If you already read one of my previous post (Lightweight to Autonomous (vice versa) Conversion…) you may konw one way of doing this AP conversion.
In this post we will see how to do the same task using Mode/Reset button of the Access point. Number 1 in the below diagram shows this Reset button of the given AP.
 You can use this mode/reset button when you do not know password or your AP firmware is corrupted,etc. In our case, even the firmware is not corrupted, we can use this button to load an image from a TFTP server. In this scenario, AP is looking for a specifically named image file to load. So if you keep a Autonomous image file with the correct named syntax, AP will load that image once we do this.
You can use this mode/reset button when you do not know password or your AP firmware is corrupted,etc. In our case, even the firmware is not corrupted, we can use this button to load an image from a TFTP server. In this scenario, AP is looking for a specifically named image file to load. So if you keep a Autonomous image file with the correct named syntax, AP will load that image once we do this.
Before starting we will look at some of the AP model Autonomous & Lightweigth recovery images. As you can see below certain AP models are having common images (like 2600,3600 or 1040, 1140 or 1260,3500) for this purpose.
 In this example I am using 3500 series AP & therefore I have downloaded ap3g1-k9w7-tar.152-4.JA1.tar & ap3g1-rcvk9w8-tar.152-4.JA1.tar files onto my TFTP server. Now you need to rename these in order to load it to AP when it is resetting using mode button. Below shows the how it should be renamed. Since it expecting same default filename you have to make sure correct file renames depend on you are doing LAP-> AAP or AAP->LAP conversion process.
In this example I am using 3500 series AP & therefore I have downloaded ap3g1-k9w7-tar.152-4.JA1.tar & ap3g1-rcvk9w8-tar.152-4.JA1.tar files onto my TFTP server. Now you need to rename these in order to load it to AP when it is resetting using mode button. Below shows the how it should be renamed. Since it expecting same default filename you have to make sure correct file renames depend on you are doing LAP-> AAP or AAP->LAP conversion process.
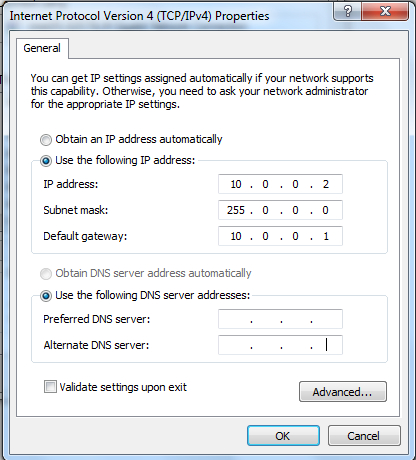
 Since AP resetting to factory default, it will always takes 10.0.0.1 IP. So your TFTP server should be on the same subnet (most of the time your PC act as TFTP server directly connect AP ethernet port). Here is my TFTP/PC IP seettings
Since AP resetting to factory default, it will always takes 10.0.0.1 IP. So your TFTP server should be on the same subnet (most of the time your PC act as TFTP server directly connect AP ethernet port). Here is my TFTP/PC IP seettings
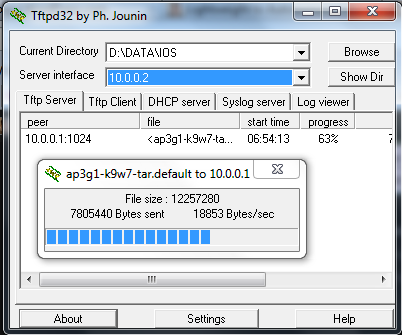
 Now everything is ready for the conversion. First we will take Lightweight AP & convert it to Autonomous. Ensure you have renamed “ap3g1-k9w7-tar.152-4.JA1.tar ” file to “ap3g1-k9w7-tar.default” & available it on your TFTP server.
Now everything is ready for the conversion. First we will take Lightweight AP & convert it to Autonomous. Ensure you have renamed “ap3g1-k9w7-tar.152-4.JA1.tar ” file to “ap3g1-k9w7-tar.default” & available it on your TFTP server.
To do this you need to hold the mode/reset button for 20s (until the LED become solid RED) while powering on the AP. You can watch the console output to see what’s happening in the background.
using MCNG ddr static values from serial eeprom ddr init done IOS Bootloader - Starting system. FLASH CHIP: Numonyx P33 Checking for Over Erased blocks ...................................................................................................................................................................................................................................................... Xmodem file system is available. DDR values used from system serial eeprom. WRDTR,CLKTR: 0x8200083f, 0x40000000 RQDC, RFDC : 0x80000033, 0x00000218 PCIE0: link is up. PCIE0: VC0 is active PCIE1: link is up. PCIE1: VC0 is active 64bit PCIE devices PCIEx: initialization done flashfs[0]: 41 files, 9 directories flashfs[0]: 0 orphaned files, 0 orphaned directories flashfs[0]: Total bytes: 31739904 flashfs[0]: Bytes used: 14926336 flashfs[0]: Bytes available: 16813568 flashfs[0]: flashfs fsck took 10 seconds. Reading cookie from system serial eeprom...Done Base Ethernet MAC address: cc:ef:48:72:0f:b5 Ethernet speed is 1000 Mb - FULL duplex button is pressed, wait for button to be released... button pressed for 23 seconds process_config_recovery: set IP address and config to default 10.0.0.1 process_config_recovery: image recovery image_recovery: Download default IOS tar image tftp://255.255.255.255/ap3g1-k9w7-tar.default examining image... extracting info (283 bytes) Image info: Version Suffix: k9w7-.152-2.JB Image Name: ap3g1-k9w7-mx.152-2.JB Version Directory: ap3g1-k9w7-mx.152-2.JB Ios Image Size: 1126912 Total Image Size: 12257792 Image Feature: WIRELESS LAN|LWAPP Image Family: AP3G1 Wireless Switch Management Version: 7.4.1.37 Extracting files... . . . . extracting ap3g1-k9w7-mx.152-2.JB/info (283 bytes) extracting info.ver (283 bytes) Deleting current version: flash:/ap3g1-k9w8-mx.v152_2_jb.201310220755...done. New software image installed in flash:/ap3g1-k9w7-mx.152-2.JB Configuring system to use new image...done. Requested system reload in progress...download took about 731 seconds Loading "flash:/ap3g1-k9w7-mx.152-2.JB/ap3g1-k9w7-mx.152-2.JB"...################ File "flash:/ap3g1-k9w7-mx.152-2.JB/ap3g1-k9w7-mx.152-2.JB" uncompressed and installed, entry point: 0x4000 executing...
You will see AP is downloading the “.default” image from your TFTP server.
 Once image is fully loaded, AP will reboot & come up as a Autonomous AP. Noticed that “ap>” promt indicating it is an Autonomous AP on its default settings.
Once image is fully loaded, AP will reboot & come up as a Autonomous AP. Noticed that “ap>” promt indicating it is an Autonomous AP on its default settings.
ap>en Password: Cisco ap#sh ver Cisco IOS Software, C3500 Software (AP3G1-K9W7-M), Version 15.2(2)JB, RELEASE SOFTWARE (fc1) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2012 by Cisco Systems, Inc. Compiled Mon 10-Dec-12 23:42 by prod_rel_team ROM: Bootstrap program is C3500 boot loader BOOTLDR: C3500 Boot Loader (AP3G1-BOOT-M), Version 12.4 [mpleso-ap_jmr3_esc_0514 125] ap uptime is 2 minutes System returned to ROM by power-on System image file is "flash:/ap3g1-k9w7-mx.152-2.JB/ap3g1-k9w7-xx.152-2.JB" Last reload reason:
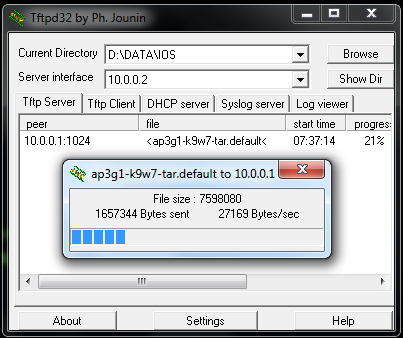
Now you can follow the same process, if you want to convert it back to Lightweight. Make sure “ap3g1-rcvk9w8-tar.152-4.JA1.tar” file is renamed to “ap3g1-k9w7-tar.default” file is available on your TFTP server.(you may have to remove or rename previously used .default file for LAP->AAP conversion)
IOS Bootloader - Starting system. FLASH CHIP: Numonyx P33 Checking for Over Erased blocks ...................................................................................................................................................................................................................................................... Xmodem file system is available. DDR values used from system serial eeprom. WRDTR,CLKTR: 0x8200083f, 0x40000000 RQDC, RFDC : 0x80000033, 0x00000218 PCIE0: link is up. PCIE0: VC0 is active PCIE1: link is up. PCIE1: VC0 is active 64bit PCIE devices PCIEx: initialization done flashfs[0]: 198 files, 9 directories flashfs[0]: 0 orphaned files, 0 orphaned directories flashfs[0]: Total bytes: 31739904 flashfs[0]: Bytes used: 15564800 flashfs[0]: Bytes available: 16175104 flashfs[0]: flashfs fsck took 10 seconds. Reading cookie from system serial eeprom...Done Base Ethernet MAC address: cc:ef:48:72:0f:b5 Ethernet speed is 1000 Mb - FULL duplex button is pressed, wait for button to be released... button pressed for 21 seconds process_config_recovery: set IP address and config to default 10.0.0.1 process_config_recovery: image recovery image_recovery: Download default IOS tar image tftp://255.255.255.255/ap3g1-k9w7-tar.default examining image... extracting info (263 bytes) Image info: Version Suffix: rcvk9w8- Image Name: ap3g1-rcvk9w8-mx Version Directory: ap3g1-rcvk9w8-mx Ios Image Size: 123392 Total Image Size: 7598592 Image Feature: WIRELESS LAN|LWAPP Image Family: AP3G1 Wireless Switch Management Version: 7.4.1.37 Extracting files... ap3g1-rcvk9w8-mx/ (directory) 0 (bytes) extracting ap3g1-rcvk9w8-mx/ap3g1-rcvk9w8-mx (113080 bytes)........................ extracting ap3g1-rcvk9w8-mx/ap3g1-boot-m_upg (393216 bytes)..................................................................................... extracting ap3g1-rcvk9w8-mx/u-boot.bin (393216 bytes)..................................................................................... extracting ap3g1-rcvk9w8-mx/ap3g1-rcvk9w8-xx (6686892 bytes)...
Now your AP is back in Lightweight mode & it is ready to register for a WLC.
APccef.4872.0fb5#sh ver Cisco IOS Software, C3500 Software (AP3G1-RCVK9W8-M), Version 15.2(2)JB, RELEASE SOFTWARE (fc1) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2012 by Cisco Systems, Inc. Compiled Mon 10-Dec-12 23:48 by prod_rel_team ROM: Bootstrap program is C3500 boot loader BOOTLDR: C3500 Boot Loader (AP3G1-BOOT-M), Version 12.4 [mpleso-ap_jmr3_esc_0514 125] Networks-ISE-Test uptime is 0 minutes System returned to ROM by reload System image file is "flash:/ap3g1-rcvk9w8-mx/ap3g1-rcvk9w8-xx" Last reload reason:
Here are some of reference document you should read.

Once again nice post.
Some months ago I tried to do the same operation and I encountered several problems, the biggest one came from the tftp server.
I learned that some of them do not answer to broadcast requests. It can be configurable in some servers but on others it simply not supported. And guest what, in this situation the AP’s request for a tftp server is a broadcast.
For this specific need I couldn’t try the tftp server in WCS/NCS/CPI because of the numbering plan. I didn’t want to change the ip address of WCS/NCS/CPI server.
So guys, be aware that you can’t do this operation with all tftp servers.
HTH
Hi
Thanks for that feedback.. it is very useful
I used tftpd32 as TFTP server & PC is directly connected to AP. That should works everytime 🙂
Rasika
Hi Guys, I’m new to all of this. IS there a way to do this and reset the password with a MAC on a home network?
If you reset, it will reset all configuration of your AP. So unless you have configuration backup you will not able to setup home wireless again.
MAC should be fine
HTH
Rasika
Rasika, Your posts are very useful to me! Thank you very much!. I have a question about the default mode of the serie 2600, What is the default mode? CAPWAP or Autonomous? And when I configure the first time, can I register on the controller or configure autonomous? or I need to convert? Many Thanks!
Hi Thiago,
If you ordering these fresh from Cisco, then depend on the part number we can tell. SAP-S for standalone or Autonomous, CAP – C for CAPWAP or Lightweight
AIR-CAP2602I-x-K9
AIR-SAP2602I-x-K9
If a AP already being used, that can be converted in the past eitherway. Only way to verify is power up the AP & see show version. If image comewith k9w7 that indicate an autonomous image. if it is k9w8 then it is lightweight.
If it has lightweight image, then you require a WLC. If it has autonomous image you can configure it normally (ie conf t, etc)
HTH
Rasika
Thank you very much! About the Cisco tools like “Autonomous To Lightweight Mode Upgrade Tool” and “IP Setup Utility (IPSU)”, these are a facility or I need to use it on oldest AP model?
I have not used these tool & do not have first hand information. If your AP does not have mode button, you cannot use the method I describe in this post.
I think for those it may useful.
HTH
Rasika
Rasika, Your posts are very useful to me! Thank you very much!. I have a question about the default mode of the serie 2600, What is the default mode? CAPWAP or Autonomous? And when I configure the first time, can I register on the controller or configure autonomous? or I need to ? Thanks!
Great tutorial 🙂 Thanks 🙂
Thanks for the feedback…
Hi Rasika
I am facing problem with the 3602i AP registration with the vWLC, both are in same subnet. The AP is keep sending messages and not allowing me to enter anything in AP console. How can I enter command in the AP console? Please help.
Hi there,
I followed your directions above but am running into the same issue! I set a static IP on my machine 10.0.0.2/8 and connected the AP directly to my laptop using an Ethernet cable. I reset the power and while holding in the mode button till the status light went red(30 secs)…i get the following:
button pressed for 20 seconds
process_config_recovery: set IP address and config to default 10.0.0.1
process_config_recovery: image recovery
image_recovery: Download default IOS tar image tftp://255.255.255.255/c1240-k9w7-tar.default
examining image…tftp://255.255.255.255/c1240-k9w7-tar.default: no such file or directory
ERROR: Failed to open archive file tftp://255.255.255.255/c1240-k9w7-tar.default
Loading “flash:/c1240-rcvk9w8-mx/c1240-rcvk9w8-mx”…#
Looking at the output it is looking at 255.255.255.255 for the image. I have two images under C:\TFTP-Root…c1240-k9w7-tar.default and c1240-k9w7-mx.124-10b.JA.
I have tried Solar winds which I read somewhere didn’t work(I used this to copy an image form another AP). So i tried TFTP32 and still didn’t work. Below is the log from TFTP32
Connection received from 10.0.0.3 on port 56931 [12/03 15:18:46.651]
Read request for file . Mode octet [12/03 15:18:46.652]
File : error 2 in system call CreateFile The system cannot find the file specified. [12/03 15:18:46.654]
Am i missing something else here! Thanks in advance!
Sorry for late response. Have you managed to get this working ?
As long as you set TFTP directory on your tftp32 application correct & you have the correct image “c1240-k9w7-tar.default” in that folder this should work.
HTH
Rasika
Hi. I have configured both AP and PC on the same subnet but still cannot ping the AP. I am using PoE switch to connect both. The image has been renamed and I still get the error message:
process_config_recovery: set IP address and config to default 10.0.0.1
process_config_recovery: image recovery
image_recovery: Download default IOS tar image tftp://255.255.255.255/ap3g2-k9w7
-tar.default
examining image…
DPAA Set for Independent Mode
DPAA_INIT = 0x0
%Error opening tftp://255.255.255.255/ap3g2-k9w7-tar.default (connection timed o
ut)ap:
What can I do?
I fought this exact issue with the same symptoms & output at the console.
AP: C2702i File: ap3g2-k9w7-tar.153-3.JAB.tar –> (renamed to ap3g2-k9w7-tar.default)
I was using tftpd64 on a Win 8.1 Pro machine and the AP would not take the image from the directory, although I could see in the tftpd64 logs that the AP was connecting and trying to initialize the transfer nd then ‘connection timed out’ message every time. I disabled AV & windows firewall with no luck and finally gave up after an hour of trying different things – thinking that maybe I had a corrupt image or something…
*The next day I decided to try the process again from a different computer (tftpd32 on Win 7 Pro) – it worked on the first attempt and performed the conversion to Autonomous successfully !!!
*I still haven’t figured out what the issue was on the first machine.
Thanks for your experience with windows 8, may be useful to others
Rasika
me also got same error when i am using windows 8 then i tried with windows 7 it works!!!! Thanks a lot..
You have to turn off Windows firewall or create an exception
Be sure that your firewall (windows) allows UDP port 69 INCOMING..
That was MY problem all along…
Missing the 2700 series files? 🙂
Yes, post was done prior to this model release 🙂
I’ll see to update the post with that information
Rasika
I used this today on a 2602e, worked great, thank you!!
Glad to hear that Robert…
Rasika
Hello, in case it can help somebody, we were trying already one week to upload an image on AP 2600 and it randpmly failed. It was powered throught ethernet. We then switched for the external power connector and the upload were systematically successfull.
Thanks for that update as it may useful to others doing the same.
Will this work with the 2602E with version 8 of code? Thank you
should work, I haven’t try that as I do not have specific AP model.
HTH
Rasika
Conversion to auto works perfectly as you described for 3502i but AP does not have A/b/g bands, works only in N band. Something missing in ap3g1-k9w7-152-2.jb file or a configuration step?
Cisco implemented 802.11n mixed mode support where 802.11n has to support 802.11a in 5GHz & 802.11b/g in 2.4GHz band.
So if you try to connect non 802.11n client you will see them connect to your wireless
HTH
Rasika
using 1250 series AP’s & the ones received are in lightweight mode. Any suggestions on where i could get the FW download to get them into Autonomous? Do not have active contract with Cisco.
Hi Mike,
You need to have valid support contract to download Autonomous image from cisco
HTH
Rasika
Thanks Navarasi for the answer. Let me explain what happens. I have turned on both 2.4GHz and 5GHz radio channels on 3502i in autonomous mode and assigned them SSDI. However, my galaxy S2 phone (old by today’s technology) will not find this WiFi but a tablet would connect and work fine. Tablet was bought this month and therefore does have N support. Phone does connect to Linksys and D-link 2.4GHz Wifi routers fine just not to 3502i. Therefore, I thought a/b/g bands are some how not active in the autonomous mode in 3502i. Any ideas?
Excellent Guide Save my day….Thanks
Thanks Ansari
THANK YOU THANK YOU THANK YOU!!!!!!!
Thanks Joe
Hi,
I have installed image ap3g2-k9w7-tar.default on my AP and in boot sequence this shows me the same image but when I reload the AP, It doesn’t come up with new image but it boots up with the same old image. Anything I can do here?
Thanks,
Kedar
Hi
On the console output, did it show that given image is loading ?
Are you trying to convert from lightweigh to autonomous ?
You can try the other method given at the start of the post.
Rasika
I have converted a 1532 AP to Autonomous mode and running it as a Client, however I am only able to get the 2.4ghz radio working? If I configure the dot11radio 1 when I try to connect the AP just says cannot associate no response? Any ideas?
Thanks
Roger
Try different version of software & see problem persist
Rasika
Hi,
Thank you very much……its very useful…..
Thanks for the feedback 🙂
I used image file ap3g2-k9w7-tar.153-3.JAB.tar for converting a 2702E model. Simply followed your words and worked perfect. Thanks a lot.
Do you still having this issue ?
image_recovery: Download default IOS tar image tftp://255.255.255.255/c1140-k9w7
-tar.default
examining image…
%Error opening tftp://255.255.255.255/c1140-k9w7-tar.default (connection timed o
ut)
ap:
not able to load IOS on AP, im trying to convert LAP to AP
I was doing everything correctly and kept getting the same ftfp timeout message. Tried a different laptop (also Windows 7) and it worked on the first try.
May be local firewall issue of the first machine.
Anyway good to see you got it working with a different PC
Rasika
Had the same issue with windows 10, ran the tftp server as admin and it worked on a win 10 system.
Thanks! running TFTPD as admin in Windows 10 did the trick!
Hi,
I followed your suggestion and it took the file, but I’m having troubles connecting with console. Shall I change the console default boud speed from 9600?
Or is there any other way to connect to it?
Thanks
Does this console cable work with any other cisco devices (eg. router/switch). check that first
HTH
Rasika
Thank you for posting this. Is there a way that you can send a link or the actual iOS? All I am able to find is ap3g1-k9w7-tar.124-25d.JA2, not ap3g1-k9w7-tar.124-25d.JA. Thank you for your time.
Hi
You need to have support contract with Cisco to download these autonomous images.
Otherwise approarch your local Cisco partner & see how they can help
HTH
Rasika
translate with google translator
Hello
no need to have a contract with cisco to download the software
There are several pages on the internet where you can download freely and freely
I have done it and it works perfectly
Here I leave you one of the many pages where you can download this specific software
https://www.techeia.com/2016/11/cisco-firmware-and-manual-downloads.html
and to download other softwares there are also pages on the internet to download free
you just have to look
Hi,
Does this Tutorial can be used for AIR CAP 1602I-E-K9 ?
If not, how can i convert AIR CAP 1602I-E-K9 to autonomous mode ?
Thanks in advance
Yes, this should applicable for that model as well.
Hello Rasika,
I have a small doubt. Can I use this cisco 3700 as a standalone AP without a controller?
Yes, you can. You need to buy it with Autonomous image (..k9w7… ).
If you have it with lightweight image, then you need to convert it to Autonomous to use it as Standalone.
HTH
Rasika
thanks man. I saw in forum that AP will have only limited functionality if we convert it to Autonomous. Is it so?
No, it has full features 🙂
awesome !
that answers all my queries
thanks alot man
Hola tengo un problema,
ap: tar -xtract tftp://10.0.0.8/ap3g1-k9w8-mx.153-3.JBB6 flash:
“Tar checksum error in df 0”
¿como puedo solucionar este error?
Pls translate this to english 🙂
Thank you very much for your tutorial, everything works properly.I’ve lost three days searching for solutions .
Good to hear that…
Hello nayarasi. Thank you very much for the detailed article. But there is one very important addition, because of which I lost a lot of time. AP must be connected without the use of PoE. Otherwise, it does not see the TFTP. This is important, do not use the Power over Ethernet at conversion.
No Problems converting a PoE attached AP here….
Nice and really easy guide. Everything working here. Great work. Thank you.
Thanks Peter for feedback. Good to hear that it is easy to follow.
Dear,
i have AIR-CAP–1702i-E-K9 ACCESSPOINT, I tried to make console, but not getting connected, also i tried like the above post, also no result. Anybody have any solution to convert the default mode to Autonoumus?
Hello, thanks for the good post.
I tried to power the AP with PoE from a cisco 3650 with PoE, and then plugged in my computer to another port in the same switch and i configured static ip on the computer as shown in the guide.
The switch is basically unconfigured (no vlans or anything) and it did not seem to work, I only got timeout from the AP cli and nothing popped up in the tftp-server.
I really dont know why it didnt work, I checked firewall settings and such, but then later I tried without PoE, using power injector instead and connected the AP directly to my computer, and it worked directly.
Really strange behaviour, I did this scenario on two different switches as well. Too bad I dont have my power injector at home now, so at the moment I cannot recover my AP…
Any suggestions why this shouldnt work with a switch in between? I mean they are on the same L2-domain..
Cheers
John
It worked for me int the past, have you statically change PC ip range for 10.0.0.0/8 ?
First of all, great post!
When I try to do this with the AP powered by PoE, and my computer plugged in to another port on the same switch, it does not seem to be working, I get timeout from the tftp server. The switch is basically unconfigured and is a cisco 2960 with no vlans and such. I have turned off the firewall on the computer as well. When I tried to power the AP from a power injector and connected it directly to the computer, it worked like a charm directly.
This is for me really strange, since they are on the same L2-domain when they are plugged in to the switch. Any suggestions why it does not work with this setup? unfortenatly I dont have a power injector at hand at home, so I cannot fix this at the moment.
Regards
Hi ! I am trying to download the IOS from the tftp server that is my Pc to the access point but it is not working,even though I followed the steps…Please help!
I had the same issue and changed the laptop. Installed TFTP on a different system and then iwas able to connect.
Dear Nayarasi, I’ve come across your blog from Google. and it’s awesome. Very informative yet simple writing I must say. I’ll definitely share your site address among my colleges.
I am into a problem, I got an AP which was stuck in ap: mode due to corrupt IOS. I tried loading the ios using xmodem.
Then for purpose of speeding up the process, I set baud to 115200 using command set BAUD 115200.
After that I lost console response,I closed putty and reconnected with baud 115200 but got no output. Later I restarted AP while reconnected putty at 9600 baud, I got few boot messages but as soon as it comes to ap: mode, none of the keyboard buttons are working, when I press enter, it just inserts garbage character.
Model- 1142 LWAP. And I got one error message- system unable to boot properly as there is not bootable image.
My question is that, how can communicate on present BAUD 115200 and/or how can I reset BAUD to 9600?
I just received this new Cisco 2602i AP and cannot figure out how to configure it due to not being able to enter configure terminal mode. I tried to download the autonomous image file but cannot because we don’t have a contract agreement with Cisco. Is there anything else I can do to get this AP up and running?
Any help would be appreciated!
Here is my complete #show run configurations (default configs out of the box):
AP78da.6e85.0871#
AP78da.6e85.0871#sho run
Building configuration…
Current configuration : 17224 bytes
!
! Last configuration change at 00:00:32 UTC Mon Mar 1 1993
version 15.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname AP78da.6e85.0871
!
!
logging rate-limit console 9
enable secret 5 $1$760J$unIE6O2NWpaiZo1zMAu8Y1
!
aaa new-model
!
!
aaa authentication login default local
!
!
!
!
!
aaa session-id common
ip cef
!
!
!
!
power inline negotiation prestandard source
!
crypto pki trustpoint airespace-old-root-cert
revocation-check none
rsakeypair Cisco_IOS_MIC_Keys
!
crypto pki trustpoint airespace-new-root-cert
revocation-check none
rsakeypair Cisco_IOS_MIC_Keys
!
crypto pki trustpoint airespace-device-root-cert
revocation-check none
rsakeypair Cisco_IOS_MIC_Keys
!
crypto pki trustpoint cisco-root-cert
revocation-check none
rsakeypair Cisco_IOS_MIC_Keys
!
crypto pki trustpoint Cisco_IOS_MIC_cert
revocation-check none
rsakeypair Cisco_IOS_MIC_Keys
!
!
crypto pki certificate chain airespace-old-root-cert
certificate ca 00
30820406 3082032F A0030201 02020100 300D0609 2A864886 F70D0101 04050030
818F310B 30090603 55040613 02555331 13301106 03550408 130A4361 6C69666F
726E6961 3111300F 06035504 07130853 616E204A 6F736531 16301406 0355040A
130D6169 72657370 61636520 496E6331 0D300B06 0355040B 13046E6F 6E65310B
–More—
30090603 55040313 02636131 24302206 092A8648 86F70D01 09011615 73757070
6F727440 61697265 73706163 652E636F 6D301E17 0D303330 32313232 33333835
–More–
*Mar 1 00:15:02.531: %CAPWAP-3-DHCP_RENEW: Could not discover WLC using DHCP IP. Renewin 355A170D 31323131 31313233 33383535 5A30818F 310B3009 06035504 06130255
53311330 11060355 0408130A 43616C69 666F726E 69613111 300F0603 55040713
0853616E 204A6F73 65311630 14060355 040A130D 61697265 73706163 6520496E
63310D30 0B060355 040B1304 6E6F6E65 310B3009 06035504 03130263 61312430
2206092A 864886F7 0D010901 16157375 70706F72 74406169 72657370 6163652E
636F6D30 81DF300D 06092A86 4886F70D 01010105 000381CD 003081C9 0281C100
DB9D3901 30059DD1 05CB2793 9B9907F8 1FF57FA9 24065BF7 1A5865F8 B9CFCCB3
679354D4 69BAB847 1CA327AE EA006AAC 90479C9D C23B67DE FACC0D28 32C6103F
A59C41E2 E8B4250B 4D2903EB 52629A99 D618B747 C4A94151 1AB995BB 14905404
5F4A0B9F F387F346 D5F3A249 2AED1B6A 3DD639D8 4924366A 1234DD2D B13CD489
7E2EA101 63BCCC82 2F7A6D0B 33AB5705 3C784A6D A3DD1E5B 96CF54C6 CF4D59BC
1BFD6CB6 E72FCB29 88DCBE6D 4D76FB83 1FAF5683 E4E20822 00A9EB2E 3BEF0DF9
02030100 01A381EF 3081EC30 1D060355 1D0E0416 04149457 DF7D1482 2D31BB28
772E8996 1886DA46 84BA3081 BC060355 1D230481 B43081B1 80149457 DF7D1482
2D31BB28 772E8996 1886DA46 84BAA181 95A48192 30818F31 0B300906 03550406
13025553 31133011 06035504 08130A43 616C6966 6F726E69 61311130 0F060355
04071308 53616E20 4A6F7365 31163014 06035504 0A130D61 69726573 70616365
20496E63 310D300B 06035504 0B13046E 6F6E6531 0B300906 03550403 13026361
31243022 06092A86 4886F70D 01090116 15737570 706F7274 40616972 65737061
63652E63 6F6D8201 00300C06 03551D13 04053003 0101FF30 0D06092A 864886F7
0D010104 05000381 C100AEB0 349DC0F9 2AAA3A57 75B3A79C 5421A9D0 15389261
95C03479 04DA81D4 120F58FA E2299223 BEB54A90 6D70F7F7 2192EFAF A4B0F488
604E3094 BBCC77A3 60A88129 0849B87B 5CA1AA17 21922A55 6B68E0D3 1ADC7264
C4C4D6B2 33345C86 254E4988 096645CD 40F12761 8BC37E71 DAD91677 25322361
71D87A16 F92AF7C1 51CB8892 443BC666 59BEA47B 985E8866 68A1EBD4 88BBF6E7
A949FDF8 7711D518 A80E203D A12BEBDC 6963EDA7 B76079A3 22380C96 0CB8D324
CADD949D EA39E0EF 033D
quit
crypto pki certificate chain airespace-new-root-cert
certificate ca 00
3082045A 30820383 A0030201 02020100 300D0609 2A864886 F70D0101 04050030
81A6310B 30090603 55040613 02555331 13301106 03550408 130A4361 6C69666F
726E6961 3111300F 06035504 07130853 616E204A 6F736531 17301506 0355040A
130E4169 72657370 61636520 496E632E 31143012 06035504 0B130B45 6E67696E
65657269 6E67311A 30180603 55040313 11416972 65737061 63652052 6F6F7420
43413124 30220609 2A864886 F70D0109 01161573 7570706F 72744061 69726573
70616365 2E636F6D 301E170D 30333037 33313133 34313232 5A170D31 33303432
39313334 3132325A 3081A631 0B300906 03550406 13025553 31133011 06035504
08130A43 616C6966 6F726E69 61311130 0F060355 04071308 53616E20 4A6F7365
31173015 06035504 0A130E41 69726573 70616365 20496E63 2E311430 12060355
040B130B 456E6769 6E656572 696E6731 1A301806 03550403 13114169 72657370
61636520 526F6F74 20434131 24302206 092A8648 86F70D01 09011615 73757070
6F727440 61697265 73706163 652E636F 6D3081DF 300D0609 2A864886 F70D0101
01050003 81CD0030 81C90281 C100CCA0 F92330BD 49E947A4 3FA2ACF3 A4827F66
77BB66F4 6B1636BA 84EF0966 9CCAE0EA CA6F1D0F BA90FEFA 58B8502C 10FC78DC
C9D126D8 8F2AD059 A8A69BFE 90324BD6 4553CED9 131B99B0 282A73D9 8655EFAF
–More—
5EA54096 22E54B9F C4258988 78F1A51F F47B16F2 0C0A37A3 52603A5A B0DC4533
B0C0B7C8 02DF25F0 585DFF5F 43FDAE1F 48A34BDF F80AC27E 30BE931B D3490ADE
C81FF6F9 974F1408 55C8813F D334F1B8 A1892B0A 10D98A44 7DBF213E 64520D20
E78E9322 DA11CA7A 46ACEB41 46AB0203 010001A3 82011430 82011030 1D060355
1D0E0416 0414538D 8360478D C20F8066 3232E9E1 7070552B 17EA3081 D3060355
1D230481 CB3081C8 8014538D 8360478D C20F8066 3232E9E1 7070552B 17EAA181
ACA481A9 3081A631 0B300906 03550406 13025553 31133011 06035504 08130A43
616C6966 6F726E69 61311130 0F060355 04071308 53616E20 4A6F7365 31173015
06035504 0A130E41 69726573 70616365 20496E63 2E311430 12060355 040B130B
456E6769 6E656572 696E6731 1A301806 03550403 13114169 72657370 61636520
526F6F74 20434131 24302206 092A8648 86F70D01 09011615 73757070 6F727440
61697265 73706163 652E636F 6D820100 300C0603 551D1304 05300301 01FF300B
0603551D 0F040403 02010630 0D06092A 864886F7 0D010104 05000381 C10006E3
653D4B19 FAA0C3B9 8EAE23C5 A3305E42 4522A961 BE1B5B88 56ED2E5A E42F7AC0
26AA2805 9824080D 1512169B 44E42847 2EBBA573 29F070DB 56011C7B E9F3A240
399A3557 A50384EC A0353DCF 49E8EC01 94047469 0BC12079 2764873D 25943DCD
66A9726F 4A79EB40 1C7C6897 4E925D80 2313C126 1F604763 A9D9AC1F DF0092F6
57DF1AB4 9B904E22 CE5515CD 44F68A00 4E2BC861 FBC1540D C1F3A66B 8CDDC1C2
7C442027 E6241198 B0E002DE 9E06D64F 0D538987 96C1C0DB 12B0F581 6FED
quit
crypto pki certificate chain airespace-device-root-cert
certificate ca 03
3082047F 308203A8 A0030201 02020103 300D0609 2A864886 F70D0101 04050030
81A6310B 30090603 55040613 02555331 13301106 03550408 130A4361 6C69666F
726E6961 3111300F 06035504 07130853 616E204A 6F736531 17301506 0355040A
130E4169 72657370 61636520 496E632E 31143012 06035504 0B130B45 6E67696E
65657269 6E67311A 30180603 55040313 11416972 65737061 63652052 6F6F7420
43413124 30220609 2A864886 F70D0109 01161573 7570706F 72744061 69726573
70616365 2E636F6D 301E170D 30353034 32383232 33373133 5A170D31 35303132
36323233 3731335A 3081A831 0B300906 03550406 13025553 31133011 06035504
08130A43 616C6966 6F726E69 61311130 0F060355 04071308 53616E20 4A6F7365
31173015 06035504 0A130E41 69726573 70616365 20496E63 2E311430 12060355
040B130B 456E6769 6E656572 696E6731 1C301A06 03550403 13134169 72657370
61636520 44657669 63652043 41312430 2206092A 864886F7 0D010901 16157375
70706F72 74406169 72657370 6163652E 636F6D30 81DF300D 06092A86 4886F70D
01010105 000381CD 003081C9 0281C100 A93C0158 E7284E75 FF86A57A 886ACA37
430BECF0 7582F56B DB6AC514 554FB06E AA327B3E CE3C9391 03C93BA4 0C0AF932
A6CB5DA3 F1C3C528 53BF4E19 2C1BFC48 467EBD93 06B4974A 1273BF35 8AD8540F
261E612B A2673B68 D239C87E 1E9E967B 2654D285 45BB7F78 5F4E9D4B 7B8001AA
2F455CFF 4552ECDB 5667E3FC E7093E06 8FAE353D 4228B48D 8B415D9B F496342D
C1459987 B69BFA4B 51FB67B4 A0C21E7F C6269A39 47EB1D48 5E83B129 8B079E5E
1EDAB5A0 BE5E1DE0 109FF0BD 4750E32B 02030100 01A38201 37308201 33300C06
03551D13 04053003 0101FF30 2E060960 86480186 F842010D 0421161F 41697265
73706163 65204465 76696365 20434120 43657274 69666963 61746530 1D060355
1D0E0416 04140A52 3BB12570 523B9CEA 747FB2AD 3D8F95EA 3FCC3081 D3060355
1D230481 CB3081C8 8014538D 8360478D C20F8066 3232E9E1 7070552B 17EAA181
ACA481A9 3081A631 0B300906 03550406 13025553 31133011 06035504 08130A43
616C6966 6F726E69 61311130 0F060355 04071308 53616E20 4A6F7365 31173015
06035504 0A130E41 69726573 70616365 20496E63 2E311430 12060355 040B130B
456E6769 6E656572 696E6731 1A301806 03550403 13114169 72657370 61636520
526F6F74 20434131 24302206 092A8648 86F70D01 09011615 73757070 6F727440
61697265 73706163 652E636F 6D820100 300D0609 2A864886 F70D0101 04050003
81C100A0 E8D59D9B DA9EED0C 96045DFE A37084EC 59B5C3D3 71694DB0 70664E0C
8060D69E E366E81F 9F3CCF68 8AB0498E CCFA6CA7 2854F2D8 046690C9 8FEC84EF
2F7F0F08 C90F719D C0F4C125 CED1B525 6DD93E51 777BD5E8 7F1DC79F CC502DC2
0242C05D 1682DEE3 DF7541B8 C55B433C 10DFE2BF D2E802E7 D923329A 23A2076F
86BCC048 D569B383 59AC8979 97F02C55 6F8FE318 754F605C 43CDA7C8 1847B085
1DADF0D6 CD62C8DE A86E6E12 4A7CDCBF A6FCC7E1 852A1DB1 529D63B3 688305F6 7BD25F
quit
crypto pki certificate chain cisco-root-cert
certificate ca 5FF87B282B54DC8D42A315B568C9ADFF
30820343 3082022B A0030201 0202105F F87B282B 54DC8D42 A315B568 C9ADFF30
0D06092A 864886F7 0D010105 05003035 31163014 06035504 0A130D43 6973636F
20537973 74656D73 311B3019 06035504 03131243 6973636F 20526F6F 74204341
20323034 38301E17 0D303430 35313432 30313731 325A170D 32393035 31343230
–More—
1B301906 03550403 13124369 73636F20 526F6F74 20434120 32303438 30820120
300D0609 2A864886 F70D0101 01050003 82010D00 30820108 02820101 00B09AB9
ABA7AF0A 77A7E271 B6B46662 94788847 C6625584 4032BFC0 AB2EA51C 71D6BC6E
7BA8AABA 6ED21588 48459DA2 FC83D0CC B98CE026 68704A78 DF21179E F46105C9
15C8CF16 DA356189 9443A884 A8319878 9BB94E6F 2C53126C CD1DAD2B 24BB31C4
2BFF8344 6FB63D24 7709EABF 2AA81F6A 56F6200F 11549781 75A725CE 596A8265
EFB7EAE7 E28D758B 6EF2DD4F A65E629C CF100A64 D04E6DCE 2BCC5BF5 60A52747
8D69F47F CE1B70DE 701B20D6 6ECDA601 A83C12D2 A93FA06B 5EBB8E20 8B7A91E3
B568EEA0 E7C40174 A8530B2B 4A9A0F65 120E824D 8E63FDEF EB9B1ADB 53A61360
AFC27DD7 C76C1725 D473FB47 64508180 944CE1BF AE4B1CDF 92ED2E05 DF020103
A351304F 300B0603 551D0F04 04030201 86300F06 03551D13 0101FF04 05300301
01FF301D 0603551D 0E041604 1427F3C8 151E6E9A 020916AD 2BA08960 5FDA7B2F
AA301006 092B0601 04018237 15010403 02010030 0D06092A 864886F7 0D010105
05000382 0101009D 9D8484A3 41A97C77 0CB753CA 4E445062 EF547CD3 75171CE8
E0C6484B B6FE4C3A 198156B0 56EE1996 62AA5AA3 64C1F64E 5433C677 FEC51CBA
E55D25CA F5F0939A 83112EE6 CBF87445 FEE705B8 ABE7DFCB 4BE13784 DAB98B97
701EF0E2 8BD7B0D8 0E9DB169 D62A917B A9494F7E E68E95D8 83273CD5 68490ED4
9DF62EEB A7BEEB30 A4AC1F44 FC95AB33 06FB7D60 0ADEB48A 63B09CA9 F2A4B953
0187D068 A4277FAB FFE9FAC9 40388867 B439C684 6F57C953 DBBA8EEE C043B2F8
09836EFF 66CF3EEF 17B35818 2509345E E3CBD614 B6ECF292 6F74E42F 812AD592
91E0E097 3C326805 854BD1F7 57E2521D 931A549F 0570C04A 71601E43 0B601EFE
A3CE8119 E10B35
quit
crypto pki certificate chain Cisco_IOS_MIC_cert
certificate 73AC3C170000000F7E04
30820470 30820358 A0030201 02020A73 AC3C1700 00000F7E 04300D06 092A8648
86F70D01 01050500 30393116 30140603 55040A13 0D436973 636F2053 79737465
6D73311F 301D0603 55040313 16436973 636F204D 616E7566 61637475 72696E67
20434130 1E170D31 33313130 31323135 3134315A 170D3233 31313031 32323031
34315A30 818C310B 30090603 55040613 02555331 13301106 03550408 130A4361
6C69666F 726E6961 3111300F 06035504 07130853 616E204A 6F736531 16301406
0355040A 130D4369 73636F20 53797374 656D7331 1B301906 03550403 13124150
3347322D 37386461 36653835 30383731 3120301E 06092A86 4886F70D 01090116
11737570 706F7274 40636973 636F2E63 6F6D3082 0122300D 06092A86 4886F70D
01010105 00038201 0F003082 010A0282 010100CC FCA23E8A 86638A6D 2903C89F
D076ACDE C10A9DE5 9B93AE15 6404AA9A 87200829 E9FE383F AD55A902 1D74C88A
787E6A33 E9D96A76 B414D4F9 0E3C5B9C 09CC348A E78187A2 CCE5F8EC 502A2824
337838F2 3E284296 3A204244 A5DF0D06 9AA04353 3D8395A3 059A3C5A 4B83D50F
CA268A69 8BBD2C47 4BCFC5CB 0CEFA43A BBD7260E 9475BC5E B8DD4543 3E6647A8
68B7437B 9DE52711 D79BF2E1 268357BB 98ED01F8 A31E749A C43E044D C63C4E41
87FDD8E0 5AC5D9B2 36CE3A28 7A2248BD 8B1DF1B5 4540DE09 687E9F0D D3DA81D8
6589D8D4 FD206D62 152AFE0E C156F98F 9792E1CA 5E25AE0A 0FD4FCD5 D2925BF4
3AEB7BAB D9C8D17E 4D05916F BA856B7C 78BE7902 03010001 A3820124 30820120
300E0603 551D0F01 01FF0404 030205A0 301D0603 551D0E04 160414B3 F63DBAD7
5D32B30F 3E8A5598 61A02923 FCCDF730 1F060355 1D230418 30168014 D0C52226
AB4F4660 ECAE0591 C7DC5AD1 B047F76C 303F0603 551D1F04 38303630 34A032A0
30862E68 7474703A 2F2F7777 772E6369 73636F2E 636F6D2F 73656375 72697479
2F706B69 2F63726C 2F636D63 612E6372 6C304C06 082B0601 05050701 01044030
3E303C06 082B0601 05050730 02863068 7474703A 2F2F7777 772E6369 73636F2E
636F6D2F 73656375 72697479 2F706B69 2F636572 74732F63 6D63612E 63657230
3F06092B 06010401 82371402 04321E30 00490050 00530045 00430049 006E0074
00650072 006D0065 00640069 00610074 0065004F 00660066 006C0069 006E0065
300D0609 2A864886 F70D0101 05050003 82010100 9CA023D0 6D2CEA43 DB421E30
0734D567 EE375BA3 6B0A51F7 5EABB9C7 D00BFB65 B4A21136 6260B460 1C0A1AE2
56A52132 3B4D19F8 2DCEC2E2 5F6B2AD3 5F50B1B0 BFC4A4F9 7824F98F 9FEE3215
C42F99CF A83A2D33 25D82C53 A0473FC2 F67A23C4 9726A851 0DA91227 C495B1C7
CA040F87 6B0C9064 6B8F03B1 95DBF6F9 FD64F929 82D372AB D8491D3E 23347101
C77FE2E6 94E110B1 9A9F20D0 39D0CD19 8C30BC7F 99FCEBE4 4F594D4F 3304F121
75593ACC AE5C30DF DCE382CA 281D6329 2485A841 5B80F7C1 5B08FB29 8959C14C
DDDE710C B9B5C28D 533B790B B29C2482 FB7C59E5 7D070E50 FD40D287 6B9D7007
D9E60E15 6CC6E241 841E4CE4 E4BFBF29 F696307A
quit
certificate ca 6A6967B3000000000003
–More—
86F70D01 01050500 30353116 30140603 55040A13 0D436973 636F2053 79737465
6D73311B 30190603 55040313 12436973 636F2052 6F6F7420 43412032 30343830
1E170D30 35303631 30323231 3630315A 170D3239 30353134 32303235 34325A30
39311630 14060355 040A130D 43697363 6F205379 7374656D 73311F30 1D060355
04031316 43697363 6F204D61 6E756661 63747572 696E6720 43413082 0120300D
06092A86 4886F70D 01010105 00038201 0D003082 01080282 010100A0 C5F7DC96
943515F1 F4994EBB 9B41E17D DB791691 BBF354F2 414A9432 6262C923 F79AE7BB
9B79E807 294E30F5 AE1BC521 5646B0F8 F4E68E81 B816CCA8 9B85D242 81DB7CCB
94A91161 121C5CEA 33201C9A 16A77DDB 99066AE2 36AFECF8 0AFF9867 07F430EE
A5F8881A AAE8C73C 1CCEEE48 FDCD5C37 F186939E 3D71757D 34EE4B14 A9C0297B
0510EF87 9E693130 F548363F D8ABCE15 E2E8589F 3E627104 8726A415 620125AA
D5DFC9C9 5BB8C9A1 077BBE68 92939320 A86CBD15 75D3445D 454BECA8 DA60C7D8
C8D5C8ED 41E1F55F 578E5332 9349D5D9 0FF836AA 07C43241 C5A7AF1D 19FFF673
99395A73 67621334 0D1F5E95 70526417 06EC535C 5CDB6AEA 35004102 0103A382
01E73082 01E33012 0603551D 130101FF 04083006 0101FF02 0100301D 0603551D
0E041604 14D0C522 26AB4F46 60ECAE05 91C7DC5A D1B047F7 6C300B06 03551D0F
04040302 01863010 06092B06 01040182 37150104 03020100 30190609 2B060104
01823714 02040C1E 0A005300 75006200 43004130 1F060355 1D230418 30168014
27F3C815 1E6E9A02 0916AD2B A089605F DA7B2FAA 30430603 551D1F04 3C303A30
38A036A0 34863268 7474703A 2F2F7777 772E6369 73636F2E 636F6D2F 73656375
72697479 2F706B69 2F63726C 2F637263 61323034 382E6372 6C305006 082B0601
05050701 01044430 42304006 082B0601 05050730 02863468 7474703A 2F2F7777
772E6369 73636F2E 636F6D2F 73656375 72697479 2F706B69 2F636572 74732F63
72636132 3034382E 63657230 5C060355 1D200455 30533051 060A2B06 01040109
15010200 30433041 06082B06 01050507 02011635 68747470 3A2F2F77 77772E63
6973636F 2E636F6D 2F736563 75726974 792F706B 692F706F 6C696369 65732F69
6E646578 2E68746D 6C305E06 03551D25 04573055 06082B06 01050507 03010608
2B060105 05070302 06082B06 01050507 03050608 2B060105 05070306 06082B06
01050507 0307060A 2B060104 0182370A 0301060A 2B060104 01823714 02010609
2B060104 01823715 06300D06 092A8648 86F70D01 01050500 03820101 0030F330
2D8CF2CA 374A6499 24290AF2 86AA42D5 23E8A2EA 2B6F6923 7A828E1C 4C09CFA4
4FAB842F 37E96560 D19AC6D8 F30BF5DE D027005C 6F1D91BD D14E5851 1DC9E3F7
38E7D30B D168BE8E 22A54B06 E1E6A4AA 337D1A75 BA26F370 C66100A5 C379265B
A719D193 8DAB9B10 11291FA1 82FDFD3C 4B6E65DC 934505E9 AF336B67 23070686
22DAEBDC 87CF5921 421AE9CF 707588E0 243D5D7D 4E963880 97D56FF0 9B71D8BA
6019A5B0 6186ADDD 6566F6B9 27A2EE2F 619BBAA1 3061FDBE AC3514F9 B82D9706
AFC3EF6D CC3D3CEB 95E981D3 8A5EB6CE FA79A46B D7A25764 C43F4CC9 DBE882EC
0166D410 88A256E5 3C57EDE9 02A84891 6307AB61 264B1A13 9FE4DCDA 5F
quit
username Cisco secret 5 $1$VWCI$4YJtVamYLeh9FlQcqO8MQ.
!
!
bridge irb
!
!
!
interface GigabitEthernet0
duplex auto
speed auto
!
interface GigabitEthernet0.1
encapsulation dot1Q 1 native
bridge-group 1
bridge-group 1 spanning-disabled
!
interface BVI1
ip address dhcp client-id BVI1
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 BVI1
!
bridge 1 protocol ieee
bridge 1 route ip
!
–More—
line vty 0 4
transport input none
line vty 5 15
transport input none
!
end
AP78da.6e85.0871#
Hi Dave,
Do you have WLC to mange this AP ? Usually AP comes with a lightweight image & that require a WLC to manage the AP.
If you do not, then you need to convert this AP to Autonomous mode and given blog post describe how you can do it.
HTH
Rasika
Pingback: Spectrum Analysis Kit | Nolans Wireless Blog
Hi, Is it possible to convert AIR-CAP702W-D-K9 AP to autonomous mode?
If Yes, how and which image should be used?
Regards,
Sachin
Yes, it supports Autonomous.
ap1g1-k9w7-x is what you need. (eg
ap1g1-k9w7-tar.153-3.JD.tar)
HTH
Rasika
Hello, I have an AIR-CAP-2602I-A-K9 and I am trying to make it into an autonomous device. I have the ap3g2-k9w7-tar.153-3.JD.tar file, I renamed it to ap3g2-k9w7-tar.default connected the Ethernet port and the console cable opened teraterm and then unplugged the Ethernet held down the reset and plugged her back in.
I have set my address to 10.0.0.2 255.0.0.0 Gateway 10.0.0.1 this is is what I get
IOS Bootloader – Starting system.
flash is writable
FLASH CHIP: Spansion Mirrorbit (0001)
Xmodem file system is available.
flashfs[0]: 73 files, 9 directories
flashfs[0]: 0 orphaned files, 0 orphaned directories
flashfs[0]: Total bytes: 31997952
flashfs[0]: Bytes used: 20931584
flashfs[0]: Bytes available: 11066368
flashfs[0]: flashfs fsck took 20 seconds.
Reading cookie from SEEPROM
Base Ethernet MAC address: b8:38:61:83:22:6d
Ethernet speed is 1000 Mb – FULL Duplex
button pressed for 25 seconds
process_config_recovery: set IP address and config to default 10.0.0.1
process_config_recovery: image recovery
image_recovery: Download default IOS tar image tftp://255.255.255.255/ap3g2-k9w7-tar.default
examining image…
DPAA Set for Independent Mode
DPAA_INIT = 0x0
%Error opening tftp://255.255.255.255/ap3g2-k9w7-tar.default (permission denied)ap:
I am guessing it is something simple that I am missing any help would be greatly appreciated
Did you get it working ? I would suggest different PC with no firewall enabled.
HTH
Rasika
2 years later, you ever figure out this (permission denied)?
Hi,
first of all Thank you this post.
I changed my AP (AIR -CAP3702I – E-K9) from lightweight to autonomous .
SSID configured I can able to connect my laptop .
AP is connected to ADSL router and both are in same rage. but I am not getting IP address from AP as I think netting part is missing in my configuration. I can access my AP via GUI .
Can you please share the procedure or configuration
Hi Balraj,
Very basically simple configuration like below should do the job. Modify SSID name/password as necessary.
conf t
hostname
!
dot11 ssid
authentication open
authentication key-management wpa version 2
guest-mode
wpa-psk ascii
!
interface Dot11Radio0
encryption mode ciphers aes-ccm
ssid
no shutdown
!
interface Dot11Radio1
channel width 40-above
encryption mode ciphers aes-ccm
ssid
no shutdown
!
interface BVI1
ip address dhcp
!
end
write memory
!
HTH
Rasika
This has been a great help. I used a more round about way to convert AP’s from Autonomous to Lightweight and back again. This has helped with the process 10 fold, thanks!
Glad to hear it Jared 🙂
Rasika
Hello Rasika,
I’m having an issue. the transfer is cancell with the following error “Premature end of tar fileap:”.
I tried to change the timeout and retries in the TFTP server (tftpd32 win 64) and it always fails at different percentage (25%, 34% for example).
what do you recommen?
(I need to convert a CAP2602i from lightweight to Autonomous)
Thanks!
Did you try other method with “debug capwap console cli” & “debug capwap clinet no-reload” options
HTH
Rasika
Tried MANY TIMES to convert a 3602E to Autonomous from Lightweight with ZERO success.
Used the MODE button approach……..sucked@!
timed out using Solar Winds and TFTPD32 using the famous ap3g2-k9w7-tar.default file. All this using several laptops running Windows 10 naked with Firewall/AV
???????????????
I found Windows firewall is worse. I will block TFTP so Dissable windows firewall
i never comment, but i had to say thank you. great how to. thank you.
Thank you Leon
Pingback: Convert AP mode using TFTP and mode button – The dot 11 blog
Thank you for this walkthrough. It worked like a charm for two c1140 a friend of mine had bought from an office.
I had to rename the firmware file to c1140-k9w7-tar.default for his APs.
Good to hear that Ole. Thanks for the feedback
Rasika
Hi. I am not able to fix this problem.
CAP-AIR3702i
Flash is empy!
PC settings IP 10.0.0.2 255.255.255.0
FW disabled
TFTPD32
Image placed ap3g2-k9w7-tar.default in c:\tmp
Set this folder in TFTPD32
Adjust timeout settings to 30sec
Connect straight UTP cable (cat6a) from PC to AP
Used both PoE adapter and power adapter 42v
Rommon mode by mode button IP 10.0.0.1 255.255.255.224
After DPAA_INIT = 0x0 error opening tftp://255.255.255.255/ap3g2-k9w7-tar.default (connection time out)
Have try it on different PC’s with Windows 10 and 7
is there a way to solve this problem?
I have converted my Cisco 2702i AP to autonomous mode, configured DHCP scope for internal network, SSIDs, associated SSIDs to radio interfaces, connected the Xfinity modem to Gig0 interface of the AP.
The AP is broadcasting both SSIDs, I can connect to them, get authenticated, get an IP address from the DHCP pool, DHCP binding confirmed on the AP, but there is no access to the Internet. I also have a default route pointing to the BVI1 interface.
DHCP scope has DNS server set to 8.8.8.8 (tried 1.1.1.1) .
The Xfinity modem is handing out the public IP address to the inside network, which means I’ll have to NAT my RFC1918 to the interface for return traffic, but there is no NAT option and I really don’t want to introduce a router just for NATing purposes in my home network.
So the questions are:
– Can I connect AP directly to Xfinity modem without a router?
– If so, what am I missing from configs below?
hostname 2702i-M
!
no ip domain lookup
no ip dhcp conflict logging
ip dhcp excluded-address 192.168.100.1 192.168.100.100
!
ip dhcp pool 1142Shneider-AVE
network 192.168.100.0 255.255.255.0
default-router 192.168.100.1
dns-server 8.8.8.8
!
!
dot11 ssid DampaliVashli
authentication open
authentication key-management wpa version 2
guest-mode
wpa-psk ascii [PSK]
!
dot11 ssid DampaliVashli2
authentication open
authentication key-management wpa
guest-mode
wpa-psk ascii [PSK]
!
bridge irb
!
interface Dot11Radio0
no ip address
no ip route-cache
!
encryption mode ciphers aes-ccm
!
ssid DampaliVashli
!
antenna gain 0
stbc
station-role root
bridge-group 1
bridge-group 1 subscriber-loop-control
bridge-group 1 spanning-disabled
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
!
interface Dot11Radio1
no ip address
no ip route-cache
!
encryption vlan 1 mode ciphers aes-ccm
!
encryption mode ciphers aes-ccm
!
ssid DampaliVashli2
!
antenna gain 0
peakdetect
dfs band 3 block
stbc
channel dfs
station-role root
bridge-group 1
bridge-group 1 subscriber-loop-control
bridge-group 1 spanning-disabled
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
!
interface GigabitEthernet0
ip address 192.168.100.1 255.255.255.0
duplex auto
speed auto
bridge-group 1
bridge-group 1 spanning-disabled
no bridge-group 1 source-learning
!
interface BVI1
mac-address a0ec.f921.acac
ip address dhcp
ipv6 address dhcp
ipv6 address autoconfig
ipv6 enable
!
ip route 0.0.0.0 0.0.0.0 BVI1
!
bridge 1 route ip
!
!
!
2702i-M(config-if)#do show ip int brief
Interface IP-Address OK? Method Status Protocol
BVI1 73.44.185.162 YES DHCP up up
Dot11Radio0 unassigned YES NVRAM up up
Dot11Radio1 unassigned YES NVRAM up up
GigabitEthernet0. 192.168.100.1 YES NVRAM up up
!
!
Thanks.
Thank you for instructions! It realy helps!
Hi am trying to convert and old cisco ap ( CAP3502E ) just for learning purpose but I cannot fine the autonomous IOS for it. Tried cisco but won’t let me download it. Would you happen to know where I can find it?
Thanks.
I would search on internet
sorry, I cannot share those images
Rasika
😦 Ok thank you for your feed back.
I cant to uploaded the image i have a question i need to have both images in my server tftp or only the image called .default,
only 1 image required.
1. LAP -> AAP (rename that k9w7 file as .default)
2. AAP -> LAP (k9w8 recovery file rename as .default)
HTH
Rasika
Bro, thank you for your article – it helps a lot!
Recently I have bought CAP-2702i ($3.5 only) and now it is converted into autonomous mode.
I am new to Cisco (studying CCNA currently) and stuff looks a bit overwhelming at the glance thus I have got some obstacles on my way:
1. I could not connect AP directly to my laptop as have no injector or power supply yet. To empower AP I had connected both devices to 3750 PoE switch (switch was set to factory default settings). It cause me some doubts.
2. I had set IP on my notebook to 10.0.0.2 255.255.255.224 and gateway to 10.0.0.1 but could not ping 10.0.0.1 . I increases my doubts.
3. Nevertheless, I had installed the TFTPD64 and set the image path. However, having troubled with my doubts I forgot that file extensions on my PC was hidden, thus I had got image name “ap3g2-k9w7-tar.default.TAR” and it was not going to work. AP said that it cannot see the image in the folder or folder does not exist. I was lucky that my laptop has extensions visible, so I could see it clear and localize the problem fast upon a troubleshooting.
4. Finally, I have got image written into AP and it became autonomous but I could not get access as it was asking for a password. I did not understand the purpose of that three “password:” strings as I was taught that after factory reset of the switch or router there is no password or secret for Enable Mode at all. Eventually, I found that there is default secret for reset APs – “cisco” or “Cisco”, and last matches. For HTTP mode it works with “admin” login.
So, I guess it would be good idea to give some hints for newbies:
1. If you have no injector or power supply then use PoE+ switch with minimum settings on it or dumb.
2. Do not worry if you cannot ping 10.0.0.1
3. Check that the image name is ap3g2-k9w7-tar.default and there is no hidden extension. (only one image required in the TFTP folder).
4. Use “Cisco” or “cisco” password to get into Enable Mode and login into HTTP mode as “admin” with one of that passwords. Of course, you will want to change and save administrative login and password before you will install AP into a working network.
Cheers!
Serge
Hello, I have an AP Air-CAP2602i-A-K9 and I cannot download the software from anywhere. is there anyone who can pass me the link to download it? From the Cisco page I can’t because I don’t have a contract. Can you share that software with me?
I need to make this AP autonomous
Thank you
Same problem – I cannot download the file ap3g2-k9w7-tar.152-4.JA1.tar from Cisco page as I don’t a contract too.
Hello, i was researching in different places and i already could change it to standalone. but didnt work the antennas spreading the SSID. With this information i was able to set the device at standalone mode correctly and it is working now.
Thank you for sharing your knowledge
Regards from Mexico
Good to hear that and found this post useful.. Stay in safe..
Rasika
Hi,
I’m looking for the Firmware image:
ap3g2-k9w7
To make my AP autonomous.
Can you share it with me?
pls i have the same problem being discussed, can you help me get the image for 1142n-e-k9 image for AAP
thanks
I Also need this software please
ap3g2-k9w7-xx.152-2.JB
Did you ever find the firmware please
I know this is an older discussion, but I did have a fix that may help anyone in the future here.
If your machine is running windows and your tftp server won’t load, use a combination of these powershell commands to resolve the problem:
first – get-netconnectionprofile
– Look at the NetworkCategory of the Network interface you configured the 10.0.0.2 IP address on.
if it is set to “Public”, then run this second command. NOTE – you may need local admin access to be able to do this on your windows machine.
get-netconnectionprofile | where {$_.NetworkCategory -eq “Public”} | Set-NetConnectionProfile -NetworkCategory Private
this command sets any of your Network connections that have “Public” and sets them to “Private”.
When I’ve done this, it has worked for me, hope this helps someone else as well.
Thank you very much sharing this info Phil
hi phil. would you happen to know where i would be able to get the following firmware from please
ap3g1-k9w7-tar.152-2.JB.tar
thanks
Good day, after reviewing this post, it has offered much information and i appreciated it. unfortunately after upgrading the IOS i still encounter the same boot issue with FW.
AIR-CAP3702I – ap3g2-k9w8-tar.153-3.JPM.tar
my ap 2600 series does connect but gives error
Error opening tftp://255.255.255.255/ap3g2-k9w7-tar.default (no such file or directory)ap: 10.0.0.1
on tftpd64 logs says:
File <ap3g2-k9w7-tar.default>: error 2 in system call CreateFile The system cannot find the file specified. [22/08 13:18:44.208]
also on show directory, the file shows
ap3g2-k9w7-tar.default.tar
the .tar at the end shows the type of file, would the couse?