In this post we will see how to confiugre an Autonomous AP to authenticate users with external RADIUS server. I have used ACS v5.2 as my RADIUS Server. 1142N access point with IOS image c1140-k9w7-mx.124-25d.JA used for this exercise. Here is basic topology for the post.
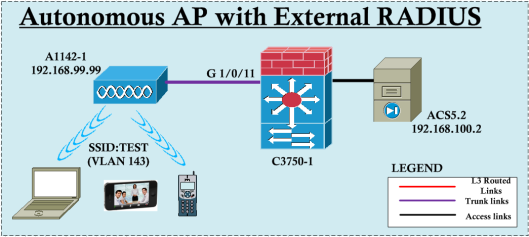 Here is the basic configuration of AP with open authentication & Switch. You need to make sure this configuration is working before proceeding to the RADIUS configuration. I used only Radio 1(5GHz) for simplicity.
Here is the basic configuration of AP with open authentication & Switch. You need to make sure this configuration is working before proceeding to the RADIUS configuration. I used only Radio 1(5GHz) for simplicity.
hostname C3750-1 <= Switch Configuration ! ip dhcp excluded-address 192.168.143.1 192.168.143.50 ip dhcp pool VLAN143 network 192.168.143.0 255.255.255.0 default-router 192.168.143.1 option 150 ip 10.10.205.20 domain-name mrn.com dns-server 192.168.200.1 ! interface GigabitEthernet1/0/11 switchport trunk encapsulation dot1q switchport trunk native vlan 999 switchport trunk allowed vlan 143,999 switchport mode trunk ! interface Vlan100 ip address 192.168.100.1 255.255.255.0 ! interface Vlan143 ip address 192.168.143.1 255.255.255.0 ! interface Vlan999 ip address 192.168.99.1 255.255.255.0 hostname A1142-1 <= AP Configuration ! dot11 ssid TEST vlan 143 authentication open guest-mode ! interface Dot11Radio1 ssid TEST ! interface Dot11Radio1.143 encapsulation dot1Q 143 bridge-group 143 ! interface Dot11Radio1.999 encapsulation dot1Q 999 native bridge-group 1 ! interface GigabitEthernet0.143 encapsulation dot1Q 143 bridge-group 143 ! interface GigabitEthernet0.999 encapsulation dot1Q 999 native bridge-group 1 ! interface BVI1 ip address 192.168.99.99 255.255.255.0 ip default-gateway 192.168.99.1
When configuring RADIUS for any IOS device, here are the 3 steps you needs to follow.
1. Define the RADIUS server/or servers.
2. Create a RADIUS Server Group (listing defined servers).
3. Create a method-list, that points to the RADIUS group created.
When working with the RADIUS, you could be easily locked yourself out unless you do the required configuration 100% correct. Therefore always good practice to have a safe way of accessing the IOS device, even if you made a mistake. So before starting rest of the configuration we will configure Console Line not to do any authentications.
line con 0 no login authentication
First command to enter is “aaa new-model“. Then you can define the radius server configuration as shown below. I have used “Cisco123” as shared key & timeout value of 10s (by default 5s)
A1142-1(config)#radius-server ? accounting Accounting information configuration attribute Customize selected radius attributes authorization Authorization processing information backoff Retry backoff pattern(Default is retransmits with constant delay) cache AAA auth cache default server group challenge-noecho Data echoing to screen is disabled during Access-Challenge configure-nas Attempt to upload static routes and IP pools at startup dead-criteria Set the criteria used to decide when a radius server is marked dead deadtime Time to stop using a server that doesn't respond directed-request Allow user to specify radius server to use with `@server' domain-stripping Strip the domain from the username host Specify a RADIUS server key encryption key shared with the radius servers local Configure local RADIUS server optional-passwords The first RADIUS request can be made without requesting a password retransmit Specify the number of retries to active server retry Specify how the next packet is sent after timeout. source-ports source ports used for sending out RADIUS requests timeout Time to wait for a RADIUS server to reply transaction Specify per-transaction parameters unique-ident Higher order bits of Acct-Session-Id vsa Vendor specific attribute configuration radius-server host 192.168.100.2 auth-port 1812 acct-port 1813 key Cisco123 1D5A5E57 radius-server timeout 10
As a 2nd Step, you can define the RADIUS server group & then list the server you defined. I have used “RAD_GRP” as my RADIUS group name.
A1142-1(config)#aaa group server radius RAD_GRP A1142-1(config-sg-radius)#? RADIUS Server-group commands: accounting Specify a RADIUS attribute filter for accounting attribute Customize selected radius attributes authorization Specify a RADIUS attribute filter for authorization backoff Retry backoff pattern (Default is retransmits with constant delay) cache cached DB profile configuration deadtime Specify time in minutes to ignore an unresponsive server default Set a command to its defaults exit Exit from RADIUS server-group configuration mode ip Internet Protocol config commands no Negate a command or set its defaults server Specify a RADIUS server server-private Define a private RADIUS server (per group) A1142-1(config-sg-radius)#server 192.168.100.2 auth-port 1812 acct-port 1813
As final step, you can define method lists & pointing it to the RADIUS group you defined & apply it to a WLAN (or SSID) created. Method List name “EAP_MTD” used in my example. Additionally I have configured WPA2/AES for added security.
A1142-1(config)#aaa authentication login EAP_MTD group RAD_GRP ! A1142-1(config)#dot11 ssid TEST A1142-1(config-ssid)# authentication open eap EAP_MTD A1142-1(config-ssid)# authentication network-eap EAP_MTD A1142-1(config-ssid)# authentication key-management wpa version 2 ! A1142-1(config)#interface Dot11Radio1 A1142-1(config-if)# encryption vlan 143 mode ciphers aes-ccm
That’s pretty much the configuration on the AP itself. You have to configure ACS5.2. In ACS you have to configure the shared secret for this AP. Either you can individually configure each NAS devices or you can configure a Default Network Device which will be applicable to any device connecting to ACS. I have used default device method.
 Then make sure you have created a Username/Password for testing. In my example I have used local user (test/test123) within ACS. Also if you want to do EAP-TLS make sure you installed necessary certificates on ACS & Test Client (not explain in this post) & they are correctly listed in Certificate Authority Section.
Then make sure you have created a Username/Password for testing. In my example I have used local user (test/test123) within ACS. Also if you want to do EAP-TLS make sure you installed necessary certificates on ACS & Test Client (not explain in this post) & they are correctly listed in Certificate Authority Section.
 For TLS to work you need to have certificates installed & TLS request pointing to the Identity Store created for TLS.
For TLS to work you need to have certificates installed & TLS request pointing to the Identity Store created for TLS.
 I have defined an Identity Store for all EAP-TLS requests.
I have defined an Identity Store for all EAP-TLS requests.
 Then I have defined a custom attribute named NAS-IP & called “NAS-IP-Address” attribute in RADIUS-IETF dictionary.For simple scenario like our case, we can use default permit rule without any custom policy, but if you want to do some filtering based on RADIUS request coming from this NAS IP, then this method is very useful.
Then I have defined a custom attribute named NAS-IP & called “NAS-IP-Address” attribute in RADIUS-IETF dictionary.For simple scenario like our case, we can use default permit rule without any custom policy, but if you want to do some filtering based on RADIUS request coming from this NAS IP, then this method is very useful.
 Next to make sure all required protocol is permitted though ACS. (Access Policies -> Default Network Access -> Allowed Protocols)
Next to make sure all required protocol is permitted though ACS. (Access Policies -> Default Network Access -> Allowed Protocols)
 In the Access Policies -> Default Network Access -> Identity section, you have to specify if the request is EAP-TLS, use the Identity Store defined for TLS. By default all request go to Internal Users Identity Store. So I have created a rule based selection to pointing all TLS to go for “CCIE-TLS-Internal” identity store created in a previous step.
In the Access Policies -> Default Network Access -> Identity section, you have to specify if the request is EAP-TLS, use the Identity Store defined for TLS. By default all request go to Internal Users Identity Store. So I have created a rule based selection to pointing all TLS to go for “CCIE-TLS-Internal” identity store created in a previous step.
Then you can create a policy by adding the custom attribute created (NAS-IP) in to Custom Condition. You can do this by hitting “Customize” button under Access Policies -> Default Network Access -> Authorization section. (Some other attributes aslo shown, but not relevant to this example)
 Here is the policy looks like. Simply give “Permit Access” for any RADIUS request coming from NAS-IP 192.168.99.99 (Our Access Point IP)
Here is the policy looks like. Simply give “Permit Access” for any RADIUS request coming from NAS-IP 192.168.99.99 (Our Access Point IP)
 Once you save the configuration, it is all ready to testing. I have used a Laptop as EAP-TLS client & iPhone5 as PEAP client. You can see the client associations on AP CLI
Once you save the configuration, it is all ready to testing. I have used a Laptop as EAP-TLS client & iPhone5 as PEAP client. You can see the client associations on AP CLI
A1142-1#show dot11 associations 802.11 Client Stations on Dot11Radio1: SSID [TEST] : MAC Address IP address Device Name Parent State 0022.fa94.6858 192.168.143.55 ccx-client A1142-1 self EAP-Assoc 04f7.e4ea.5b66 192.168.143.54 unknown - self EAP-Assoc A1142-1#show dot11 associations 0022.fa94.6858 Address : 0022.fa94.6858 Name : A1142-1 IP Address : 192.168.143.55 Interface : Dot11Radio 1 Device : ccx-client Software Version : NONE CCX Version : 4 Client MFP : Off State : EAP-Assoc Parent : self SSID : TEST VLAN : 143 Hops to Infra : 1 Association Id : 2 Clients Associated: 0 Repeaters associated: 0 Tunnel Address : 0.0.0.0 Key Mgmt type : WPAv2 Encryption : AES-CCMP Current Rate : 54.0 Capability : WMM 11h Supported Rates : 6.0 9.0 12.0 18.0 24.0 36.0 48.0 54.0 Voice Rates : disabled Bandwidth : 20 MHz Signal Strength : -49 dBm Connected for : 90 seconds Signal to Noise : 48 dB Activity Timeout : 20 seconds Power-save : On Last Activity : 0 seconds ago Apsd DE AC(s) : NONE Packets Input : 649 Packets Output : 179 Bytes Input : 129364 Bytes Output : 35033 Duplicates Rcvd : 1 Data Retries : 3 Decrypt Failed : 0 RTS Retries : 0 MIC Failed : 0 MIC Missing : 0 Packets Redirected: 0 Redirect Filtered: 0 Session timeout : 0 seconds Reauthenticate in : never A1142-1#show dot11 associations 04f7.e4ea.5b66 Address : 04f7.e4ea.5b66 Name : NONE IP Address : 192.168.143.54 Interface : Dot11Radio 1 Device : unknown Software Version : NONE CCX Version : NONE Client MFP : Off State : EAP-Assoc Parent : self SSID : TEST VLAN : 143 Hops to Infra : 1 Association Id : 1 Clients Associated: 0 Repeaters associated: 0 Tunnel Address : 0.0.0.0 Key Mgmt type : WPAv2 Encryption : AES-CCMP Current Rate : m7.- Capability : WMM 11h Supported Rates : 6.0 9.0 12.0 18.0 24.0 36.0 48.0 54.0 m0. m1. m2. m3. m4. m5. m6. m7. Voice Rates : disabled Bandwidth : 20 MHz Signal Strength : -44 dBm Connected for : 2952 seconds Signal to Noise : 53 dB Activity Timeout : 57 seconds Power-save : On Last Activity : 1 seconds ago Apsd DE AC(s) : NONE Packets Input : 469 Packets Output : 97 Bytes Input : 26761 Bytes Output : 9326 Duplicates Rcvd : 0 Data Retries : 1 Decrypt Failed : 0 RTS Retries : 0 MIC Failed : 0 MIC Missing : 0 Packets Redirected: 0 Redirect Filtered: 0 Session timeout : 0 seconds Reauthenticate in : never
In ACS as well you can monitor the successful authentications of these clients. Here is the “Monitoring & Reports -> Launching Monitoring & Report Viewer-> RADIUS Authentication” results.
 If you want to look details you can click the “Magnify Glass” icon. This is the best way of troubleshooting if clients connection is not successful. It will give the failure reason & you be directed to the right direction in troubleshooting. Here is a part of PEAP authentication came from my iPhone5 client.
If you want to look details you can click the “Magnify Glass” icon. This is the best way of troubleshooting if clients connection is not successful. It will give the failure reason & you be directed to the right direction in troubleshooting. Here is a part of PEAP authentication came from my iPhone5 client.
 Hope this is useful for anyone wanted to play with an Autonomous AP & external RADIUS for authentication.
Hope this is useful for anyone wanted to play with an Autonomous AP & external RADIUS for authentication.


Hi Nayarasi, One question Is VLAN999 a non-routable vlan? ACS5.2 (192.168.100.2) need to access via L3 AP 192.168.99.99. Thanks JT Date: Wed, 13 Nov 2013 20:39:22 +0000 To: jose_tomas_perez@hotmail.com
No, It is a routable vlan as AP (192.168.99.99) should be able to communicate with ACS (192.168.100.2)
HTH
Rasika
Nice!! My friend
Thanks Daniel
Network EAP = LEAP. Open with EAP = Any other EAP.
So You probably do not want to use LEAP anymore
can we do this config with ISE
Yes, you should be able to use ISE as external radius
Rasika
thank you very much, can you help me authenticate guest users using web authentication on cisco 3602 autonomous access point with cisco ISE 2.3
We have a mixed environment of AAP and LAP. I tried using ISE as a Radius server with Autonomous AP’s 1231G with no success
Also in ISE it seems like *Require Message-Authenticator for all Radius Requests cannot be disabled. I tried to uncheck this box thinking if this is something causing the issue
Any thoughts would be helpful
Hi Ryan,
I do not have exact AP model to test. Did you try the latest software of that AP model. Since it is EoL , you may not even able to download
Rasika
can anyone help, i have a cisco air-cap2602i-e-k9 and need the controller software, to clear it and set it up on my home network?
Here you find some infos to convert a Cisco AP for home network usw. and example configurations:
https://administrator.de/en/cisco-wlan-access-point-1142n-and-2702-3702-for-soho-use-901293552.html