Tags
There are two types of ACL available in WLC. CPU ACL & Interface ACL
Here are the basic rules for ACL on a WLC.
1. Direction : There are 3 directions. Inbound, Outbound and Any.These directions are taken from a position relative to the WLC & not the wireless client. CPU ACL needs to apply either inbound or any direction.
– Inbound: IP packets sourced from the wireless client are inspected to see if they match ACL lines
– Outbound:IP packets destined to the wireless client are inspected to see if they match ACL lines
– Any: IP packets sourced from the wireless client and destined to the wireless client are inspected to see if they match ACL lines. Any direction should only be used in specific situations where you want to block or allow a specific IP protocol or port in both directions.
2. Source/Destination with Mask : Mask in a WLC ACL is not like the wildcard or inverse mask uses in IOS ACL. In WLC ACL 255 means match exactly the octet, while 0 is a wildcard. (in otherwords mask bit 1 mean “exact match”, mask bit 0 for “ignore”
3. Protocol : Options are Any, TCP (6), UDP(17), ICMP (1), ESP (50). AH (51), GRE (47), IP-in-IP (4), EoIP(97), OSPF(89), Other (specify the protocol number).
4. Source/Destination Port : Can only be specified for TCP or UDP protocol. Range 0-65535.
5. DSCP : Allows you to specify DSCP values to match in the IP packet header.
6. Action : Deny or Permit. Remember that implicit deny any any rule exist here as well.
Keep in mind following restrictions in WLC ACL
1. You can define up to 64 ACL each with up to 64 rules.
2. You cannot log packets that matches ACL line (not like an IOS ACL)
3. IP packets (Ethertype[0x0800]) are the only packet inspected by the ACL. Any other type of packets cannot be blocked. eg ARP – 0x0806
4. ACL do not affect broadcast or Multicast traffic
5. ACLs cannot block access to WLC virtual IP address. Therefore DHCP cannot be blocked for wireless clients.
6.
You can configure ACL by choosing “Security -> Access Control Lists -> Access Control Lists”. Lets consider an example. Wireless client will be in 10.10.14.0/24 network & wired clients are in 192.168.1.0/24 network. CME IP is 10.10.205.20. Users in wireless subnet should not able to ping CME IP, but they should be able to ping any other network.
Below screenshots show how to define this. Tick “Enable Counters” to show the statistics

You can apply this per interface or per WLAN. Per WLAN ACL will override the interface ACL.
Here is the WLAN advanced option.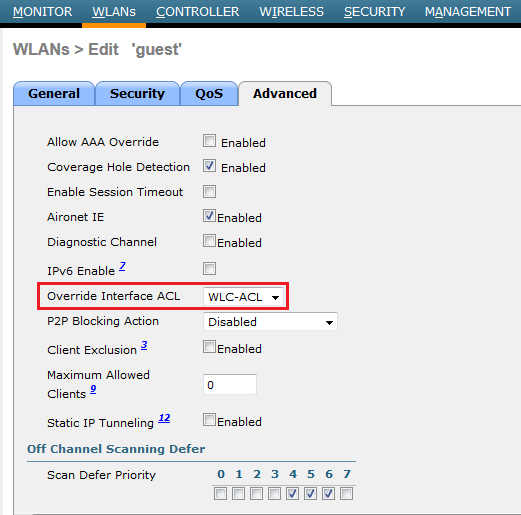
Here is the before applying ACL.
CME#sh ip int bri | ex un|dis
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 172.16.99.5 YES NVRAM up up
FastEthernet0/1 192.168.1.254 YES NVRAM up up
FastEthernet2/1 172.16.99.9 YES NVRAM up down
Loopback0 10.10.205.20 YES NVRAM up up
Loopback99 10.10.99.1 YES NVRAM up up
CME#ping 10.10.14.53 sou lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.14.53, timeout is 2 seconds:
Packet sent with a source address of 10.10.205.20
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/23/104 ms
I have applied this on WLAN itself. Here is after applying ACL onto WLAN. Since we block ICMP to loopback 0 IP you can ping this from another IP. Also keep in mind, in our test ICMP echo response packet will be get dropped when it comes from wireless client to AP (as we have applied deny inbound).
CME#ping 10.10.14.53 sou lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.10.14.53, timeout is 2 seconds: Packet sent with a source address of 10.10.205.20 ..... Success rate is 0 percent (0/5) ! CME#ping 10.10.14.53 sou lo99 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.10.14.53, timeout is 2 seconds: Packet sent with a source address of 10.10.99.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/19/84 ms
You can verify this using WLC CLI as well.
(WLC1) >show acl summary ACL Counter Status Enabled ---------------------------------------- ACL Name Applied -------------------------------- ------- WLC-ACL Yes ! (WLC1) >show acl detailed WLC-ACL Source Destination Source Port Dest Port Index Dir IP Address/Netmask IP Address/Netmask Prot Range Range DSCP Action Counter ------ --- ------------------------------- ------------------------------- ---- ----------- ----------- ----- ------- ----------- 1 In 10.10.14.0/255.255.255.0 10.10.205.20/255.255.255.255 1 0-65535 0-65535 Any Deny 5 2 In 10.10.14.0/255.255.255.0 0.0.0.0/0.0.0.0 1 0-65535 0-65535 Any Permit 14 3 Out 0.0.0.0/0.0.0.0 10.10.14.0/255.255.255.0 1 0-65535 0-65535 Any Permit 14 4 Any 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0 Any 0-65535 0-65535 Any Permit 77
If you are interested in CLI commands here are those. I think it is relatively easy to do this via GUI rather remember all these syntax for CLI.
config acl create WLC-ACL <- Create an ACL config acl counter start <- Enable Counters config acl rule add WLC-ACL 1 config acl rule destination address WLC-ACL 1 10.10.205.20 255.255.255.255 config acl rule protocol WLC-ACL 1 1 config acl rule direction WLC-ACL 1 in config acl rule source address WLC-ACL 1 10.10.14.0 255.255.255.0 config acl rule add WLC-ACL 2 config acl rule protocol WLC-ACL 2 1 config acl rule action WLC-ACL 2 permit config acl rule direction WLC-ACL 2 in config acl rule source address WLC-ACL 2 10.10.14.0 255.255.255.0 config acl rule add WLC-ACL 3 config acl rule destination address WLC-ACL 3 10.10.14.0 255.255.255.0 config acl rule protocol WLC-ACL 3 1 config acl rule action WLC-ACL 3 permit config acl rule direction WLC-ACL 3 out config acl rule add WLC-ACL 4 config acl rule action WLC-ACL 4 permit config acl rule add WLC-ACL 65 <- I think this is implicit rule as line65 config acl apply WLC-ACL <- Apply ACL to Data path ?? config wlan acl 4 WLC-ACL <- Apply ACL onto WLAN
If this is a CPU ACL you can apply it by using ” Security -> Access Control List -> CPU ACL” . I simply show the previous ACL (but it does not make any sense as CPU ACL looking at source/dest). You have to decide which traffic you want to block/ permit for WLC CPU. Remember that when CPU ACL is enabled via GUI it apply for both wireless & wired traffic. If you want to conditionally apply this rule you can use CLI “config acl cpu <acl-name> {wired|wireless|both}”
You can use “show rules”command to verify exising rules on a WLC. You can override these by CPU ACL if you use the same protocol/port numbers. This is shown partial list of the output of that command.
-------------------------------------------------------- Rule ID.............: 37 Ref count...........: 0 Precedence..........: 5010 Flags...............: 00000002 ( REJECT ) Service Info Service name........: SSH Protocol............: 6 Source port low.....: 0 Source port high....: 0 Dest port low.......: 22 Dest port high......: 22 Source IP range: IP Low.............: 0.0.0.0 IP High............: 0.0.0.0 Interface..........: ANY Destination IP range: IP Low.............: 192.0.2.1 IP High............: 192.0.2.1 Interface..........: ANY -------------------------------------------------------- Rule ID.............: 38 Ref count...........: 0 Precedence..........: 5010 Flags...............: 00000002 ( REJECT ) Service Info Service name........: TELNET Protocol............: 6 Source port low.....: 0 Source port high....: 0 Dest port low.......: 23 Dest port high......: 23 Source IP range: IP Low.............: 0.0.0.0 IP High............: 0.0.0.0 Interface..........: ANY Destination IP range: IP Low.............: 192.0.2.1 IP High............: 192.0.2.1 Interface..........: ANY
In CLI, you can use “show acl cpu” to view ACL applied to CPU. Also you can use “config acl cpu none” to remove any CPU ACL.
ACL can be defined for pre-web authentication & will see that in a separate post for “Web Authentication”
Here are some reference documents, Even though those are bit old give your some valuable information which is relevant to this topic.



In your access list example, why do we need second and third rules if have an explicit permit in the 4th rule?
Hi Rasika,
Have you ever seen the following log msg from the controller?. Any idea is well-received. thanks
2014-10-31 16:11:38 Local7.Warning 172.23.111.23 DC-WiFi-WLC1-3: *dtlArpTask: Oct 31 16:12:28.520: #DTL-4-ARP_NULL_SRC_IP: dtl_net.c:2693 Recv ARP Request with source IP as 0. Marking for Duplicate Addr Detection.
Hey Abraham,
Did you ever find a resolution to this error message? I’m experiencing the same error message on my WLC.
Same Here. If you find a solution, please share it here.
Rasika,
How would you block a specific multicast stream from the wired side from reaching a SSID?
Thanks
hi rasika, from the 2 ACL that you mentioned, which one is the PREAUTH ACL? thanks
The ACL is wrong
HI Jerome,
It is good if you point out the issue and correct it for others benefit (I am not saying all my blog posts are 100% accurate… as I am on a journey to learn wifi)
Rasika
Awesome explanation … as always
Hi!
When Peer-to-peer blocking (when users cant talk directly to each other without passing the WLC) is enabled, is it possible to block lets say SMB-traffic (139, 445 TCP and 137 and 138 UDP) between wireless users on the same subnet using ACL’s in WLC?
Great blog btw!
Try to use AVC & see
Hi Nayarasi,
I have 8510 WLC and i need to configure ACL to allow specific URLs. How can I do that.
Hey . I have assigned ip for CAPWAP tunnel eg 10.XXX.XX.XX/24. I want to secure my CAWAP tunnel from communicating or responding to any network device except connected AP to WLC. I am not sure what all things i have to add in ACL . CAPWAP is using VLAN 130 with ip range 10.130.xx.xx/24
i have made ACL as below :
ip access-list standard CAPWAP_ACL
permit 10.130.xxx.0 0.0.0.255
deny any log
And applied ACL on VLAN 130 interface at ifrom inside
But i am not sure i dont feel its correct , since any ip can ping to ca wap and still capwap can communicate with any other IP from the network.