In small wireless network (Autonomous) there may not be Radius server available for 802.1x authentication.In a situation like this you can configure one of your AAP as local authentication server. Then this AP can authenticate upto 50 clients using LEAP, EAP-FAST or MAC based authentication.
In this post we will configure AAP as local radius server to support LEAP authentication. I will create SSID called “data3 with vlan 14 – 10.10.14.0/24). In this first we will configure this on GUI & later on derive the CLI commands. I will use WPA2 key management method.
First of all you need to configure the vlan on the AAP1. You can do this in ” SERVICES -> VLAN” section. 
Next step is to configure an encryption method for this vlan. Since I am planning to use WPA2, I have to configure encryption as AES-CCMP. You can do this in ” SECURITY – > Encryption Manager” section.
Then you can create SSID & configure Authentication key management method (WPA2). You have to go to “SECURITY -> SSID Manager” section for this. You have to use client Authentication settings as ” Network EAP” in order to support LEAP. Key management configured as WPA2.

Now you have to configure Radius server, in this case we will pointing this to AAP itself. You can do this from ” SECURITY -> Server Manager” section. Authentication & Accounting port configured as 1812 & 1813. AAP BVI IP is configured as server IP & shared secret as “cisco”
Make sure you select the configured radius server as Default Server priority for EAP authentication. See below
Now you need to configure AAP as local radius server & specify the Authentication Protocol. In this example LEAP is sufficient, but configured others to familiar with CLI commands to enable those. Shared secret is used as “cisco”
Finally you can configure a local username & password for a client. I have configured one as “cisco/cisco”.
Now you can check this configuration with Anyconnect client.
Now we will look at CLI commands where we can achieve this. First of all you have to configure your basic AAP configurations as below.
hostname AAP1 ! interface Dot11Radio1.14 encapsulation dot1Q 14 bridge-group 14 ! interface Dot11Radio1.110 encapsulation dot1Q 110 native bridge-group 1 ! interface GigabitEthernet0.14 encapsulation dot1Q 14 bridge-group 14 ! interface GigabitEthernet0.110 encapsulation dot1Q 110 native bridge-group 1 ! interface BVI1 ip address 10.10.110.100 255.255.255.0 no ip route-cache ! ip default-gateway 10.10.110.3
Next step is to configure the SSID & configure authentication key management method. For LEAP to work properly with windows client you have to specify “Open Authentication with EAP Methods”. For Cisco Anyconnect “Network EAP” should be sufficient.
Also you have to configure Encryption to be used under radio interface. Since we are using WPA2 encryption should be AES-CCMP.
dot11 ssid data3 vlan 14 authentication open eap eap_methods authentication network-eap eap_methods authentication key-management wpa version 2 mbssid guest-mode ! interface Dot11Radio1 mbssid encryption vlan 14 mode ciphers aes-ccm ssid data3
Next you can configure RADIUS on AAP pointing to its own IP. “radius-server attribute 32 include-in-access-req format %h” will allow AP to send its system name in the NAS_ID attribute for authentication. Radius server group defined as “rad_eap” & it is called for login authentication.
aaa new-model radius-server host 10.10.110.100 auth-port 1812 acct-port 1813 key cisco radius-server attribute 32 include-in-access-req format %h ! aaa group server radius rad_eap server 10.10.110.100 auth-port 1812 acct-port 1813 aaa authentication login eap_methods group rad_eap aaa authorization exec default local
Finally you can configure AAP as local authenticator. You have to define all your local username/password for clients in this section. Also any other AAP use this AP as radius you have to specify other AAP IPs with secret key. In this example only single AP & one local user created for testing.
radius-server local nas 10.10.110.100 key cisco user cisco password cisco
That’s pretty much it & you can test with your Any Connect client now. You should see client get associated & you can check the details via CLI using “show dot11 association” command.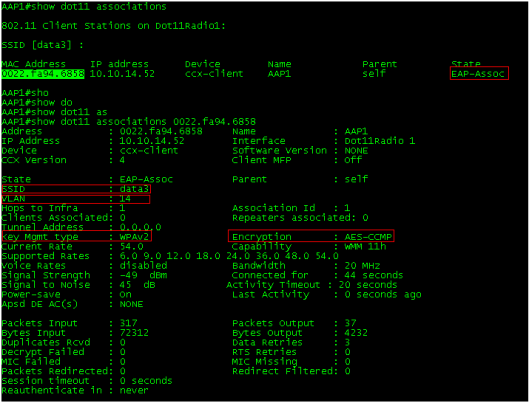
So for the exam I have to remember this CLI commands. Once you breakdown whole config in to simple sections it is much easier than I initially thought. We will look another example with multiple AAP & multiple user groups in next example.
Related Posts
1. Autonomous AP with WEP Security
2. Autonomous AP with WPA-PSK Security
3. Autonomous AP with LEAP Security
4. Autonomous AP with PEAP Security
5 Autonomous AP with EAP-FAST Security
6 Autonomous AP with EAP-TLS Security
7.
8.
9. Autonomous AP – QoS
10.




Good post Rasika! I only ever use the CLI for autonomous AP’s. GUI takes too long and is actually more confusing.
Thanks Nolan, I have very little practical experience with Autonomous deployment. Working hard to learn these topics & CLI commands which is required for the LAB exam.
will try this… both with my love.. GUI and hopefully my new love… CLI.. heheh
Hi
I know you will love CLI once you get basics. It’s powerful & reliable
HTH
Rasika
how to configure aronet to authentication with radius server(windows server 2012)? can you provide me this guide line and sample configuration?
Hi
Refer this post, I have used ACS as radius server.
I haven’t configure Windows 2012 as RADIUS & does not have sample config for that. If you google it you will find something useful on that
HTH
Rasika
Hi Rasika – well done. Your post is indeed very informative. However, after following your guide, it does not appear my local radius server is starting on my 3602i with the autonomous image running ap3g2-k9w7-xx.153-3.JAB. I have tried opening connections to 1812 and 1813 from my host and the connection is refused. I am wondering if there is a bug with this image. Do you have suggestions on how to further debug what exactly is going on with the local radius server or maybe to determine what the problem is? I am happy to provide my configuration as well.
Hi Kurt,
“debug radius local-server client” is a useful debug command on this case.
Also refer this document & see if that helps.
http://www.cisco.com/c/en/us/support/docs/wireless-mobility/wireless-lan-wlan/116580-configure-eapfast-00.html
HTH
Rasika
Hello Rasika, I have applied your configuration on my Aironet AP1231G, but my PC authentication is failed , this is the log mesage that appear when i tried to authenticate with the configured username and password:
———————————————————————————————————–
*Mar 1 03:56:01.967: AAA/BIND(0000002A): Bind i/f
*Mar 1 03:56:12.715: AAA/AUTHEN/PPP (0000002A): Pick method list ‘eap_methods’
*Mar 1 03:56:12.722: AAA/AUTHEN/PPP (0000002A): Pick method list ‘eap_methods’
*Mar 1 03:56:12.725: %DOT11-7-AUTH_FAILED: Station 645a.04c6.6bec Authentication failed
———————————————————————————————————–
I’m using the IOS: c1200-k9w7-mx.123-8.JA2
thank you in advance
Rasika, I’ve task to use IPV6 address in the Local Radius Server.
I’ve 2 autonomous APs::
1) 2600i (Root Bridge)
2) 3600E ( Non-Root Bridge)
Can you please help, The Radius Server is going ON/OFF and this associations are going up and down as well.
*Mar 1 03:18:07.179: %RADIUS-4-RADIUS_DEAD: RADIUS server 2001:10:20:14::10:16445,1646 is not responding.
*Mar 1 03:18:07.179: %RADIUS-4-RADIUS_ALIVE: RADIUS server 2001:10:20:14::10:16445,1646 is being marked alive.
____________________________________________________
Here’s the config:
interface BVI1
mac-address 1c6a.7ae2.7aab
ip address 10.0.0.10 255.255.255.0
ipv6 address dhcp
ipv6 address 2001:10:20:14::10/64
ipv6 address autoconfig
ipv6 enable
!
ip default-gateway 10.0.0.1
ip forward-protocol nd
ip http server
no ip http secure-server
ip http help-path http://www.cisco.com/warp/public/779/smbiz/prodconfig/help/eag
!
!
radius-server local
no authentication leap
no authentication mac
group APs
!
user 3600-E nthash 7 09196D5149553143582D57090E7C7E1611704653462725027C0F00075F2641370B
!
!
radius server 2600i-BR1
address ipv6 2001:10:20:14::10 auth-port 16445 acct-port 1646
key 7 110A1016141D
Rasika, its John again,
I hope you can advice me how I can use IPV6 in the Local Radius:
The problem with IPv6 is that, there is no “NAS” command for IPv6,
How can we make it work.
I’m getting the following error on the Supplicant :
*Mar 1 13:16:20.189: %DOT1X_SHIM-3-SUPP_START_FAIL: Unable to start supplicant on Dot11Radio1
Here is the Config:
________________________
Root Bridge:
________________________
!
! Last configuration change at 09:16:07 UTC Mon Mar 1 1993
version 15.3
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname Bridge-1
!
!
logging rate-limit console 9
no logging console
enable secret 5 $1$qUhn$4w3JgzUbGF3nbYrzPYLlO1
!
aaa new-model
!
!
aaa group server radius rad_eap
server name Bridge-1
!
aaa authentication login eap_methods group rad_eap
!
aaa session-id common
no ip source-route
no ip cef
!
dot11 syslog
!
dot11 ssid Bridge
vlan 15
authentication network-eap eap_methods
authentication key-management wpa version 2
guest-mode
!
username CISCO password 7 00271A150754
!
bridge irb
!
interface Dot11Radio0
no ip address
shutdown
antenna gain 0
station-role root
!
interface Dot11Radio0.15
encapsulation dot1Q 15 native
bridge-group 1
bridge-group 1 subscriber-loop-control
bridge-group 1 spanning-disabled
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
!
interface Dot11Radio1
no ip address
!
encryption vlan 15 mode ciphers aes-ccm
!
ssid Bridge
!
antenna gain 0
antenna a-antenna
peakdetect
dfs band 3 block
channel dfs
station-role root bridge
distance 2
!
interface Dot11Radio1.15
encapsulation dot1Q 15 native
bridge-group 1
bridge-group 1 spanning-disabled
!
interface GigabitEthernet0
no ip address
duplex auto
speed auto
!
interface GigabitEthernet0.15
encapsulation dot1Q 15 native
bridge-group 1
bridge-group 1 spanning-disabled
!
interface BVI1
mac-address 1c6a.7a42.6684
ip address 10.0.0.10 255.255.255.0
ipv6 address dhcp
ipv6 address 2000:10:10:14::10/64
ipv6 address autoconfig
ipv6 enable
!
ip default-gateway 10.0.0.1
ip forward-protocol nd
ip http server
no ip http secure-server
ip http help-path http://www.cisco.com/warp/public/779/smbiz/prodconfig/help/eag
!
!
radius-server local
group APs
!
user Bridge2 nthash 7 075A02141E593F5444425B5C547A7B740B636572435746535106090803045E5348 group APs
!
!
radius server Bridge-1
address ipv6 2001:10:10:14::10 auth-port 1645 acct-port 1646
key 7 110A1016141D
!
bridge 1 route ip
!
!
!
line con 0
line vty 0 4
transport input all
!
end
____________________________________
Non-Root Bridge
_____________________________________
!
hostname Bridge-2
!
!
logging rate-limit console 9
no logging console
enable secret 5 $1$613h$yjkAJPBrQ6TIAbbAB5VaD/
!
no aaa new-model
no ip source-route
no ip cef
!
!
!
!
dot11 syslog
!
dot11 ssid Bridge
vlan 200
authentication network-eap eap_methods
authentication key-management wpa version 2
!
!
!
eap profile FAST
method fast
!
!
!
dot1x credentials Bridge-2
username Bridge-2
password 7 070c285F4D06
!
username CISCO password 7 096F471A1A0A
!
!
bridge irb
!
!
!
interface Dot11Radio0
no ip address
shutdown
antenna gain 0
station-role root
!
interface Dot11Radio0.200
encapsulation dot1Q 200 native
bridge-group 1
bridge-group 1 subscriber-loop-control
bridge-group 1 spanning-disabled
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
!
interface Dot11Radio1
no ip address
!
encryption vlan 200 mode ciphers aes-ccm
!
ssid Bridge
!
antenna gain 0
antenna a-antenna
peakdetect
station-role non-root bridge
!
interface Dot11Radio1.200
encapsulation dot1Q 200 native
bridge-group 1
bridge-group 1 spanning-disabled
!
interface GigabitEthernet0
no ip address
duplex auto
speed auto
!
interface GigabitEthernet0.200
encapsulation dot1Q 200 native
bridge-group 1
bridge-group 1 spanning-disabled
!
interface BVI1
mac-address 74a2.e66c.9544
ip address 10.1.0.10 255.255.255.0
ipv6 address dhcp
ipv6 address autoconfig
ipv6 enable
!
ip default-gateway 10.1.0.1
ip forward-protocol nd
ip http server
no ip http secure-server
ip http help-path http://www.cisco.com/warp/public/779/smbiz/prodconfig/help/eag
!
!
bridge 1 route ip
!
!
!
line con 0
line vty 0 4
login local
transport input all
!
end
Hi John,
I have to play with IPv6 on this & then give some input
Rasika
Hi John,
I haven’t tested IPv6 with this. Let me see if I can set it up & see (as time permits)
HTH
Rasika
Hi,
I have one question .
When 2 clients associated to AP ,client-1 using WPA-TKIP encryption ,client-2 using WPA2-AES encryption .When client-1 tries to send data to client-2.is it possible to send data and how the encryption process carries between two clients.
excellent article, I have been hunting everywhere for a this type of guide, to test different flavours of EAP for analysis pcaps to get a better understanding of the EAP flavours.
Thank you Dave for appreciation.
Rasika