In auto-anchor mobility mode, a subset of a mobility group is specified as the anchor controllers for a WLAN. You can use this feature to restrict a WLAN to a single subnet regardless of a client’s entry point into the network. Usually this is used for service guests in a corporate network. In this way all guests (irrespective of the location where they connect to wireless network) will get a same subnet IP usually via a WLC in a DMZ & can only go to internet where internal network access is restricted.
When a client first associate to a WLC of a mobility group that has been pre-configured as a mobility anchor for a WLAN, the client associate to the controller locally.Clients can be anchored only to pre-configured anchor controllers of the WLAN. (In guest service usually DMZ WLC). The client associated controller is announced this to the rest of the controller in the mobility list. If the announcement is not answered, the controller contacts one of the anchor controllers configured for the WLAN and create a foreign session for the client on the local switch. Packets from the client are encapsulated through a mobility tunnel using EoIP (IP protocol 97) & sent to the anchor controller. Here is the typical use case for Auto Anchor deployment.
Below is my topology to test this Auto-Anchor scenario. Objective is to assign same subnet IPs to guest users irrespective of the location they connect to the network. Also to provide better security by isolating guest traffic from the rest of the network. In this example guest user is connecting to wireless at Branch Office where that traffic tunnel back to DMZ controller in Head Office
In general settings in “Mobility Anchor Config” page you can change the keepalive interval & failure count value to determine an anchor controller is down. Keepalive count [3-20] specifies the number of times a ping request is sent to a mobility list member before the member is considered to be unreachable. Keepalive interval [1-30] specifies the amount of time(in seconds) between each ping request sent to a mobility list member. Also you can change DSCP value of these packets. Here are the default settings of these parameters.
By using CLI you can configure the above as follows
config mobility group keepalive count [3-20] config mobility group keepalive interval [1-30]
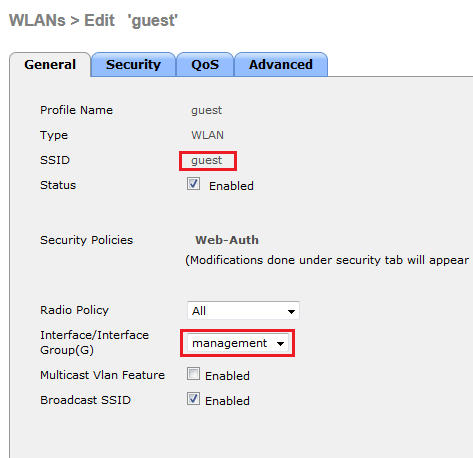
For the WLAN configuration first you need to create “guest” WLAN in branch controller (WLC3). You need to remember to map management interface to this WLAN in controllers other than DMZ WLC (See below). Only in DMZ controller you map this into a dynamic interface.
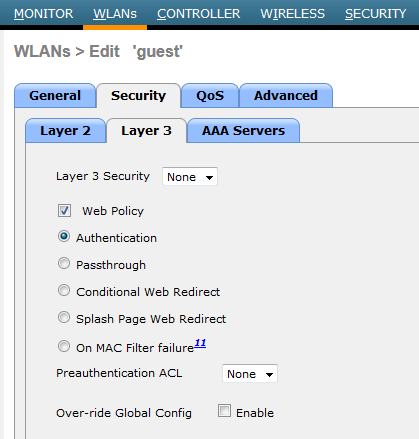
Since this SSID for guest services you need to enable WebAuth on that (depend on your Geust Access policy). In my example I have used basic web authentication where guest user is required to have username/password to access the network.
** It is very important to remember WLAN configuration settings should be identical in all controllers except only DMZ is having dynamic interface assign to it & all others having management interface assigned to it. If you do not follow this rule, your auto-anchor will not work ***
Prior to configure Mobility Anchor you need to verify both controllers configured for respective mobility groups and mobility list updated with each other controllers detail. I have configured mobility group “mrn-ccie” at Branch WLC3 & “mrn-cciew” group in Head Office WLC1.
Then you have to configure Mobility Anchor for this WLAN. You can go to Mobility Anchor configuration page as shown in the below.
Now you select WLC1 IP address as Mobility Anchor & click “Mobility Anchor Create” button. Once you do that you can verify Mobility Anchor has been created. See the below two screen captures.
In Mobility Anchor you have to anchor it to itself & do not anchor back to WLC3.
Now you can check the guest access service by connecting to your branch wireless network using “guest” SSID. Here is monitor client information once you successfully login to guest WLAN.
If you are interested in the “debug client <mac-address>” output of successful guest user connection, here it is. As mentioned in earlier post clients state changes from START (0) -> AUTHCHECK (2) -> L2AUTHCOMPLETE (4) -> DHCP_REQD (7) -> RUN (20) on non-anchor controller.
In Anchor Controller you would see “WEBAUTH_REQD -> WEBAUTH_NOL3SEC (14) -> RUN (20) states where Web Authentication takes place.
(WLC1) >debug client 04:f7:e4:ea:5b:66 # output ommitted *emWeb: Mar 22 20:48:02.621: 04:f7:e4:ea:5b:66 Username entry deleted for mobile *emWeb: Mar 22 20:48:02.622: 04:f7:e4:ea:5b:66 Username entry (user1) created for mobile *emWeb: Mar 22 20:48:02.629: 04:f7:e4:ea:5b:66 10.10.14.53 WEBAUTH_REQD (8) Change state to WEBAUTH_NOL3SEC (14) last state RUN (20) *emWeb: Mar 22 20:48:02.633: 04:f7:e4:ea:5b:66 apfMsRunStateInc *emWeb: Mar 22 20:48:02.633: 04:f7:e4:ea:5b:66 10.10.14.53 WEBAUTH_NOL3SEC (14) Change state to RUN (20) last state RUN (20) *emWeb: Mar 22 20:48:02.633: 04:f7:e4:ea:5b:66 Session Timeout is 0 - not starting session timer for the mobile *emWeb: Mar 22 20:48:02.634: 04:f7:e4:ea:5b:66 10.10.14.53 RUN (20) Reached PLUMBFASTPATH: from line 5063 *emWeb: Mar 22 20:48:02.634: 04:f7:e4:ea:5b:66 10.10.14.53 RUN (20) Replacing Fast Path rule type = Airespace AP Client on AP 00:00:00:00:00:00, slot 0, interface = 1, QOS = 0 ACL Id = 255, Jumbo Frames = NO *emWeb: Mar 22 20:48:02.634: 04:f7:e4:ea:5b:66 10.10.14.53 RUN (20) Fast Path rule (contd...) 802.1P = 3, DSCP = 0, TokenID = 5006 IPv6 Vlan = 14, IPv6 intf id = 11 *emWeb: Mar 22 20:48:02.634: 04:f7:e4:ea:5b:66 10.10.14.53 RUN (20) Successfully plumbed mobile rule (ACL ID 255) *pemReceiveTask: Mar 22 20:48:02.638: 04:f7:e4:ea:5b:66 Set bi-dir guest tunnel for 04:f7:e4:ea:5b:66 as in Export Anchor role *pemReceiveTask: Mar 22 20:48:02.643: 04:f7:e4:ea:5b:66 10.10.14.53 Added NPU entry of type 1, dtlFlags 0x4 (WLC3) >debug client 04:f7:e4:ea:5b:66 (WLC3) >*apfMsConnTask_0: Mar 22 20:35:45.706: 04:f7:e4:ea:5b:66 Adding mobile on LWAPP AP a0:cf:5b:9e:e8:20(1) *apfMsConnTask_0: Mar 22 20:35:45.706: 04:f7:e4:ea:5b:66 Association received from mobile on AP a0:cf:5b:9e:e8:20 *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 0.0.0.0 START (0) Changing ACL 'none' (ACL ID 0) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:1621) *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 Applying site-specific IPv6 override for station 04:f7:e4:ea:5b:66 - vapId 4, site 'default-group', interface 'management' *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 Applying IPv6 Interface Policy for station 04:f7:e4:ea:5b:66 - vlan 120, interface id 0, interface 'management' *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 STA - rates (6): 152 36 176 72 96 108 0 0 0 0 0 0 0 0 0 0 *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 0.0.0.0 START (0) Initializing policy *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 0.0.0.0 START (0) Change state to AUTHCHECK (2) last state AUTHCHECK (2) *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 0.0.0.0 AUTHCHECK (2) Change state to L2AUTHCOMPLETE (4) last state L2AUTHCOMPLETE (4) *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 0.0.0.0 L2AUTHCOMPLETE (4) DHCP Not required on AP a0:cf:5b:9e:e8:20 vapId 4 apVapId 4for this client *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 Not Using WMM Compliance code qosCap 00 *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 0.0.0.0 L2AUTHCOMPLETE (4) Plumbed mobile LWAPP rule on AP a0:cf:5b:9e:e8:20 vapId 4 apVapId 4 *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 0.0.0.0 L2AUTHCOMPLETE (4) Change state to DHCP_REQD (7) last state DHCP_REQD (7) *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 apfMsAssoStateInc *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 apfPemAddUser2 (apf_policy.c:223) Changing state for mobile 04:f7:e4:ea:5b:66 on AP a0:cf:5b:9e:e8:20 from Idle to Associated *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 Stopping deletion of Mobile Station: (callerId: 48) *apfMsConnTask_0: Mar 22 20:35:45.707: 04:f7:e4:ea:5b:66 Sending Assoc Response to station on BSSID a0:cf:5b:9e:e8:20 (status 0) ApVapId 4 Slot 1 *apfMsConnTask_0: Mar 22 20:35:45.708: 04:f7:e4:ea:5b:66 apfProcessAssocReq (apf_80211.c:5241) Changing state for mobile 04:f7:e4:ea:5b:66 on AP a0:cf:5b:9e:e8:20 from Associated to Associated *DHCP Socket Task: Mar 22 20:35:45.730: 04:f7:e4:ea:5b:66 DHCP received op BOOTREQUEST (1) (len 308,vlan 120, port 1, encap 0xec03) *DHCP Socket Task: Mar 22 20:35:45.730: 04:f7:e4:ea:5b:66 DHCP dropping packet due to ongoing mobility handshake exchange, (siaddr 0.0.0.0, mobility state = 'apfMsMmQueryRequested' *apfReceiveTask: Mar 22 20:35:47.683: 04:f7:e4:ea:5b:66 0.0.0.0 DHCP_REQD (7) State Update from Mobility-Incomplete to Mobility-Complete, mobility role=ExpForeign, client state=APF_MS_STATE_ASSOCIATED *apfReceiveTask: Mar 22 20:35:47.683: 04:f7:e4:ea:5b:66 apfMsRunStateInc *apfReceiveTask: Mar 22 20:35:47.683: 04:f7:e4:ea:5b:66 0.0.0.0 DHCP_REQD (7) Change state to RUN (20) last state RUN (20) *apfReceiveTask: Mar 22 20:35:47.685: 04:f7:e4:ea:5b:66 0.0.0.0 RUN (20) Reached PLUMBFASTPATH: from line 4495 *apfReceiveTask: Mar 22 20:35:47.685: 04:f7:e4:ea:5b:66 0.0.0.0 RUN (20) Adding Fast Path rule type = Airespace AP Client on AP a0:cf:5b:9e:e8:20, slot 1, interface = 1, QOS = 0 ACL Id = 255, Jumbo Frames = NO *apfReceiveTask: Mar 22 20:35:47.685: 04:f7:e4:ea:5b:66 0.0.0.0 RUN (20) Fast Path rule (contd...) 802.1P = 0, DSCP = 0, TokenID = 1506 IPv6 Vlan = 120, IPv6 intf id = 0 *apfReceiveTask: Mar 22 20:35:47.685: 04:f7:e4:ea:5b:66 0.0.0.0 RUN (20) Successfully plumbed mobile rule (ACL ID 255) *pemReceiveTask: Mar 22 20:35:47.686: 04:f7:e4:ea:5b:66 Set bi-dir guest tunnel for 04:f7:e4:ea:5b:66 as in Export Foreign role *pemReceiveTask: Mar 22 20:35:47.699: 04:f7:e4:ea:5b:66 0.0.0.0 Added NPU entry of type 1, dtlFlags 0x4 *DHCP Socket Task: Mar 22 20:35:47.764: 04:f7:e4:ea:5b:66 DHCP received op BOOTREQUEST (1) (len 308,vlan 120, port 1, encap 0xec03) *DHCP Socket Task: Mar 22 20:35:47.764: 04:f7:e4:ea:5b:66 DHCP processing DHCP REQUEST (3) *DHCP Socket Task: Mar 22 20:35:47.764: 04:f7:e4:ea:5b:66 DHCP op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 0 *DHCP Socket Task: Mar 22 20:35:47.764: 04:f7:e4:ea:5b:66 DHCP xid: 0x75162e82 (1964387970), secs: 512, flags: 0 *DHCP Socket Task: Mar 22 20:35:47.764: 04:f7:e4:ea:5b:66 DHCP chaddr: 04:f7:e4:ea:5b:66 *DHCP Socket Task: Mar 22 20:35:47.764: 04:f7:e4:ea:5b:66 DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:47.765: 04:f7:e4:ea:5b:66 DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:47.765: 04:f7:e4:ea:5b:66 DHCP requested ip: 149.144.136.4 *DHCP Socket Task: Mar 22 20:35:47.765: 04:f7:e4:ea:5b:66 DHCP successfully bridged packet to EoIP tunnel *DHCP Socket Task: Mar 22 20:35:49.466: 04:f7:e4:ea:5b:66 DHCP received op BOOTREQUEST (1) (len 308,vlan 120, port 1, encap 0xec03) *DHCP Socket Task: Mar 22 20:35:49.466: 04:f7:e4:ea:5b:66 DHCP processing DHCP REQUEST (3) *DHCP Socket Task: Mar 22 20:35:49.466: 04:f7:e4:ea:5b:66 DHCP op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 0 *DHCP Socket Task: Mar 22 20:35:49.466: 04:f7:e4:ea:5b:66 DHCP xid: 0x75162e82 (1964387970), secs: 1024, flags: 0 *DHCP Socket Task: Mar 22 20:35:49.466: 04:f7:e4:ea:5b:66 DHCP chaddr: 04:f7:e4:ea:5b:66 *DHCP Socket Task: Mar 22 20:35:49.467: 04:f7:e4:ea:5b:66 DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:49.467: 04:f7:e4:ea:5b:66 DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:49.467: 04:f7:e4:ea:5b:66 DHCP requested ip: 149.144.136.4 *DHCP Socket Task: Mar 22 20:35:49.467: 04:f7:e4:ea:5b:66 DHCP successfully bridged packet to EoIP tunnel *DHCP Socket Task: Mar 22 20:35:49.475: 04:f7:e4:ea:5b:66 DHCP received op BOOTREPLY (2) (len 312,vlan 120, port 1, encap 0xec05) *DHCP Socket Task: Mar 22 20:35:49.476: 04:f7:e4:ea:5b:66 DHCP processing DHCP NAK (6) *DHCP Socket Task: Mar 22 20:35:49.476: 04:f7:e4:ea:5b:66 DHCP op: BOOTREPLY, htype: Ethernet, hlen: 6, hops: 0 *DHCP Socket Task: Mar 22 20:35:49.476: 04:f7:e4:ea:5b:66 DHCP xid: 0x75162e82 (1964387970), secs: 0, flags: 80 *DHCP Socket Task: Mar 22 20:35:49.476: 04:f7:e4:ea:5b:66 DHCP chaddr: 04:f7:e4:ea:5b:66 *DHCP Socket Task: Mar 22 20:35:49.476: 04:f7:e4:ea:5b:66 DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:49.476: 04:f7:e4:ea:5b:66 DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:49.476: 04:f7:e4:ea:5b:66 DHCP server id: 1.1.1.1 rcvd server id: 1.1.1.1 *DHCP Socket Task: Mar 22 20:35:49.477: 04:f7:e4:ea:5b:66 DHCP successfully bridged packet to STA *DHCP Socket Task: Mar 22 20:35:49.628: 04:f7:e4:ea:5b:66 DHCP received op BOOTREQUEST (1) (len 308,vlan 120, port 1, encap 0xec03) *DHCP Socket Task: Mar 22 20:35:49.629: 04:f7:e4:ea:5b:66 DHCP processing DHCP DISCOVER (1) *DHCP Socket Task: Mar 22 20:35:49.629: 04:f7:e4:ea:5b:66 DHCP op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 0 *DHCP Socket Task: Mar 22 20:35:49.629: 04:f7:e4:ea:5b:66 DHCP xid: 0x75162e83 (1964387971), secs: 0, flags: 0 *DHCP Socket Task: Mar 22 20:35:49.629: 04:f7:e4:ea:5b:66 DHCP chaddr: 04:f7:e4:ea:5b:66 *DHCP Socket Task: Mar 22 20:35:49.629: 04:f7:e4:ea:5b:66 DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:49.629: 04:f7:e4:ea:5b:66 DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:49.630: 04:f7:e4:ea:5b:66 DHCP successfully bridged packet to EoIP tunnel *DHCP Socket Task: Mar 22 20:35:49.633: 04:f7:e4:ea:5b:66 DHCP received op BOOTREPLY (2) (len 312,vlan 120, port 1, encap 0xec05) *DHCP Socket Task: Mar 22 20:35:49.633: 04:f7:e4:ea:5b:66 DHCP processing DHCP OFFER (2) *DHCP Socket Task: Mar 22 20:35:49.633: 04:f7:e4:ea:5b:66 DHCP op: BOOTREPLY, htype: Ethernet, hlen: 6, hops: 0 *DHCP Socket Task: Mar 22 20:35:49.633: 04:f7:e4:ea:5b:66 DHCP xid: 0x75162e83 (1964387971), secs: 0, flags: 0 *DHCP Socket Task: Mar 22 20:35:49.633: 04:f7:e4:ea:5b:66 DHCP chaddr: 04:f7:e4:ea:5b:66 *DHCP Socket Task: Mar 22 20:35:49.633: 04:f7:e4:ea:5b:66 DHCP ciaddr: 0.0.0.0, yiaddr: 10.10.14.53 *DHCP Socket Task: Mar 22 20:35:49.633: 04:f7:e4:ea:5b:66 DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:49.633: 04:f7:e4:ea:5b:66 DHCP server id: 1.1.1.1 rcvd server id: 1.1.1.1 *DHCP Socket Task: Mar 22 20:35:49.633: 04:f7:e4:ea:5b:66 DHCP successfully bridged packet to STA *DHCP Socket Task: Mar 22 20:35:50.863: 04:f7:e4:ea:5b:66 DHCP received op BOOTREQUEST (1) (len 308,vlan 120, port 1, encap 0xec03) *DHCP Socket Task: Mar 22 20:35:50.863: 04:f7:e4:ea:5b:66 DHCP processing DHCP DISCOVER (1) *DHCP Socket Task: Mar 22 20:35:50.863: 04:f7:e4:ea:5b:66 DHCP op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 0 *DHCP Socket Task: Mar 22 20:35:50.863: 04:f7:e4:ea:5b:66 DHCP xid: 0x75162e83 (1964387971), secs: 256, flags: 0 *DHCP Socket Task: Mar 22 20:35:50.863: 04:f7:e4:ea:5b:66 DHCP chaddr: 04:f7:e4:ea:5b:66 *DHCP Socket Task: Mar 22 20:35:50.863: 04:f7:e4:ea:5b:66 DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:50.863: 04:f7:e4:ea:5b:66 DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:50.863: 04:f7:e4:ea:5b:66 DHCP successfully bridged packet to EoIP tunnel *DHCP Socket Task: Mar 22 20:35:50.865: 04:f7:e4:ea:5b:66 DHCP received op BOOTREPLY (2) (len 312,vlan 120, port 1, encap 0xec05) *DHCP Socket Task: Mar 22 20:35:50.865: 04:f7:e4:ea:5b:66 DHCP processing DHCP OFFER (2) *DHCP Socket Task: Mar 22 20:35:50.865: 04:f7:e4:ea:5b:66 DHCP op: BOOTREPLY, htype: Ethernet, hlen: 6, hops: 0 *DHCP Socket Task: Mar 22 20:35:50.865: 04:f7:e4:ea:5b:66 DHCP xid: 0x75162e83 (1964387971), secs: 0, flags: 0 *DHCP Socket Task: Mar 22 20:35:50.865: 04:f7:e4:ea:5b:66 DHCP chaddr: 04:f7:e4:ea:5b:66 *DHCP Socket Task: Mar 22 20:35:50.865: 04:f7:e4:ea:5b:66 DHCP ciaddr: 0.0.0.0, yiaddr: 10.10.14.53 *DHCP Socket Task: Mar 22 20:35:50.865: 04:f7:e4:ea:5b:66 DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:50.865: 04:f7:e4:ea:5b:66 DHCP server id: 1.1.1.1 rcvd server id: 1.1.1.1 *DHCP Socket Task: Mar 22 20:35:50.865: 04:f7:e4:ea:5b:66 DHCP successfully bridged packet to STA *DHCP Socket Task: Mar 22 20:35:52.002: 04:f7:e4:ea:5b:66 DHCP received op BOOTREQUEST (1) (len 308,vlan 120, port 1, encap 0xec03) *DHCP Socket Task: Mar 22 20:35:52.002: 04:f7:e4:ea:5b:66 DHCP processing DHCP REQUEST (3) *DHCP Socket Task: Mar 22 20:35:52.002: 04:f7:e4:ea:5b:66 DHCP op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 0 *DHCP Socket Task: Mar 22 20:35:52.002: 04:f7:e4:ea:5b:66 DHCP xid: 0x75162e83 (1964387971), secs: 512, flags: 0 *DHCP Socket Task: Mar 22 20:35:52.002: 04:f7:e4:ea:5b:66 DHCP chaddr: 04:f7:e4:ea:5b:66 *DHCP Socket Task: Mar 22 20:35:52.002: 04:f7:e4:ea:5b:66 DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:52.002: 04:f7:e4:ea:5b:66 DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:52.002: 04:f7:e4:ea:5b:66 DHCP requested ip: 10.10.14.53 *DHCP Socket Task: Mar 22 20:35:52.002: 04:f7:e4:ea:5b:66 DHCP server id: 1.1.1.1 rcvd server id: 1.1.1.1 *DHCP Socket Task: Mar 22 20:35:52.002: 04:f7:e4:ea:5b:66 DHCP successfully bridged packet to EoIP tunnel *DHCP Socket Task: Mar 22 20:35:52.004: 04:f7:e4:ea:5b:66 DHCP received op BOOTREPLY (2) (len 312,vlan 120, port 1, encap 0xec05) *DHCP Socket Task: Mar 22 20:35:52.004: 04:f7:e4:ea:5b:66 DHCP processing DHCP ACK (5) *DHCP Socket Task: Mar 22 20:35:52.005: 04:f7:e4:ea:5b:66 DHCP op: BOOTREPLY, htype: Ethernet, hlen: 6, hops: 0 *DHCP Socket Task: Mar 22 20:35:52.005: 04:f7:e4:ea:5b:66 DHCP xid: 0x75162e83 (1964387971), secs: 0, flags: 0 *DHCP Socket Task: Mar 22 20:35:52.005: 04:f7:e4:ea:5b:66 DHCP chaddr: 04:f7:e4:ea:5b:66 *DHCP Socket Task: Mar 22 20:35:52.005: 04:f7:e4:ea:5b:66 DHCP ciaddr: 0.0.0.0, yiaddr: 10.10.14.53 *DHCP Socket Task: Mar 22 20:35:52.005: 04:f7:e4:ea:5b:66 DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0 *DHCP Socket Task: Mar 22 20:35:52.005: 04:f7:e4:ea:5b:66 DHCP server id: 1.1.1.1 rcvd server id: 1.1.1.1 *DHCP Socket Task: Mar 22 20:35:52.005: 04:f7:e4:ea:5b:66 10.10.14.53 RUN (20) DHCP Address Re-established *DHCP Socket Task: Mar 22 20:35:52.005: 04:f7:e4:ea:5b:66 Assigning Address 10.10.14.53 to mobile *DHCP Socket Task: Mar 22 20:35:52.005: 04:f7:e4:ea:5b:66 DHCP success event for client. Clearing dhcp failure count for interface management. *DHCP Socket Task: Mar 22 20:35:52.005: 04:f7:e4:ea:5b:66 DHCP successfully bridged packet to STA
Here are some other blog posts which I think really useful to understand this topic.
Auto-Anchor Mobility Fundamentals
Related Posts
1. Wireless Mobility Basics
2. Configuring Mobility on WLC
3. L2-Inter Controller Roaming
4. L3-Inter Controller Roaming
5. WLC – Web Authentication
6. Auto-Anchor Foreign Mapping
7. Mobility Ping Tests
8. Configuring Wired Guest
9. Static IP Clients Mobility







Hello
thanks for your detailed explanations!
One question – i have issue with DHCP for remote WLAN guests.
All WLAN guests no matter in which location they are (branch or HQ) shall get IP from a central external DHCP Server in HQ (microsoft dhcp server).
But this only works for wlan guests, who are associated to access points which is connected to WLC in HQ, which is also central anchor controller for all foreign wlcs.
When a guest instead connects to an AP connected to a foreign WLC in branch office, which is properly connected via EoIP to the Anchor Controller, that guest user only gets an IP from the DHCP Server configured locally on the Anchor Controller.
From my understanding, DHCP Discover packets from wlan guests in branch office should get over the EoIP Tunnel to the anchor controller, which acts as dhcp relay agent and passes the dhcp ip.
But that only works when dhcp runs on WLC and not when external DHCP Server is used.
Any idea? I did read all the documents and simply can not fix it.
Regards & many thanks
Hello
Your articles are very good. I have a doubt here. How the anchor WLC connected to Firewall and how many interfaces are configured. In your diagram you have mentioned 10.10.111.10 is management IP of DMZ and guest vlan is 10.10.14.0 means it will connected to different interface . i didn’t understand anchor WLC placement here. Could you please explain me in details
Hi
Have you ever tested guest ssid with two anchor controller which are not in HA..how the load balancing will be performed….do we have control on load balancing method from foreign controller to two anchor controller not in HA….? it creating issue with ISE…any idea..
I haven’t test it, but it will be just simple round-robin
HTH
Rasika
Hi Rasika
Great site, packed full of useful information!! A quick question on the above scenario, In the event of multiple anchor WLCs for a WLAN do you know whether the Foreign WLC remembers which anchor to map it to? Much like the hash created when using Interface groups. I had hoped it would but I appear to have clients bouncing between Anchors, unfortunately I’ve inherited a setup where the anchors are also providing DHCP, scopes are split between the anchors and my scopes are getting full far too quickly.
It would appear that the foreign WLC load balances without considering the clients previous anchor, though I can’t find any information to confirm this.
Many thanks
Mark
Pingback: Auto-Anchor Foreign Mapping | CCIE Blogger
Hello,
is there a way to have more WLAN profiles with the same SSID and different rate limiting?
If we want to have one global naming standard but different rate limiting for countries ..
Thanks!
I think you may need to explore RADIUS attributes to assign QoS profile based on identity.
HTH
Rasika
Could you elaborate more on that pls? Any blog entry or something like that would be very helpful.
thanks
Question?
Do the SSID’s need to match exactly on Both the Foreign WLC’s, and the Anchor’s?
Is eoip tunnel break and any impact for guest users if Anchor controller’s host name change ?
I do not think host name change would impact EoIP tunnels
HTH
Rasika
Little confused here, you wrote, “In Mobility Anchor you have to anchor it to itself & do not anchor back to WLC3.” But WLC3 is actually the Mobility Anchor. So I would anchor it to itself and WLC1 (branch/campus) WLC’s I will statically anchor to WLC3 right?
Thanks
WLC1 is the anchor. (WLC3 is the foreign WLC here)
So WLC1 is anchor to itself & foreign WLC3 is anchor back to WLC1
HTH
Rasika
Eh you are right my bad sorry was studying late my brain was falling asleep. Thank you. Love your blog by the way.
No problem 🙂
Enjoy your studies
Hi Rasika
Think there’s one thing that requires some clarification. You have stated that Foreign WLCs must have management interface configured as WLAN interface, but this is not really true. In fact, I remember Cisco recommended to have this configured into isolated Bogus VLAN few years ago. If I am not wrong, it was due to the way anchoring worked back then. If EoIP/Mobility tunnel went down, it would switch users using this local interface (the one assigned to the WLAN). Effectively users would receive IP addresses from the VLAN where management interface sits. I have never tested it to prove, but since then I always configure a Bogus interface with non-trunked VLAN (i.e. 999), with dummy DHCP, dummy IP and mask and assign it to anchored WLANs. It works like a charm because WLC always uses management interface to establish the tunnel anyway.
I don’t remember where I read it, it was years ago. Just wanted to share this.
Hi Tim,
Yes, you are right, it does not need to be management (actually it is recommended to assign it to a dummy interface for better security)
HTH
Rasika
Hi Rasika,
I have a question on Mobility Anchor config.
Currently a few foreign WLCs are connected to the Anchor WLC-old (single) located in DMZ.
1. We are planning to build a new Anchor WLC-new in another DC and will decommission the existing Anchor WLC-old (no Redundancy yet)
2. it will be running with the new single WLC-new for a while and the WLC-old will be moving to another DC as a standby WLC.
now WLC-new and WLC-old (active and standby)
3. what is a requirement to connect the foreign WLCs to the standby WLC-old?
just configure Anchor Mobility between foreign WLCs and the standby WLC-old?
How does redundancy work when the active anchor WLC fails?
Thanks,
Sam
Hi Sam,
Have a look below, after 8.1 you can configure priority value for Anchor redundancy
https://www.cisco.com/c/en/us/td/docs/wireless/controller/8-1/Enterprise-Mobility-8-1-Design-Guide/Enterprise_Mobility_8-1_Deployment_Guide/WirelessNetwork_GuestAccessService.html
HTH
Rasika
Hi Rasika, if all Guest Traffic is Tunnelled between Controllers. Is the guest traffics destination address always the WLCs Management interface?
I have a remote WLC with two ISPs and I want to route guest traffic out over the backup ISP, any idea how I should do this?
Should I simply create a static route to forward traffic with destination IP of Anchor Management Interface towards secondary ISP interface?
Hi Rasika!
It is possible to configure guest anchor between different domains?
I have one WLC that belong to one company and another WLC that belongs to another company and they want to configure guest anchor, but they have different domains names. If I configure the same mobility domain name it works, but if I configure only the same name for mobility group it doesn’t work.
Do you know if there is any way to achieve what I want? (guest anchor between WLCs with different mobility domain name.
Thanks in advance!