AC:2).
Note that capture shown below has taken when AG2 connecting to different AP advertising same SSID, CWAP-TEST.
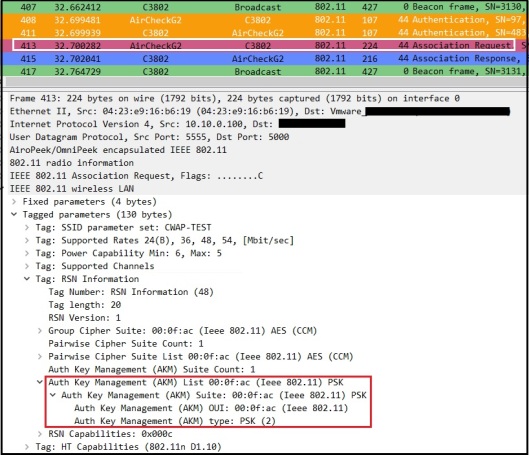
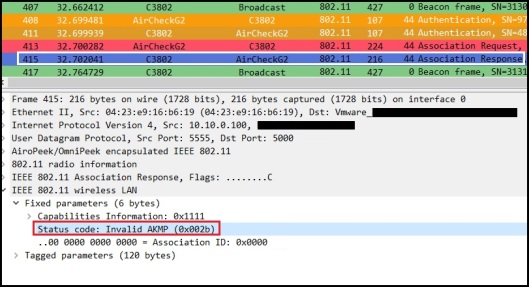
AP respond with Association Response message with status code unsuccessful (failure code 43 – Invalid AKMP)
Since most devices still may not support this WPA3-SAE mode of operation, Transition mode implementation is required if you want both WPA3-SAE supported devices and other devices to connect to same SSID. We will look at that mode in next post.
References
1. WPA3, OWE and DPP | Hemant Chaskar | WLPC Phoenix 2019
2.WPA3 support for AireOS 8.10/ IOS-XE 16.12
3. Dragonblood A Security Analysis of WPA3’s SAE Handshake by Mathy Vanhoef
4. https://wificoops.com/2019/07/28/wi-fi-security-enhancements-part-1-wpa3-personal-sae/
Related Posts
1. End of Cisco AireOS?
2. Enhanced Open – Part 1
3. Enhanced Open – Part 2 (Transition Mode)
4. WPA3-SAE Transition Mode
5. WPA3-Enterprise

Good article, really helpful.
But I think the pcap file is wrong, it’s not a 802.11 raw packet capture.
Maybe you uploaded the another file? Or if I just misunderstood something?
Hi Jing, These packets captured using sniffer mode AP. You have to follow method given below to see it as 802.11 frames
Rasika
This seems to be a source of problem why no Apple device can connect to WPA2/3 mixed mode network. But as is stated when configuring the SSID on the controller, “SAE must be configured when PSK is configured”
Hi Pavel, I haven’t come across particular issue. Did you try with latest version of iOS
Rasika
Hi Rasika ,
Thanks for valuable information shared for WPA3 Security .
I have one doubt , after SAE handshake both devices derive secret key and which will be used further as seeding material to 4-way Handshake to generate encryption keys like PTK and GTK , but where as in KRACK Attack done on WPA2 , is there any same chance to do here in WPA3 Security ? Why because , finally traffic is encrypted with the PTK & GTK only right ? What is your comment on this ?
I know this WPA3 is more secured and against offline dictionary attacks and some other attacks .
KRACK is not possible in WPA3 devices because KRACK test is done or patches are applied during WPA3 certification,which is mandatory.
Detailed post. Unlike in OWE where groupID and public key are shared in assoc frames , in SAE these groupID and public keys are trasmitted in only in auth frames ?
thanks for the great post. I just have a quick question. ive seen all the articles related to WPA3-personal which say it uses SAE instead of PSK. However, it seems like that even SAE is password-based. I’m just a bit confused. haha. could you confirm if im right?
Hi Lee,
Even in SAE, we use a password, but that will not be part of encryption key derivation. To ensure both AP & Client having reference point, both end needs to configure with a password value.
Pls watch the video from WLPC 2019 given under first reference link. You will understand it better
HTH
Rasika
Pingback: Dual Authentication Key Management (AKM) – A Journey to Fast Transition (FT) – John Waas
Pingback: WPA3 – SAE in Action – Wireless Gnan
Your router configuration options are very rich, what is the router model you are using, I need to buy one. Thanks.
I used Cisco AP with WLC running 8.10.x version
HTH
Rasika
Can we connect 802.11n supported client to WPA3-PSK??
Yes, make sure devices driver version updated to support it. AnyWiFi client manufactured mid July 2020 (even 11n or prior technology to 11ax) & get WiFi Alliance certification, then they should support WPA3-Personal as a mandatory requirement.
HTH
Rasika
Thanks for your article, would you please help list some wireless Router or AP that support WPA3 H2E function?Many thanks.
Hi Rasika,
Thanks for the excellent blog with WPA3-SAE
I have one question with respect to incorrect password. As you said, the PMK derivation is independent of the passphrase (PSK), if the client tries to join with incorrect password, the association is failing at the commit 2 message. Can you please explain on this