Ever had a device suddenly drop off your Wi-Fi and reconnect moments later? It’s easy to blame interference or buggy drivers, but often the cause could be deliberate. Wi-Fi Deauthentication attacks are a simple yet powerful way for attackers—using tools like Flipper Zero—to kick clients off WPA2 networks.
Why? Because management frames in WPA2 are sent unencrypted, leaving your network vulnerable to spoofed commands. In this post, we’ll break down exactly how these attacks work, why WPA2 is exposed, and how WPA3 with Management Frame Protection (MFP) closes that gap forever. Check out the demo below to see the defense in action.
In a standard WPA2 configuration, only data frames are encrypted, while management frames—which handle network operations—remain unprotected. This critical gap allows an attacker to spoof an Access Point’s (AP) MAC address and broadcast forged deauthentication frames. Because these frames are unencrypted, client devices accept them as legitimate commands from the AP and immediately disconnect. By persistently flooding the network with these spoofed frames, an attacker can maintain a Denial-of-Service (DoS) state, effectively locking all users out of the SSID.
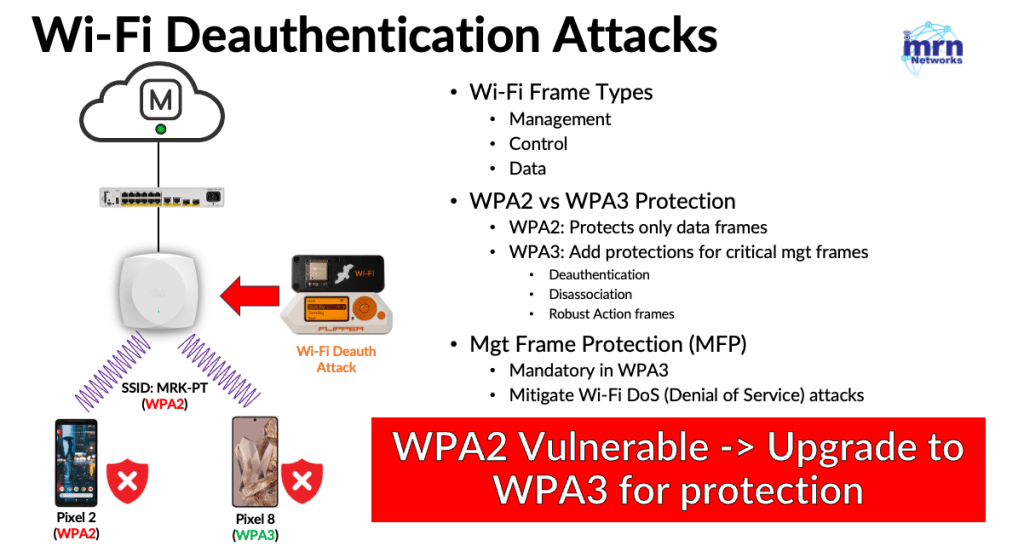
Implementing WPA3 ensures that critical management frames are secured: unicast frames are fully encrypted, while broadcast and multicast frames are protected with a Message Integrity Check (MIC). If your network needs to support legacy WPA2 devices, WPA3 must be deployed in Transition Mode (SSID is configured with WPA2 + WPA3). This allows WPA3-capable clients to benefit from enhanced protections; however, deauthentication attacks remain effective against many WPA2 clients because Management Frame Protection (MFP) is optional in WPA2 and unsupported by many legacy devices. WPA3 mitigates this by requiring MFP.

Alternatively, transitioning to the 6GHz band (Wi-Fi 6E/7) provides a definitive solution. Because WPA3 is mandatory for 6GHz operation, legacy WPA2 security is not supported in this band. This ensures that every client connected to your 6GHz SSID is natively protected by Management Frame Protection, effectively eliminating the threat of deauthentication attacks by design.
Here are the two PCAPs took during this demo

Is it possible to share the .pcap?
Hi, I have updated the post and attached those 2 PCAPs (towards end of the post)
HTH
Rasika