Tags
Once a client station is discover a SSID (Probe Request/Response or listening to Beacons) it move to Join phase. This exchange comprise of at least 4 frames
1. Authentication (Request)
2. Authentication (Response)
3. Association Request
4. Association Response
The frame format of those Authentication frames are as shown below.(from page 136- CWAP Official Study Guide)
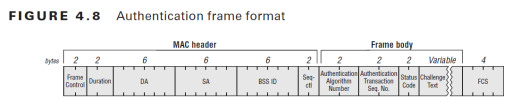 As you can see above, frame body of an Authentication Frame consist of the following filds
As you can see above, frame body of an Authentication Frame consist of the following filds
1. Authentication Algorithm Number – 0 for Open System & 1 for Shared Key
2. Authentication Transaction Sequence Number -Indicate current state of progress
3. Status Code – 0 for Success & 1 – Unspecified failures
4. Challenge Text – Used in Shared Key Authentiction frame 2 & 3
Below table summarize the authentication frame field values & usages.(from page 137- CWAP Official Study Guide)
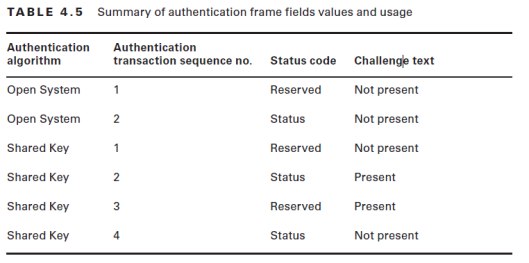 The initial purpose of the authentication frame is to validate the device type (verify that the requesting station has proper 802.11 capability to join the cell). This exchanged is based on simple two-frame (Auth Request & Auth Response) called Open System.
The initial purpose of the authentication frame is to validate the device type (verify that the requesting station has proper 802.11 capability to join the cell). This exchanged is based on simple two-frame (Auth Request & Auth Response) called Open System.
In IEEE 802.11-1997 standard included a WEP shared key exchange authentication mechanism called “Shared Key” where 4 authentication frame exchange. (when more complex authentication like 802.1X/EAP in place, Open System is used first & then complex method followed by Association frames). Below shows a Open System Authentication (note that all unicast frame ACK, so Auth frames get acknowledged)
Below diagrams show an Open System authentication frame exchange & associate packet capture.
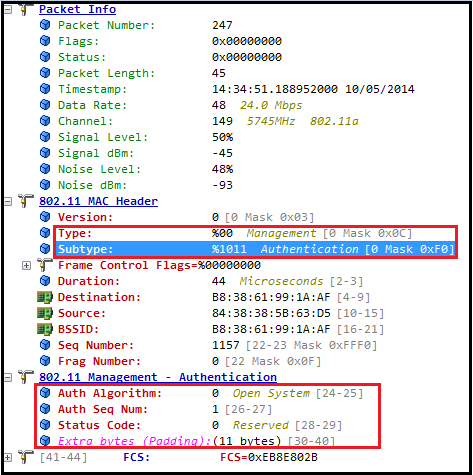
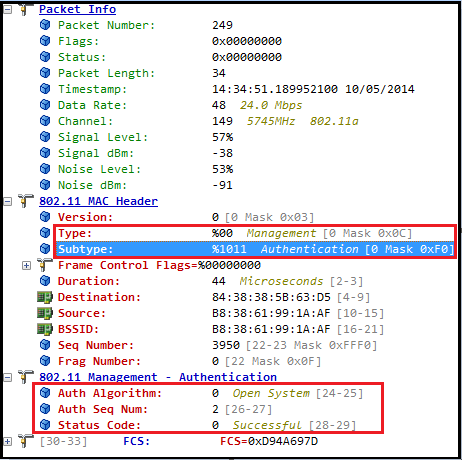
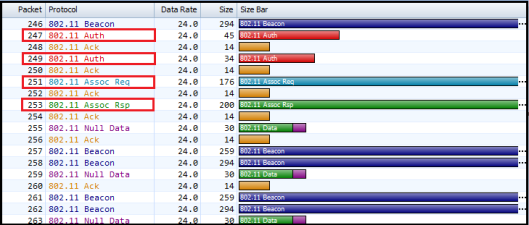 Here is the first Authentication Frame in this exchange (frame 247). You can see the Authentication Algorithm Number is 0 (indicate Open System). Auth Seq Number is 1 indicate this is the first Authentication Frame in the given exchange. Status code is Reserved for the first frame (refer the table above)
Here is the first Authentication Frame in this exchange (frame 247). You can see the Authentication Algorithm Number is 0 (indicate Open System). Auth Seq Number is 1 indicate this is the first Authentication Frame in the given exchange. Status code is Reserved for the first frame (refer the table above)
 Here is the 2nd Auth Frame (Auth Response) of the Open System frame exchange. As you can see here, Auth Seq Number is 2 indicating this is Auth Response frame. Also status code is 0 indicating successful Open System Authentication.
Here is the 2nd Auth Frame (Auth Response) of the Open System frame exchange. As you can see here, Auth Seq Number is 2 indicating this is Auth Response frame. Also status code is 0 indicating successful Open System Authentication.
 Even in a 802.1X/EAP Authentication, Always Open System Authentication occur first & then followed by EAP Authentication & 4 Way handshake prior to encrypt data. Here is 802.11r FT Association where 802.1X frame exchange after the Open System Authentication & Association completes.
Even in a 802.1X/EAP Authentication, Always Open System Authentication occur first & then followed by EAP Authentication & 4 Way handshake prior to encrypt data. Here is 802.11r FT Association where 802.1X frame exchange after the Open System Authentication & Association completes.
 If it is a Shared Key authentication, there will be 4 authentication frame exchanged as shown below.
If it is a Shared Key authentication, there will be 4 authentication frame exchanged as shown below.
 Here is a frame capture of this
Here is a frame capture of this Here is the first Authentication Frame in Shared Key exchange (Auth Seq No =1). As you can see this time Authentication Algorithm is 1 (indicate Shared Key)
Here is the first Authentication Frame in Shared Key exchange (Auth Seq No =1). As you can see this time Authentication Algorithm is 1 (indicate Shared Key)
 Here is the 2nd Auth Frame (Auth Seq No=2) . Note that this frame contain a “Challenge Text”. It is expected receiving device of this frame encrypt it using WEP & send it inside Auth frame 3.
Here is the 2nd Auth Frame (Auth Seq No=2) . Note that this frame contain a “Challenge Text”. It is expected receiving device of this frame encrypt it using WEP & send it inside Auth frame 3. Here is the 3rd Auth Frame in that exchange. You can see WEP encryption used
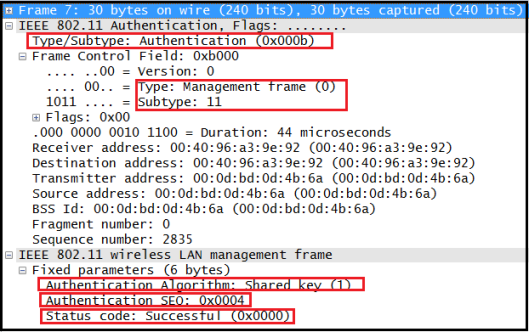
Here is the 3rd Auth Frame in that exchange. You can see WEP encryption used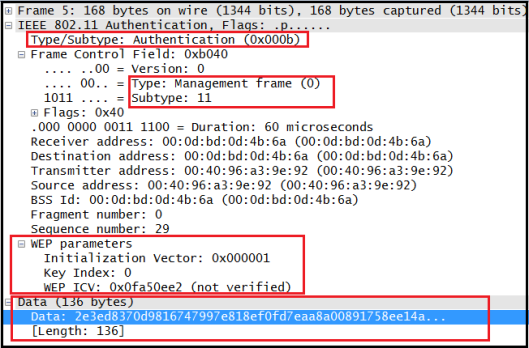 Here is the last frame (Auth Seq No =4) of Shared Key Authentication. Note that Status code=0 indicate Successful Authentication.
Here is the last frame (Auth Seq No =4) of Shared Key Authentication. Note that Status code=0 indicate Successful Authentication.
 References
References
1. CWAP Official Study Guide – Chapter 4
Related Posts
1. 802.11 Management Frame Types
2. 802.11 Mgmt – Beacon Frame
3. 802.11 Mgmt – Action Frames

Hey Rasika,
Good work with the WLAN packet explanation. I follow your blog religiously. I am not sure if you have used another visual tool wizshark (https://www.wizshark.net). You may want to give it a try and i would love to hear your feedback.
Drop me an email and i will set you up for a beta account.
Keep up the good work.
B Misra
Hi Misra,
Thank you for this.
I havn’t use that tool & greatly appreciate if you can setup a beta account for me. Would love to use that & give you feedback.
What is your email address to send the request
Rasika
Nice. Please send the request to me (bmisra at airtightnetworks.com). I will have it setup.
Thanks
Thank you.. I have sent you a request
“The initial purpose of the authentication frame is to validate the device type (verify that the requesting station has proper 802.11 capability to join the cell”
How done AP know the 11n capabilities with authentication frame exchange?
Based on HT capability & HT Information these two are present in the prob request and association request from station side mang frames.
Which tool is used in this explanation ? is it available for linux?
Hi
I used omnipeek
https://www.savvius.com/product/omnipeek/
It is a commercial product
HTH
Rasika
Hi Sir,
Wouldn´t you clarify the following?
I clear with Wi-Fi authentication, association, and 4-way handshake.
My mob is authenticated and associated with my router, when I go out of my home, I get disconnected. But it will be automatically connected when I come back to my home.
Could briefly explain what technical thing behid this, avoid the reentering of password again?
Is that reassociation request with a specific reassociation ID?
Thanks in advance
Hi Manesh,
After leaving the BSS (Basic service set), the station will be disconnected.
But, the station still does scanning to find the next BSS (Active/ Passive scanning) to associate. So, when reentering to the same BSS, it can choose the same AP to associate.
Here, It may send the auth and reassociation request or fresh association request to AP and the behaviour is based on the implementation on the Station side.
Already we have the password for the same AP. Then why we need to re-enter the password. Just we need to confirm the same BSS exists.
There is no reassociation ID kind of thing. reassociation frames almost similar to the association request.
Generally, In the roaming case Station sends the reassociation request.