Tags
Web Authentication or Web Auth is a layer 3 security method that allow client to pass DHCP & DNS traffic only untill they have passed some form of authentication. This is greatly used in wireless guest access service where no client side configuration required.
WLC has four authentication policies.
1. Authentication
2. Passthrough
3. Conditional Web Redirect
4. Splash Page Web Redirect
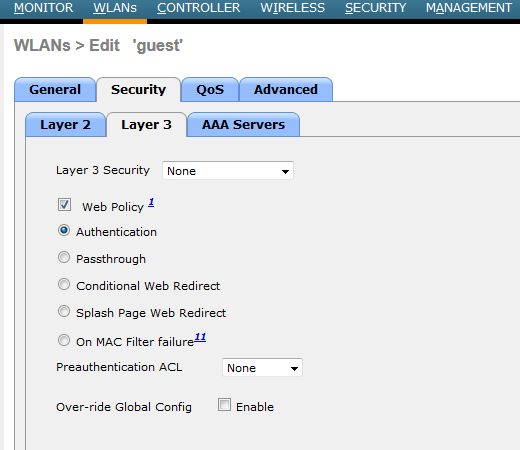
Below shows the authentication policies on layer 3 security tab for a given WLAN of WLC with 7.0.116.0 code.
When you enable Authentication option (as shown in the above screen capture), a guest client has to enter a username & password to gain access to the guest network. Once user get an IP & try to access an URL it authentication screen appear like this.
In VPN Web Passthrough option, guest client just have to simply accept the agreement before gaining to access (no username verification). WLC can be configured to request user to enter his email ID a way of identify the guest user. Once you do that when a guest user access the network it will prompt a screen like this & user can get access by entering his/her email address.
Conditional Web Redirect is commonly used by businesses that are selling network access to users (like hotels). To this to work guest WLAN must have some sort of layer 2 (802.1x or WAP) security configured. When user log on to wireless network from the splash page, a RADIUS server verifies their user credentials. Should certain conditions be met that necessitate another redirect, the client is redirected to a new page (like pay billing for the service).
In Splash Page Web Redirect, the user is redirected to particular web page after successfully completing 802.1x authentication. Once redirect is complete user has full access to the network. This method requried 802.1x or WPA+WPA2 layer 2 security.
There are 3 ways of presenting login page (Internal, Custom & External). In the first two method internal web server of the WLC will be used & you can access it via “SECURITY -> Web Auth -> Web Login Page” as shown below
Here is the steps in Web Authentication Process
Step 1. The Cient enter START state by completing any layer 2 security if necessary
Step 2. After layer 2 Authentication state is complete, the client move to DHCP_REQD state.
Step 3. The client will receive DHCP IP, DNS from the DHCP server. The clients open web browser and PC send a DNS query.
Step 4. The WLC forwards the DNS query.
Step 5. DNS server resolve URL name to IP address.
Step 6. Controller(WLC) forwards the DNS reply.
Step 7. Client Sends HTTP GET to the web server.
Step 8. Controller intercepts the returned web page from the destination web server and sends a redirect to its own internal web server address (virtual interface IP of WLC)
Step 9. The client goes to the login page, passes web authentication and enters the RUN state on the controller.
Step 10. The WLC forwards the client browser to the original web page requested.
Here is the debug client output on WLC in VPN Passthrough configuration. You can see the client state changes during the process { START (0) -> AUTHCHECK (2) -> L2AUTHCOMPLETE (4) -> DHCP_REQD (7)-> WEBAUTH_REQD (8) -> WEBAUTH_NOL3SEC (14) -> RUN (20) }. Also highlighted few other key elements in this debug out put (DHCP DORA, Guest email, etc) which you need to familiar in order to troubleshoot clients issue with respect to Web Auth.
(WLC1) >debug client 64:20:0c:e0:23:75 (WLC1) >*apfMsConnTask_0: Mar 21 07:10:14.812: 64:20:0c:e0:23:75 Adding mobile on LWAPP AP 54:75:d0:3e:80:b0(1) *apfMsConnTask_0: Mar 21 07:10:14.812: 64:20:0c:e0:23:75 Association received from mobile on AP 54:75:d0:3e:80:b0 *apfMsConnTask_0: Mar 21 07:10:14.812: 64:20:0c:e0:23:75 0.0.0.0 START (0) Changing ACL 'WLC-ACL' (ACL ID 0) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:1621) *apfMsConnTask_0: Mar 21 07:10:14.812: 64:20:0c:e0:23:75 Applying site-specific IPv6 override for station 64:20:0c:e0:23:75 - vapId 4, site 'default-group', interface 'vlan14' *apfMsConnTask_0: Mar 21 07:10:14.812: 64:20:0c:e0:23:75 Applying IPv6 Interface Policy for station 64:20:0c:e0:23:75 - vlan 14, interface id 11, interface 'vlan14' *apfMsConnTask_0: Mar 21 07:10:14.812: 64:20:0c:e0:23:75 STA - rates (4): 176 72 96 108 0 0 0 0 0 0 0 0 0 0 0 0 *apfMsConnTask_0: Mar 21 07:10:14.813: 64:20:0c:e0:23:75 0.0.0.0 START (0) Initializing policy *apfMsConnTask_0: Mar 21 07:10:14.813: 64:20:0c:e0:23:75 0.0.0.0 START (0) Change state to AUTHCHECK (2) last state AUTHCHECK (2) *apfMsConnTask_0: Mar 21 07:10:14.813: 64:20:0c:e0:23:75 0.0.0.0 AUTHCHECK (2) Change state to L2AUTHCOMPLETE (4) last state L2AUTHCOMPLETE (4) *apfMsConnTask_0: Mar 21 07:10:14.813: 64:20:0c:e0:23:75 0.0.0.0 L2AUTHCOMPLETE (4) DHCP Not required on AP 54:75:d0:3e:80:b0 vapId 4 apVapId 4for this client *apfMsConnTask_0: Mar 21 07:10:14.813: 64:20:0c:e0:23:75 Not Using WMM Compliance code qosCap 00 *apfMsConnTask_0: Mar 21 07:10:14.813: 64:20:0c:e0:23:75 0.0.0.0 L2AUTHCOMPLETE (4) Plumbed mobile LWAPP rule on AP 54:75:d0:3e:80:b0 vapId 4 apVapId 4 *apfMsConnTask_0: Mar 21 07:10:14.813: 64:20:0c:e0:23:75 0.0.0.0 L2AUTHCOMPLETE (4) Change state to DHCP_REQD (7) last state DHCP_REQD (7) *apfMsConnTask_0: Mar 21 07:10:14.813: 64:20:0c:e0:23:75 apfMsAssoStateInc *apfMsConnTask_0: Mar 21 07:10:14.813: 64:20:0c:e0:23:75 apfPemAddUser2 (apf_policy.c:223) Changing state for mobile 64:20:0c:e0:23:75 on AP 54:75:d0:3e:80:b0 from Idle to Associated *apfMsConnTask_0: Mar 21 07:10:14.813: 64:20:0c:e0:23:75 Stopping deletion of Mobile Station: (callerId: 48) *apfMsConnTask_0: Mar 21 07:10:14.813: 64:20:0c:e0:23:75 Sending Assoc Response to station on BSSID 54:75:d0:3e:80:b0 (status 0) ApVapId 4 Slot 1 *apfMsConnTask_0: Mar 21 07:10:14.813: 64:20:0c:e0:23:75 apfProcessAssocReq (apf_80211.c:5241) Changing state for mobile 64:20:0c:e0:23:75 on AP 54:75:d0:3e:80:b0 from Associated to Associated *apfReceiveTask: Mar 21 07:10:14.833: 64:20:0c:e0:23:75 Orphan Packet from 192.168.1.12 on mobile *apfReceiveTask: Mar 21 07:10:14.834: 64:20:0c:e0:23:75 Orphan Packet from 10.10.14.52 on mobile *apfReceiveTask: Mar 21 07:10:14.834: 64:20:0c:e0:23:75 Orphan Packet from 149.144.156.3 on mobile *DHCP Proxy DTL Recv Task: Mar 21 07:10:14.835: 64:20:0c:e0:23:75 DHCP received op BOOTREQUEST (1) (len 308,vlan 0, port 1, encap 0xec03) *DHCP Proxy DTL Recv Task: Mar 21 07:10:14.836: 64:20:0c:e0:23:75 DHCP dropping packet due to ongoing mobility handshake exchange, (siaddr 0.0.0.0, mobility state = 'apfMsMmQueryRequested' *apfReceiveTask: Mar 21 07:10:14.856: 64:20:0c:e0:23:75 Orphan Packet from 192.168.1.12 on mobile *apfReceiveTask: Mar 21 07:10:14.857: 64:20:0c:e0:23:75 Orphan Packet from 10.10.14.52 on mobile *apfReceiveTask: Mar 21 07:10:14.857: 64:20:0c:e0:23:75 Orphan Packet from 149.144.156.3 on mobile *DHCP Proxy DTL Recv Task: Mar 21 07:10:14.858: 64:20:0c:e0:23:75 DHCP received op BOOTREQUEST (1) (len 308,vlan 0, port 1, encap 0xec03) *DHCP Proxy DTL Recv Task: Mar 21 07:10:14.858: 64:20:0c:e0:23:75 DHCP dropping packet due to ongoing mobility handshake exchange, (siaddr 0.0.0.0, mobility state = 'apfMsMmQueryRequested' *DHCP Proxy DTL Recv Task: Mar 21 07:10:16.253: 64:20:0c:e0:23:75 DHCP received op BOOTREQUEST (1) (len 308,vlan 0, port 1, encap 0xec03) *DHCP Proxy DTL Recv Task: Mar 21 07:10:16.253: 64:20:0c:e0:23:75 DHCP dropping packet due to ongoing mobility handshake exchange, (siaddr 0.0.0.0, mobility state = 'apfMsMmQueryRequested' *apfReceiveTask: Mar 21 07:10:16.804: 64:20:0c:e0:23:75 0.0.0.0 DHCP_REQD (7) State Update from Mobility-Incomplete to Mobility-Complete, mobility role=Local, client state=APF_MS_STATE_ASSOCIATED *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.453: 64:20:0c:e0:23:75 DHCP selected relay 1 - 10.10.14.1 (local address 10.10.14.10, gateway 10.10.14.1, VLAN 14, port 1) *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.454: 64:20:0c:e0:23:75 DHCP transmitting DHCP DISCOVER (1) *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.454: 64:20:0c:e0:23:75 DHCP op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 1 *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.454: 64:20:0c:e0:23:75 DHCP xid: 0x4a8c7dc9 (1250721225), secs: 9, flags: 0 *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.454: 64:20:0c:e0:23:75 DHCP chaddr: 64:20:0c:e0:23:75 *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.454: 64:20:0c:e0:23:75 DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0 *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.454: 64:20:0c:e0:23:75 DHCP siaddr: 0.0.0.0, giaddr: 10.10.14.10 *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.454: 64:20:0c:e0:23:75 DHCP sending REQUEST to 10.10.14.1 (len 350, port 1, vlan 14) *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.454: 64:20:0c:e0:23:75 DHCP selecting relay 2 - control block settings: dhcpServer: 0.0.0.0, dhcpNetmask: 0.0.0.0, dhcpGateway: 0.0.0.0, dhcpRelay: 10.10.14.10 VLAN: 14 *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.454: 64:20:0c:e0:23:75 DHCP selected relay 2 - NONE *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.457: 64:20:0c:e0:23:75 DHCP received op BOOTREPLY (2) (len 308,vlan 14, port 1, encap 0xec00) *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.457: 64:20:0c:e0:23:75 DHCP setting server from OFFER (server 192.168.200.1, yiaddr 10.10.14.52) *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.457: 64:20:0c:e0:23:75 DHCP sending REPLY to STA (len 418, port 1, vlan 111) *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.457: 64:20:0c:e0:23:75 DHCP transmitting DHCP OFFER (2) *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.457: 64:20:0c:e0:23:75 DHCP op: BOOTREPLY, htype: Ethernet, hlen: 6, hops: 0 *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.457: 64:20:0c:e0:23:75 DHCP xid: 0x4a8c7dc9 (1250721225), secs: 0, flags: 0 *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.458: 64:20:0c:e0:23:75 DHCP chaddr: 64:20:0c:e0:23:75 *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.458: 64:20:0c:e0:23:75 DHCP ciaddr: 0.0.0.0, yiaddr: 10.10.14.52 *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.458: 64:20:0c:e0:23:75 DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0 *DHCP Proxy DTL Recv Task: Mar 21 07:10:23.458: 64:20:0c:e0:23:75 DHCP server id: 1.1.1.1 rcvd server id: 192.168.200.1 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.479: 64:20:0c:e0:23:75 DHCP received op BOOTREQUEST (1) (len 308,vlan 0, port 1, encap 0xec03) *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.480: 64:20:0c:e0:23:75 DHCP selecting relay 1 - control block settings: dhcpServer: 192.168.200.1, dhcpNetmask: 0.0.0.0, dhcpGateway: 0.0.0.0, dhcpRelay: 10.10.14.10 VLAN: 14 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.480: 64:20:0c:e0:23:75 DHCP selected relay 1 - 192.168.200.1 (local address 10.10.14.10, gateway 10.10.14.1, VLAN 14, port 1) *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.480: 64:20:0c:e0:23:75 DHCP transmitting DHCP REQUEST (3) *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.480: 64:20:0c:e0:23:75 DHCP op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 1 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.480: 64:20:0c:e0:23:75 DHCP xid: 0x4a8c7dc9 (1250721225), secs: 10, flags: 0 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.480: 64:20:0c:e0:23:75 DHCP chaddr: 64:20:0c:e0:23:75 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.480: 64:20:0c:e0:23:75 DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.480: 64:20:0c:e0:23:75 DHCP siaddr: 0.0.0.0, giaddr: 10.10.14.10 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.480: 64:20:0c:e0:23:75 DHCP requested ip: 10.10.14.52 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.480: 64:20:0c:e0:23:75 DHCP server id: 192.168.200.1 rcvd server id: 1.1.1.1 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.480: 64:20:0c:e0:23:75 DHCP sending REQUEST to 10.10.14.1 (len 350, port 1, vlan 14) *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.480: 64:20:0c:e0:23:75 DHCP selecting relay 2 - control block settings: dhcpServer: 192.168.200.1, dhcpNetmask: 0.0.0.0, dhcpGateway: 0.0.0.0, dhcpRelay: 10.10.14.10 VLAN: 14 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.485: 64:20:0c:e0:23:75 Adding Web RuleID 15 for mobile 64:20:0c:e0:23:75 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.485: 64:20:0c:e0:23:75 10.10.14.52 DHCP_REQD (7) Change state to WEBAUTH_REQD (8) last state WEBAUTH_REQD (8) *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.485: 64:20:0c:e0:23:75 10.10.14.52 WEBAUTH_REQD (8) pemAdvanceState2 5170, Adding TMP rule *DHCP P: Mar 21 07:10:24.485: 64:20:0c:e0:23:75 10.10.14.52 WEBAUTH_REQD (8) Replacing Fast Path rule type = Airespace AP Client - ACL passthru on AP 54:75:d0:3e:80:b0, slot 1, interface = 1, QOS = 2 ACL Id = *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.485: 64:20:0c:e0:23:75 10.10.14.52 WEBAUTH_REQD (8) Fast Path rule (contd...) 802.1P = 6, DSCP = 0, TokenID = 5006 IPv6 Vlan = 14, IPv6 intf id = 11 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.485: 64:20:0c:e0:23:75 10.10.14.52 WEBAUTH_REQD (8) Successfully plumbed mobile rule (ACL ID 255) *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.485: 64:20:0c:e0:23:75 Plumbing web-auth redirect rule due to user logout *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.485: 64:20:0c:e0:23:75 Assigning Address 10.10.14.52 to mobile *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.485: 64:20:0c:e0:23:75 DHCP success event for client. Clearing dhcp failure count for interface vlan14. *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.486: 64:20:0c:e0:23:75 DHCP sending REPLY to STA (len 418, port 1, vlan 111) *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.486: 64:20:0c:e0:23:75 DHCP transmitting DHCP ACK (5) *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.486: 64:20:0c:e0:23:75 DHCP op: BOOTREPLY, htype: Ethernet, hlen: 6, hops: 0 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.486: 64:20:0c:e0:23:75 DHCP xid: 0x4a8c7dc9 (1250721225), secs: 0, flags: 0 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.486: 64:20:0c:e0:23:75 DHCP chaddr: 64:20:0c:e0:23:75 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.486: 64:20:0c:e0:23:75 DHCP ciaddr: 0.0.0.0, yiaddr: 10.10.14.52 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.486: 64:20:0c:e0:23:75 DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0 *DHCP Proxy DTL Recv Task: Mar 21 07:10:24.486: 64:20:0c:e0:23:75 DHCP server id: 1.1.1.1 rcvd server id: 192.168.200.1 *pemReceiveTask: Mar 21 07:10:24.494: 64:20:0c:e0:23:75 149.144.156.3 Added NPU entry of type 2, dtlFlags 0x0 *pemReceiveTask: Mar 21 07:10:24.496: 64:20:0c:e0:23:75 Sent an XID frame *pemReceiveTask: Mar 21 07:10:24.499: 64:20:0c:e0:23:75 149.144.156.3 Added NPU entry of type 9, dtlFlags 0x0 *pemReceiveTask: Mar 21 07:10:24.504: 64:20:0c:e0:23:75 10.10.14.52 Added NPU entry of type 2, dtlFlags 0x0 *pemReceiveTask: Mar 21 07:10:24.507: 64:20:0c:e0:23:75 Sent an XID frame *apfReceiveTask: Mar 21 07:11:07.556: 64:20:0c:e0:23:75 Orphan Packet from 10.10.14.52 on mobile *apfReceiveTask: Mar 21 07:11:07.559: 64:20:0c:e0:23:75 Orphan Packet from 10.10.14.52 on mobile *emWeb: Mar 21 07:11:43.425: 64:20:0c:e0:23:75 Username entry (raji_harshi@yahoo.com) created for mobile *emWeb: Mar 21 07:11:43.425: 64:20:0c:e0:23:75 10.10.14.52 WEBAUTH_REQD (8) Change state to WEBAUTH_NOL3SEC (14) last state WEBAUTH_NOL3SEC (14) *emWeb: Mar 21 07:11:43.429: 64:20:0c:e0:23:75 apfMsRunStateInc *emWeb: Mar 21 07:11:43.430: 64:20:0c:e0:23:75 10.10.14.52 WEBAUTH_NOL3SEC (14) Change state to RUN (20) last state RUN (20) *emWeb: Mar 21 07:11:43.430: 64:20:0c:e0:23:75 Session Timeout is 0 - not starting session timer for the mobile *emWeb: Mar 21 07:11:43.430: 64:20:0c:e0:23:75 10.10.14.52 RUN (20) Reached PLUMBFASTPATH: from line 5063 *emWeb: Mar 21 07:11:43.430: 64:20:0c:e0:23:75 10.10.14.52 RUN (20) Replacing Fast Path rule type = Airespace AP Client on AP 54:75:d0:3e:80:b0, slot 1, interface = 1, QOS = 2 ACL Id = 255, Jumbo Frames = NO *emWeb: Mar 21 07:11:43.430: 64:20:0c:e0:23:75 10.10.14.52 RUN (20) Fast Path rule (contd...) 802.1P = 6, DSCP = 0, TokenID = 5006 IPv6 Vlan = 14, IPv6 intf id = 11 *emWeb: Mar 21 07:11:43.430: 64:20:0c:e0:23:75 10.10.14.52 RUN (20) Successfully plumbed mobile rule (ACL ID 255) *pemReceiveTask: Mar 21 07:11:43.438: 64:20:0c:e0:23:75 10.10.14.52 Added NPU entry of type 1, dtlFlags 0x0 *pemReceiveTask: Mar 21 07:11:43.441: 64:20:0c:e0:23:75 Sending a gratuitous ARP for 10.10.14.52, VLAN Id 53262
Here is the link to Cisco Doc ID#115951 which describe Web Authentication on WLC. Please read this for more inner details .
Related Posts
1. Auto Anchor Mobility
2. Configuring Wired Guest





Rasrika,
correct me if I’m wrong , but I assume You meant Web Passthrough instead of VPN Passthrough.
Regrads,
Marko
Thanks Marko,, yes I meant web passthrough & I have corrected it
hello,
Can you tell me how to do vlan assignment in local webauth through ISE in wired network.
Thanks,
Piyush
Hi,
Does the user always has to open webbrowser to get Web login page https://1.1.1.1/login.html? I used to be able to connet to Guest wirless network by going to my iPad settings -> wi-fi and choosing a network. After taping on the Guest Network a web login page would pop up. However it doesnt seem to be always working. And sometimes the web login page doent show up and I can see on the WLC that the client is stuc in the WEBAUT_REQD state.
Thanks,
Anna
User does not want to go for the virutal IP of WLC.
Any webpage should be redirected.
What WLC code are you running ?
HTH
Rasika
Its a Cisco 5500 with software version 7.4.121.0.
What I meant that the WLC presents the user with https://1.1.1.1/login.html which is the authentication web login page.
If I try to connect to Internet
Thanks,
Anna
…webpage I will not get access untill going to my iPad settings and connecting to a wirless network. Only this action will bring up the authentication login webpage of the WLC.
Thanks,
Anna
hello
the Authentication option I can add some more parameter without User and password, such as phone and email?
appreciate the attention
email option is there for “Web Passthrough” method. But nothing else.
HTH
Rasika
thank1s Rasika…
Hello Nayarasi,
I saw the following log above:
DHCP dropping packet due to ongoing mobility handshake exchange
And I´ve seen this same log on my environment. Such environment have sobre problem regards DHCP. Sometimes clients can´t get an IP address.
Should I worry about this log ?
Thanks in advanced ?
If you have more than 1 WLC on your setup & all are in the same mobility group, those messages are normal.
Once a client associate to AP, that AP managed WLC first check with other WLCs if that client is associated there (to see if it is a roam). So until that process is complete client won’t get an IP & DHCP packets get dropped. This is the normal behavior in that case.
HTH
Rasika
Hello,
For any mode of Authentication , L2 or L3 the client never directly communicates with the radius server but all communication is proxied via the WLC ?
Hello,
I want to use the splash page to inform the user that this SSID will be disable. They need to know that they should use the new SSID. I want no further login.
This is one of some how to’s I’ve used:
http://www.cisco.com/c/en/us/support/docs/wireless/4400-series-wireless-lan-controllers/100787-splash-page-redirect.html
The freeRadius Server send a redirection url, but on the client it will be ignored.
Have you a how to for the case or can you write a how to?
THX
Hi,
I have a question regarding customized web auth bundle..
Is it possible to configure one SSID to use customized web authentication and another SSID with customized web passthrough page. Both SSID would use the same redirect web url after successful authentication/clicking agree with disclaimer.. And all this would done on the same WLC2504 running 8.3 code?
Thanks a bunch for any feedback.
BR Alex
Hello, How can i set microsoft edge for the captive portal default?