Tags
With the arrival of Wi-Fi 7 and widespread 6 GHz adoption, the landscape of enterprise network security is evolving rapidly. Understanding the nuances of enterprise security is now essential for maintaining a stable, high-performance wireless network. Watch this AKM overview video to gain comprehensive understanding of different Authentication and Key Management (AKM) types for Enterprise security.
The chart below shows the evolution of enterprise AKMs. Each AKM defines how devices authenticate and establish encryption and intergrity keys using algorithm like SHA-1, SHA-256 and SHA-384. WPA3 introduces stronger AKMs and encryption ciphers such as GCMP-AES-256 for enchanced security in modern networks.
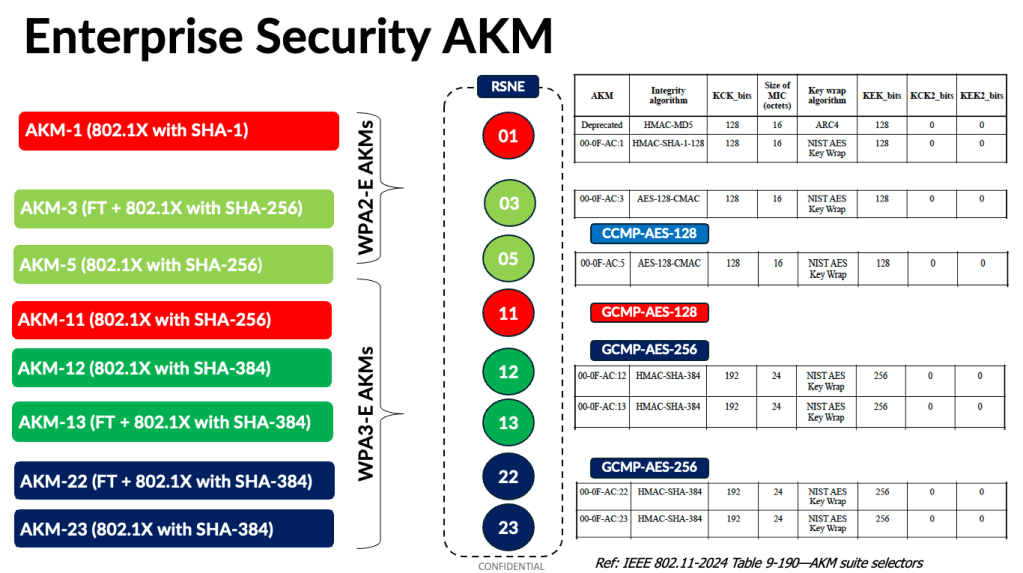
From a deployment perspective, you have three options
- WPA3 Enterprise only
- WPA3 Enterprise 192-bit mode
- WPA3 Transition mode
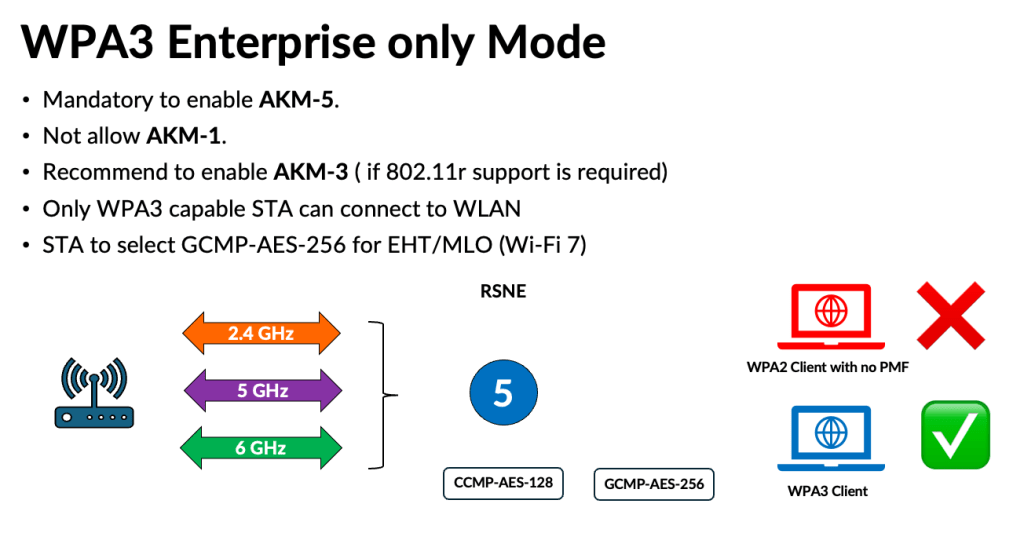
[WPA3 Enterprise only] If you have full control over your client devices and can ensure there are no legacy WPA2 clients that lack PMF support, you’re ahead of the game. In that case, you can confidently deploy WPA3-Enterprise only mode.
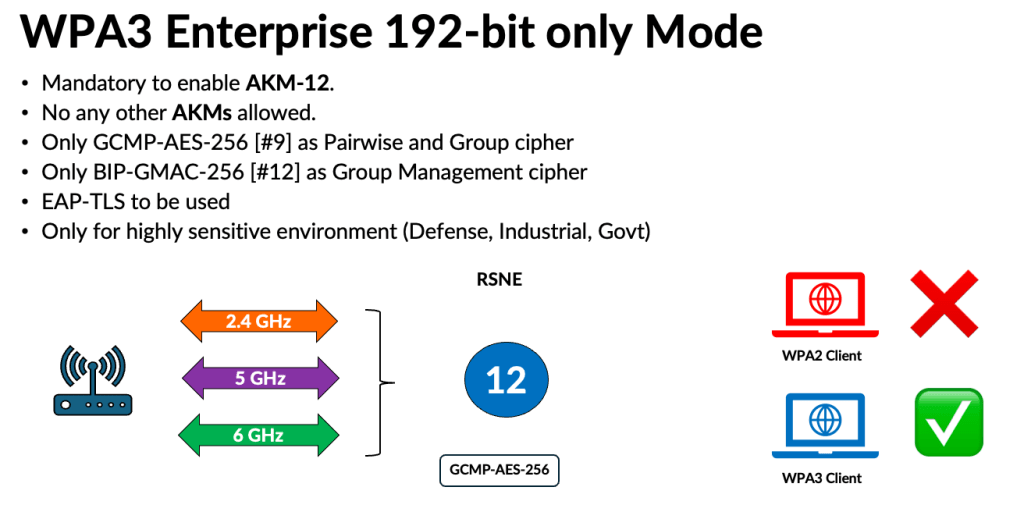
[WPA3 Enterprise 192-bit Mode]If you operate in a highly secure environment—such as government, defense, or industrial sectors—you should opt for the highest level of security. WPA3-Enterprise 192-bit, considered the gold standard, is the right choice for you.
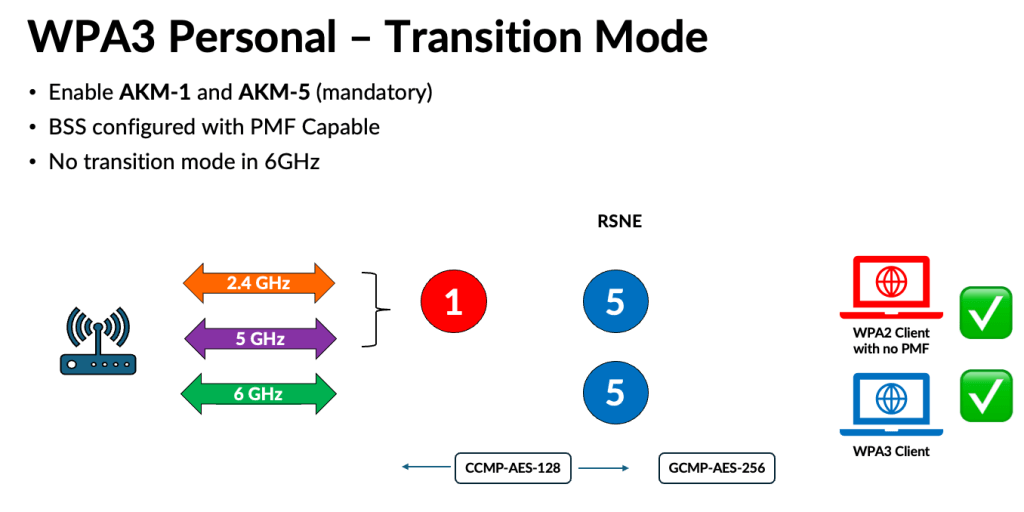
[WPA3 Enterprise Transition Mode]For most typical enterprises, you may still have legacy WPA2 clients using AKM-1 (SHA-1) and lacking PMF support. If replacing those clients isn’t an option, you’ll need to deploy WPA3-Enterprise Transition mode. This approach keeps WPA2 + WPA3 on your 2.4 GHz and 5 GHz bands, while using WPA3 exclusively on 6 GHz.
In the upcoming posts, I’ll dive into WPA3-Enterprise configurations and run tests with Wi-Fi 7 clients to see which devices truly support WPA3-Enterprise in the Wi-Fi 7 era.
