In this post we will see how to control access to WLC for different type of users using TACACS (ACS 5.2).
I will create 3 different user type (Admin, User, Guest) where “Admin” user have full access to WLC (modify, add, delete, etc), “User” having access to “WLAN” & “WIRELESS” section of the WLC to modify. All other area only read only view. For Guest users only have access to “Monitor” section of WLC.
First make sure your WLC is configured with ACS for AAA (Authentication/Accounting/Authorization). Here is the screenshot of WLC configured ACS for Authentication. You have to do this for Accounting & Authorization as well.
Then change the Priority order for management user ( in Security -> Priority Order -> Management User Section). Ensure that TACACS+ is check first & then local.
In ACS first you have to add your WLC ( in Network Resources -> Network Devices & AAA Clients section as shown below. You can create Location Group & Device Type group if you require more granular conditions in later on. I have created “HQ” location group & “WLC ” Device type group for this. Used the same shared secret key used for WLC.
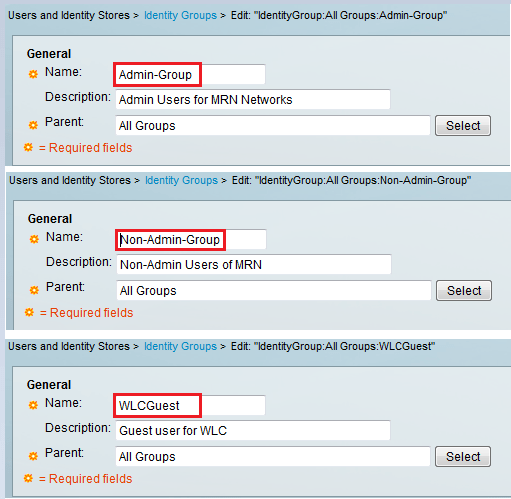
Then we will create Identity Groups for those 3 different type of users
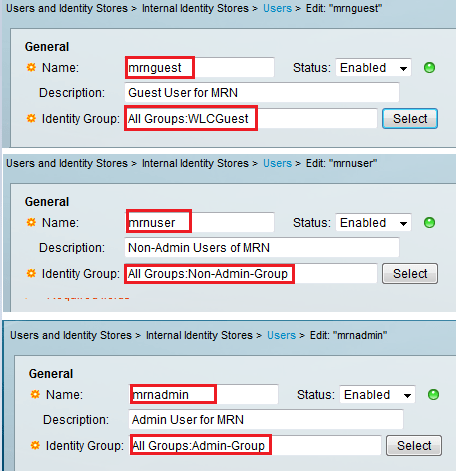
Then create 3 different users each in the 3 separate groups created.
Then go to Policy Element to define 3 different policy for this. Here is how you create it ( Policy Elements -> Authorization & Permissions -> Device Administration -> Shell Profile” . Once you give a Name & Description under the General tab, you have to go to Custom Attributes to specify the roles.
For Admin user “role1” should be “ALL” (unfortunately these are case sensitive & ensure no spaces, etc). I tried with Role1 & did not work. Therefore ALL, WLAN, MONITOR, SECURITY should be as it is.
Remember to click Add buttone before hit submit button.
Here is the setting for Non-Admin User ( Access to WLAN & WIRELESS sections of WLC)
Here is the Guest user policy only permitting “MONITOR” section of WLC.
In the same section (Device Administration -> Command Set) you have to create a commnad sets. But in here we allow all TACACS commands since shell profile we created limited the user scope.
Now you can define rule set for each type of users request. For WLCAdmin rule, you can match TACACS request coming from “WLC” device group where users belong to “Admin-Group”. Once this condition match it will select “WLCAdmin” shell profile you created in the early step.
So here is the rules for WLCUser.
Here is the rule created for WLCGuest.
Once you do this your rule set should appear like this. you can change the order by hitting UP or Down Arrow button as shown.(to ensure more specific rules are first)
Now it is time to test. First with WLCGuest user called “mrnguest”. If you try to modify any settings & try to apply you will get an error message like this.
But if you log in as WLCUser called “mrnuser” you can modify any settings under WLAN & WIRELESS tab of WLC. But if you try to modify any setting otherthan these two you will get the similar error message.
For WLCAdmin user called “mrnadmin” you will see he can do any thing and no error messages.
If you go to ACS you can verify successful login of these 3 different users.

Related Posts
1. Configuring Local EAP on WLC
2. Configuring EAP-TLC on WLC
3. Configuring EAP-TLS on ACS
4. Configuring RADIUS on WLC
5. Configuring TACACS on WLC
6. WLC Admin Access via RADIUS















Good afternoon. I am trying this configuration but users get access only by their username, it doesnt matter what password I enter in the WLC, I still have an appropriate type of access.
Maybe you know where my mistake is?
Very useful and well written article to the point. I was struggling with TACAS authentication part on WLC. I was missing the point that on ACS role1 is case sensitive. Thanks very much.
Thanks Raj for the feedback…
Hi Rasiak,
why do you configure “command sets”? I do not see this configuration in guides (see below) and i tested this and all work fine without “command sets”.
1)http://www.cisco.com/c/en/us/support/docs/wireless-mobility/wireless-lan-wlan/91631-uwn-tacacs-config.html
2)https://supportforums.cisco.com/document/57301/wlc-and-acs-5x-tacacs-configuration-example-web-authentication
Thank you.
Hi,
If that works without command sets that’s fine.
Since these were my study notes, I may not had the correct understanding all the time 😉
HTH
Rasika
Thank you for response. This is very helpful resource for preparation. This website takes a very high place in my material list.
Great…Nice to hear my blog is useful to many others like you..
Rasika
Hi Rasiak,
I’m using the vWLC 8.0.100.0 with an ACS 5.2 and something is changed.
With the “role1=ALL” I can’t access. This is the log:
AAA Authentication Success for UserName:dimarziog User Type: UNKNOWN:0
I have tried every combination of tacacs attribute but It seem that now the WLC aspects an “user type”.
These are the results of my tests:
With “role1=MONITOR” I can access as read-only user. This is the log:
AAA Authentication Success for UserName:dimarziog User Type: MGMT USER(READ ONLY)
With “role1=ADMIN” + “role2=WLAN” + “role3=CONTROLLER” and so on… I can access with ALL privilege. This is the log:
AAA Authentication Success for UserName:dimarziog User Type: MGMT USER(READ WRITE)
With “role1=LOBBY” I can access as lobbyadmin. This is the log:
AAA Authentication Success for UserName:dimarziog User Type: MGMT USER(LOBBY ADMIN)
I have checked the configuration guide on Cisco site for the version 8.0 and It is not reported:
http://www.cisco.com/c/en/us/td/docs/wireless/controller/8-0/configuration-guide/b_cg80/b_cg80_chapter_0101010.html
have you gotten a solution for this?
Thank you! helped a lot!
Good to hear that 🙂
Hi Rasika,
great explanation. Thanks!
Thanks Zoran..
hi
After I Added entry’s for Tacacs in WLC, it is no longer accessible, with Tacacs user as well as with Local, Please help.
Make TACACS server unreachable from WLC & then you should able to access it using local credentials. Then you can remove config you did
HTH
Rasika
Nice post Rasika,
If i have management and service IPs defined on WLC, how can i force WLC sending TACACs request using management IP and not other? ACS is seeing request coming from service IP and i don’t want that.
Cheers
Does your ACS and WLC service port on same subnet ?
Usually WLC use its management interface IP for communication. Check service port configuration and see
HTH
Rasika
This is the best wireless reference website.
Thank you!!
Thank you for kind application Cecil
Rasika
In the GUI under Security > Prio Order > Mgmt User, the WLC says that “If LOCAL is selected as second priority then user will be authenticated against LOCAL only if first priority is unreachable.”
But this does not seem to be true, I have selected TACACS+ then LOCAL but I can login with both TACACS+ user as well as with the local user.
8.5.151.0
Thank you for your input, I am sure it will be useful for many others
Rasika
I have selected TACACS+ then LOCAL but I cant login to WLC via local user anymore. Version 8.3.143.0. I dont have access to ACS so if tacacs wont work I wont be able to connect to WLC.
Thanks for the great article!
A little note – WLCGuest and WLCUser rules screenshots are mixed up.
how to set a tacacs auth in standby WLC which is in SSO ?
In SSO, configuration only done on active unit. To access Active & Standby individually, you have RMI IPs, still you cannot do any config on standby unit itself
HTH
Rasika