Tags
At this year’s WLPC, I had the opportunity to present on ‘WPA3 Deployment Challenges.’ I will share the link to the recorded session once it’s published (likely within a week). Here is the link to the presentation file.
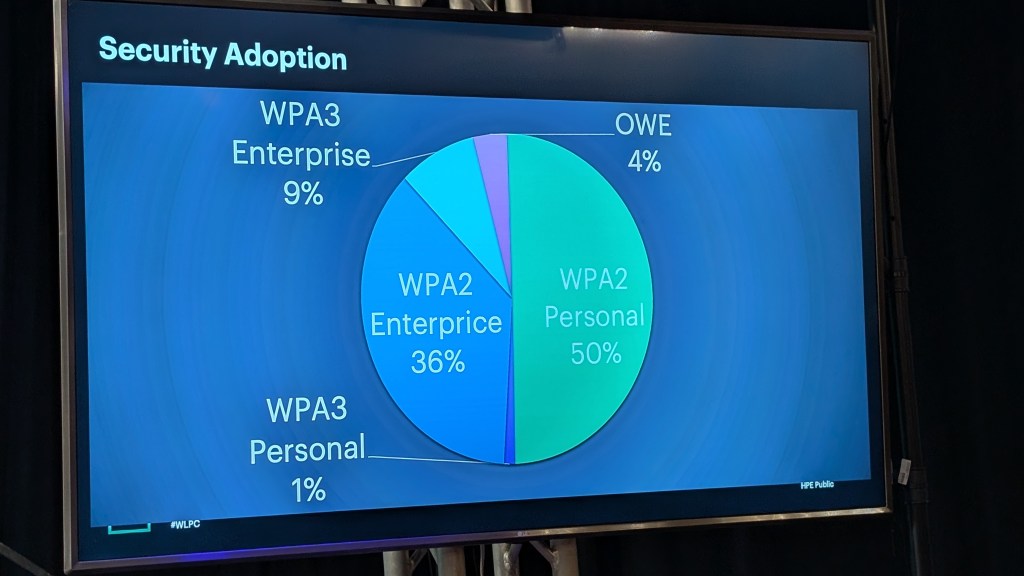
Based on the statistics shared by HPE–Juniper, only around 10% of Wi‑Fi authentications are using WPA3, and just 1% of those are WPA3‑Personal. I’m confident that WPA3 adoption rates are similar across other vendors as well. Thank you Wes for sharing these insights in your presentation.
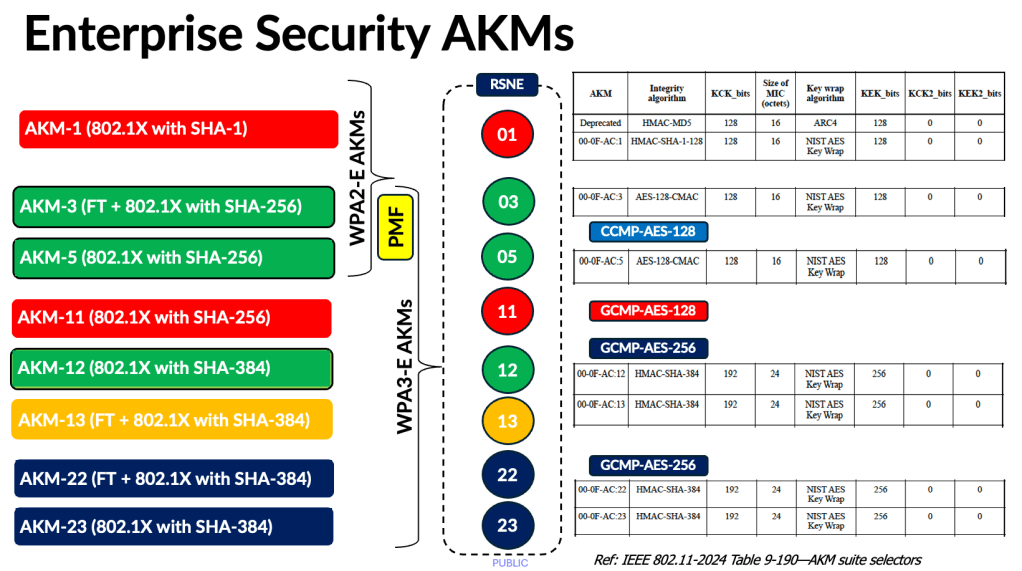
Here are the Enterprise security AKMs. The only difference between WPA2 and WPA3 Enterprise security is the requirement for MFP/PMF (Management Frame Protection); AKM 3 and AKM 5 are still used in WPA3‑Enterprise.
There are three deployment options available, with the most practical being WPA3‑Enterprise Transition.
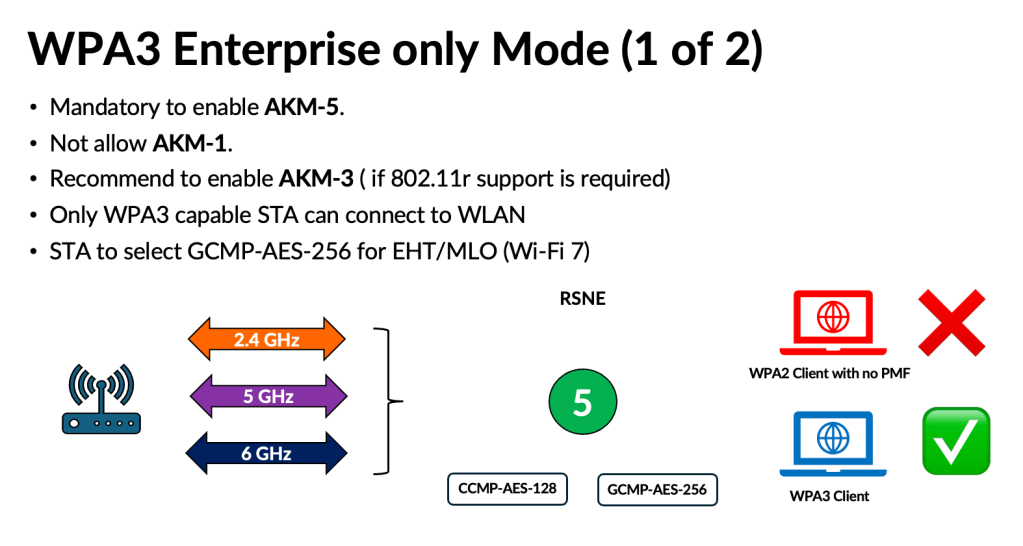
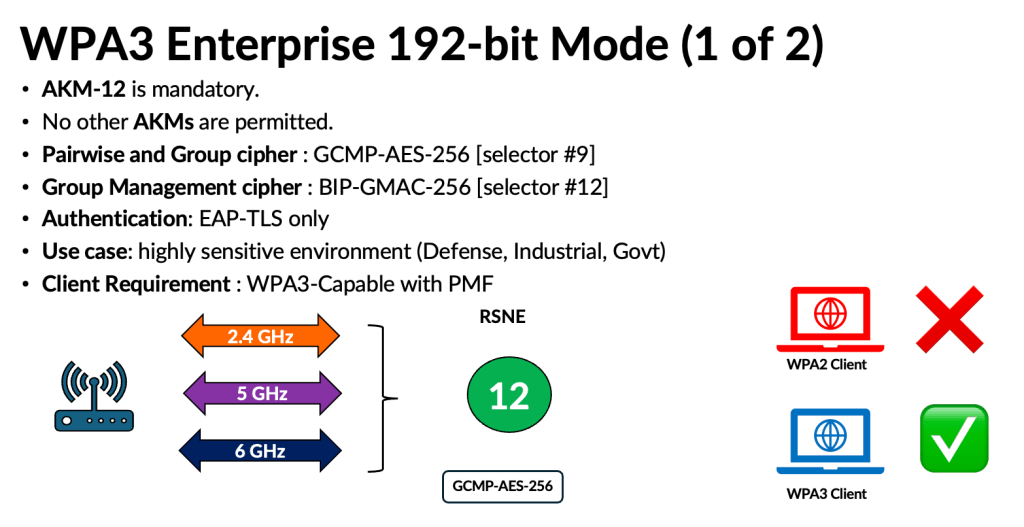
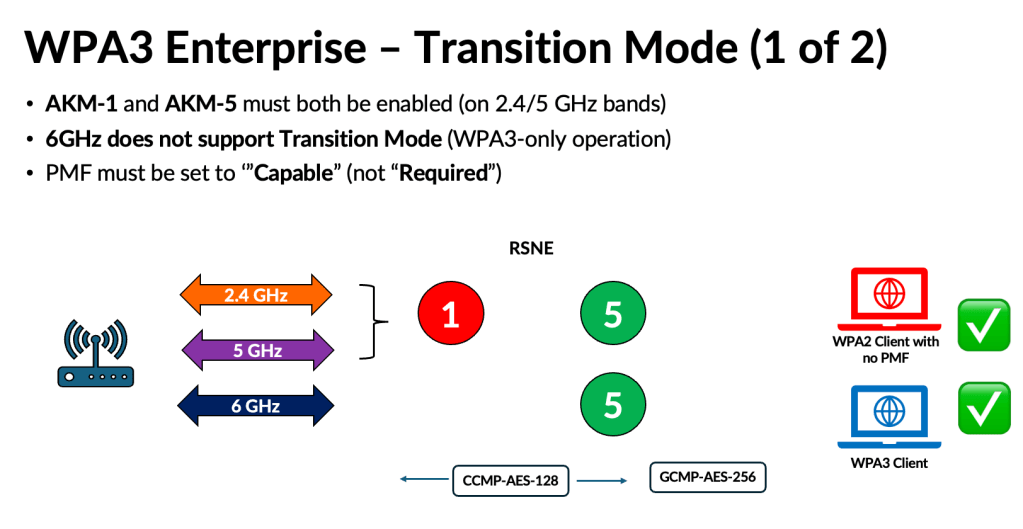
Because WPA3 uses the same AKMs (3 and 5) with PMF enabled, this mode does not introduce significant complications. However, depending on how AKM 22 and 23 are used in the future, they could lead to compatibility issues similar to those experienced with WPA3‑Personal. Here are some of the challenges highlighed in my presentation.
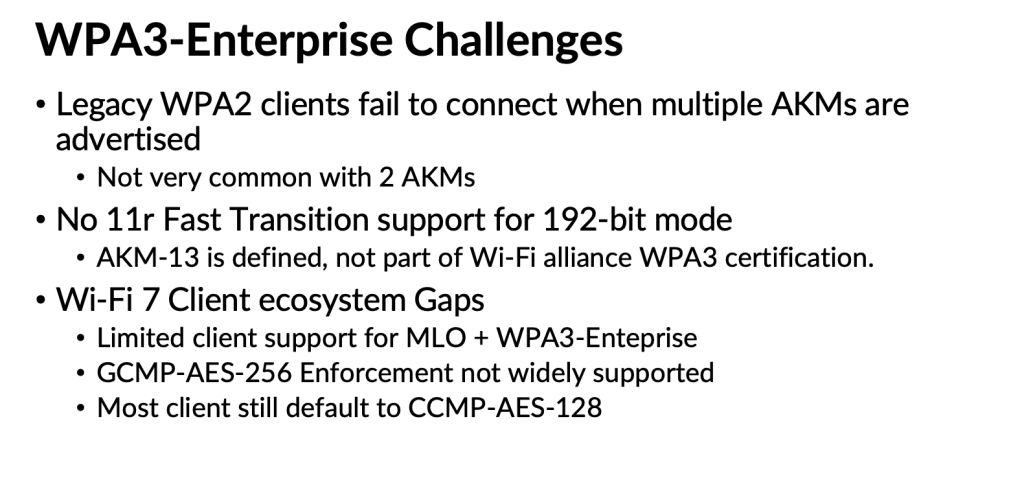
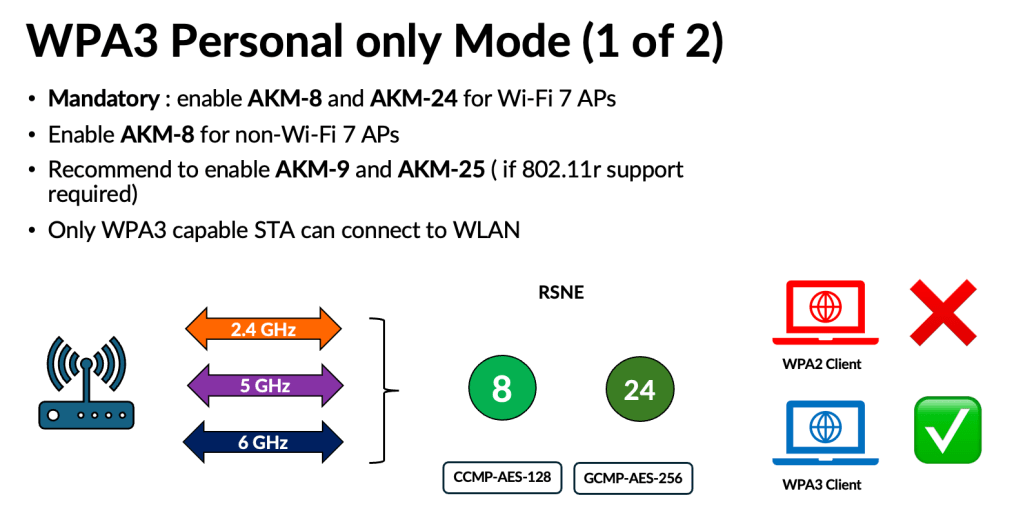
In WPA3‑Personal, new AKMs were introduced to address the vulnerabilities in WPA2‑Personal, along with the move to SAE authentication. With Wi‑Fi 7’s tightened security requirements, two additional AKMs (24 and 25) have also been introduced. As a result, transition‑mode deployments now require advertising more than two AKM suites, along with two cipher suites (CCMP‑AES‑128 and GCMP‑AES‑256). Below is the full list of Personal AKMs.
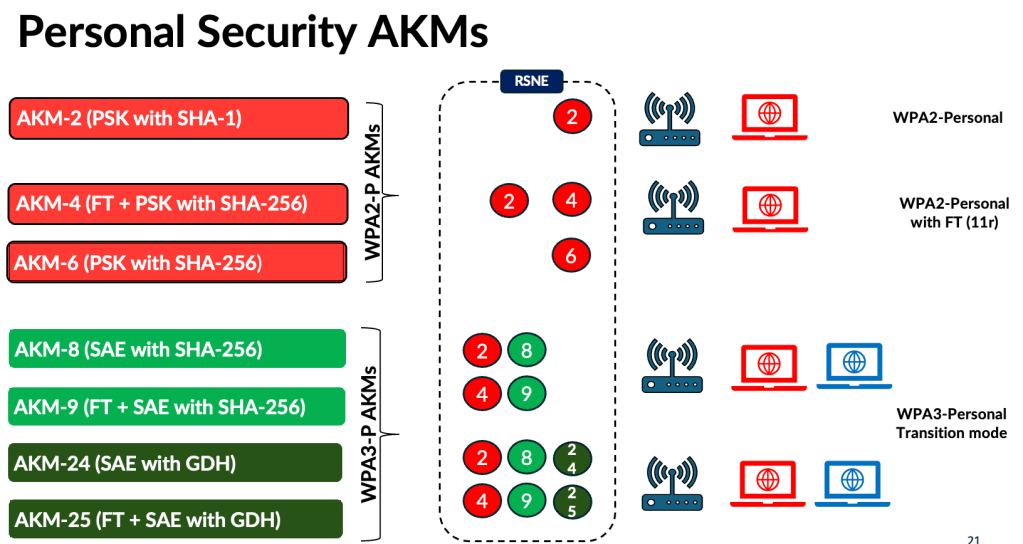
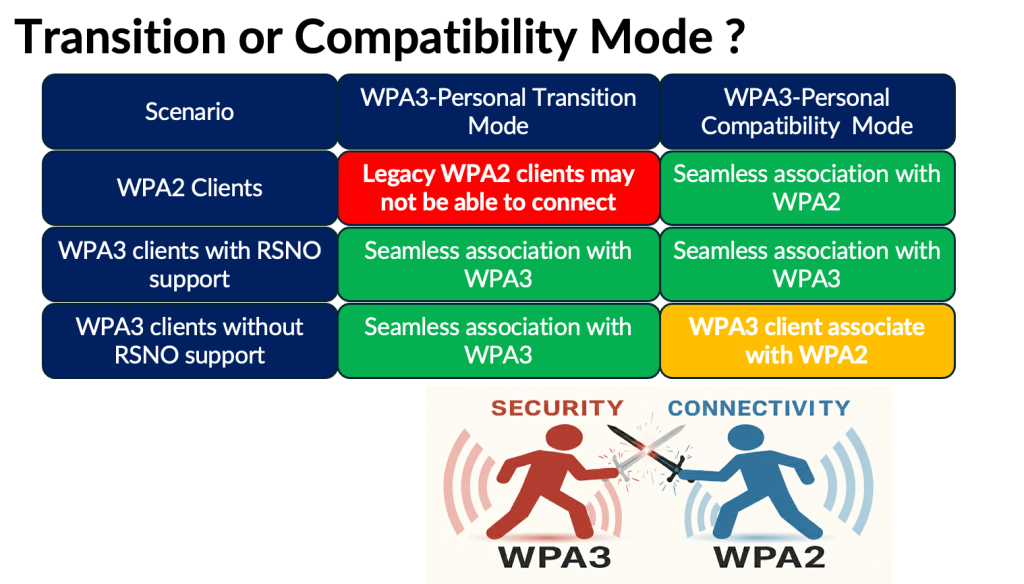
In WPA3‑Personal, you also have three deployment modes. If you have control over the endpoints, you can choose the ‘WPA3‑Personal–Only’ mode.
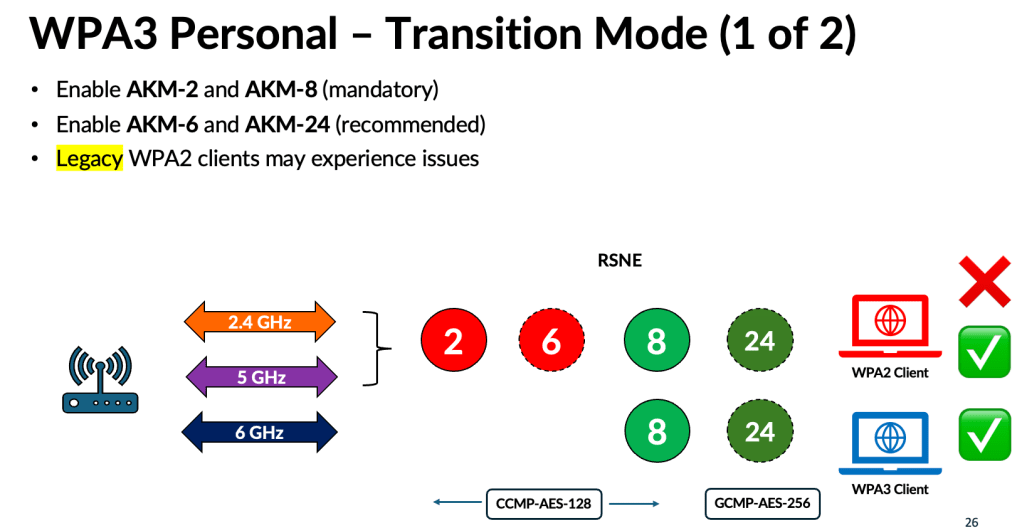
If you need both WPA2 and WPA3 clients to connect, then WPA3‑Personal Transition mode is the right choice. However, although we expected legacy WPA2 clients to behave well when multiple AKMs and cipher suites were introduced, many older clients still experience compatibility issues.
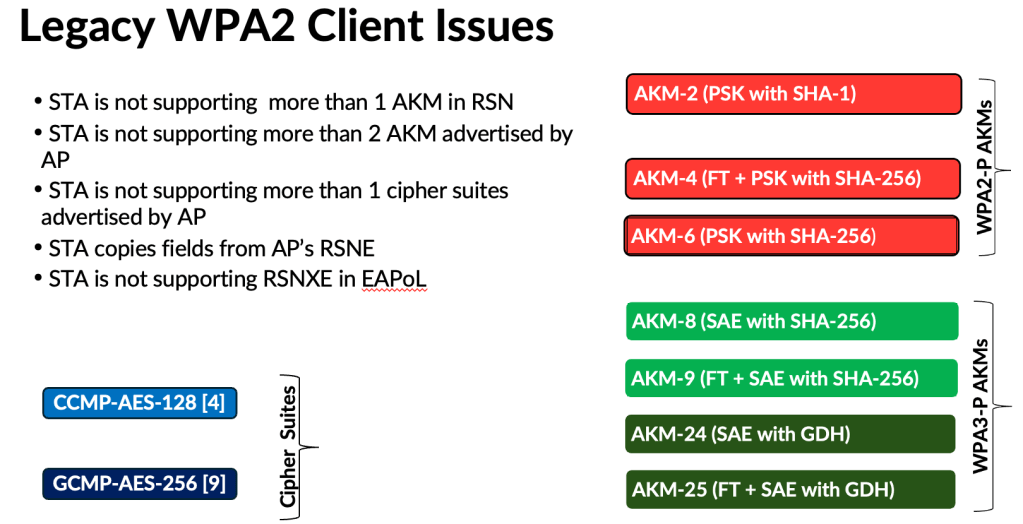
Here are some common issues seen in real‑world deployments. Because of these problems, it is nearly impossible for residential Wi‑Fi service providers to push this mode to home users, and many strongly push back when it comes to WPA3‑Transition.
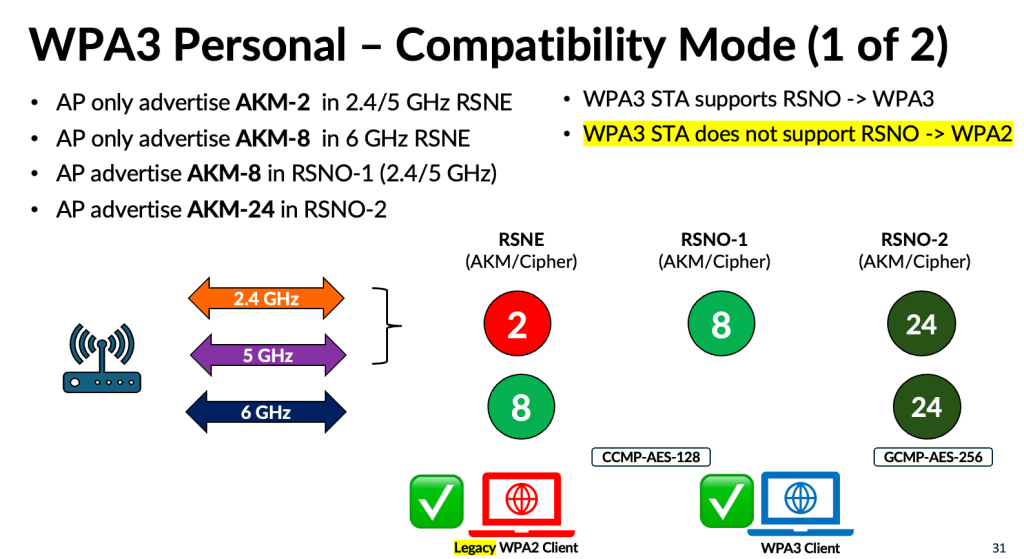
This led to the introduction of a new mode called WPA3‑Personal Compatibility, which keeps the RSN element limited to a single AKM (#2 – PSK with SHA1) and a single cipher suite (CCMP‑AES‑128), while introducing the newer AKMs through the RSN Override element (RSNO-1 and RSNO-2). This prevents legacy WPA2 clients from becoming confused. However, it also introduces a risk for WPA3‑capable clients that do not support RSNO. Since current WPA3 clients generally lack RSNO support unless vendors add it through firmware updates, those devices operating in the 2.4 GHz or 5 GHz bands may downgrade to WPA2 when it connect to WPA3-Compatibility mode SSID.
Given the very slow adoption of the Compatibility mode—partly because enterprise vendors do not see it as a priority and residential Wi‑Fi vendors are reluctant to introduce changes that might cause connectivity issues—it’s unlikely that these problems will be resolved anytime soon.
I’ve created several videos on this topic on my YouTube channel. If you’re interested, feel free to check them out.