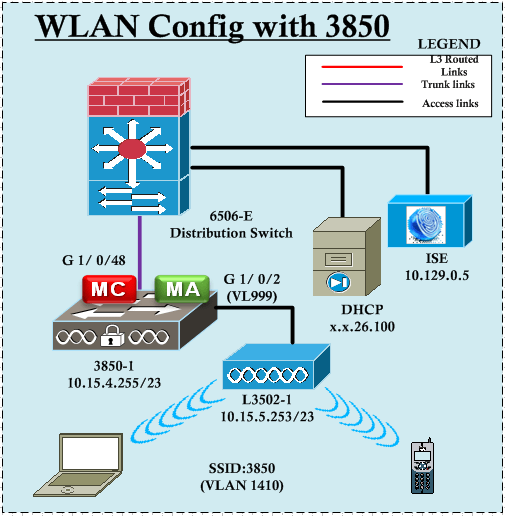
In this post we will see how to configure 802.1x WLAN with 3850. I have used ISE v1.2 as my radius server. Here is the topology for the post
 when configuring RADIUS on a IOS device, it is 3 step process
when configuring RADIUS on a IOS device, it is 3 step process
1. Define RADIUS server or servers.
2. Define a RADIUS group or groups (listing number of RADIUS server within that).
3. Define a method list that points to one of the group defined.
Let’s define the RADIUS server first. You need to enter “aaa new-model” command prior to any RADIUS configs. As you can see below, it will add automatically “aaa session-id common” command as well.
3850-1(config)#aaa new-model 3850-1#sh archive config differences nvram:startup-config system:running-config !Contextual Config Diffs: +aaa new-model +aaa session-id common
Here how you can define a RADIUS server
3850-1(config)#radius server ? WORD Name for the radius server configuration 3850-1(config)#radius server ISE-DEV ? <cr> 3850-1(config)#radius server ISE-DEV 3850-1(config-radius-server)#? RADIUS server sub-mode commands: address Specify the radius server address automate-tester Configure server automated testing. backoff Retry backoff pattern(Default is retransmits with constant delay) exit Exit from RADIUS server configuration mode key Per-server encryption key no Negate a command or set its defaults non-standard Attributes to be parsed that violate RADIUS standard pac Protected Access Credential key retransmit Number of retries to active server (overrides default) timeout Time to wait (in seconds) for this radius server to reply (overrides default) 3850-1(config-radius-server)#address ? ipv4 IPv4 Address ipv6 IPv6 Address 3850-1(config-radius-server)#address ipv4 ? Hostname or A.B.C.D IPv4 Address of radius server 3850-1(config-radius-server)#address ipv4 10.129.0.5 ? acct-port UDP port for RADIUS accounting server (default is 1646) alias 1-8 aliases for this server (max. 8) auth-port UDP port for RADIUS authentication server (default is 1645) <cr> 3850-1(config-radius-server)#address ipv4 10.129.0.5 auth-port 1812 acct-port 1813 ? <cr> 3850-1(config-radius-server)#address ipv4 10.129.0.5 auth-port 1812 acct-port 1813 3850-1(config-radius-server)#key Cisco123 3850-1(config-radius-server)#exit
Next we will define a group called “RAD-GRP”
3850-1(config)#aaa group server ? ldap Ldap server-group definition radius Radius server-group definition tacacs+ Tacacs+ server-group definition 3850-1(config)#aaa group server radius ? WORD Server-group name 3850-1(config)#aaa group server radius RAD-GRP 3850-1(config-sg-radius)#? RADIUS Server-group commands: accounting Specify a RADIUS attribute filter for accounting attribute Customize selected radius attributes authorization Specify a RADIUS attribute filter for authorization backoff Retry backoff pattern (Default is retransmits with constant delay) cache cached DB profile configuration deadtime Specify time in minutes to ignore an unresponsive server default Set a command to its defaults domain-stripping Strip the domain from the username exit Exit from RADIUS server-group configuration mode ip Internet Protocol config commands ipv6 IPv6 config commands key-wrap Configure RADIUS key-wrap feature load-balance Server group load-balancing options. mac-delimiter MAC Delimiter for Radius Compatibility Mode no Negate a command or set its defaults server Specify a RADIUS server server-private Define a private RADIUS server (per group) subscriber Configures MAC Filtering RADIUS Compatibility mode throttle Throttle requests to radius server 3850-1(config-sg-radius)#server ? Hostname or A.B.C.D IP address of RADIUS server name Name of radius server 3850-1(config-sg-radius)#server name ISE-DEV ? <cr> 3850-1(config-sg-radius)#server name ISE-DEV 3850-1(config-sg-radius)#exit 3850-1(config)#
Next step is to define method lists.
3850-1(config)#aaa ? accounting Accounting configurations parameters. attribute AAA attribute definitions authentication Authentication configurations parameters. authorization Authorization configurations parameters. cache AAA cache definitions common-criteria AAA Common Criteria configuration Authorization configuration parameters. dnis Associate certain AAA parameters to a specific DNIS number group AAA group definitions local AAA Local method options max-sessions Adjust initial hash size for estimated max sessions memory AAA memory parameters nas NAS specific configuration new-model Enable NEW access control commands and functions.(Disables OLD commands.) password Configure password/secret related settings pod POD processing policy AAA policy parameters server Local AAA server service-profile Service-Profile parameters session-id AAA Session ID traceback Traceback recording user AAA user definitions 3850-1(config)#aaa authentication ? arap Set authentication lists for arap. attempts Set the maximum number of authentication attempts banner Message to use when starting login/authentication. dot1x Set authentication lists for IEEE 802.1x. enable Set authentication list for enable. eou Set authentication lists for EAPoUDP fail-message Message to use for failed login/authentication. login Set authentication lists for logins. onep Set authentication lists for ONEP password-prompt Text to use when prompting for a password ppp Set authentication lists for ppp. sgbp Set authentication lists for sgbp. suppress Do not send access request for a specific type of user. username-prompt Text to use when prompting for a username 3850-1(config)#aaa authentication dot1x ? WORD Named authentication list (max 31 characters, longer will be rejected). default The default authentication list. 3850-1(config)#aaa authentication dot1x LTU-DOT1X group RAD-GRP
Since you are using Authentication, Authorization & Accounting you can define a method list for those as well.
3850-1(config)#aaa authorization ? auth-proxy For Authentication Proxy Services cache For AAA cache configuration commands For exec (shell) commands. config-commands For configuration mode commands. configuration For downloading configurations from AAA server console For enabling console authorization credential-download For downloading EAP credential from Local/RADIUS/LDAP exec For starting an exec (shell). multicast For downloading Multicast configurations from an AAA server network For network services. (PPP, SLIP, ARAP) onep For ONEP authorization service policy-if For diameter policy interface application. prepaid For diameter prepaid services. radius-proxy For proxying radius packets reverse-access For reverse access connections subscriber-service For iEdge subscriber services (VPDN etc) template Enable template authorization 3850-1(config)#aaa authorization network LTU-AUTH group RAD-GRP 3850-1(config)#aaa accounting network LTU-DOT1X start-stop group RAD-GRP
If you want to RADIUS server to override authorization values, in the global config you have to enable it. In this post we will not use this AAA override feature.
3850-1(config)#aaa server radius ? dynamic-author Local server profile for RFC 3576 support policy-device Local server profile for RADIUS External Policy Delegation client proxy Local server profile for RADIUS proxy clients sesm Local server profile for a SESM client 3850-1(config)#aaa server radius dynamic-author 3850-1(config-locsvr-da-radius)#? RADIUS Application commands: auth-type Specify the server authorization type client Specify a RADIUS client default Set a command to its defaults domain Username domain options exit Exit from RADIUS application configuration mode ignore Override behaviour to ignore certain parameters no Negate a command or set its defaults port Specify port on which local radius server listens server-key Encryption key shared with the radius clients 3850-1(config-locsvr-da-radius)#client 10.129.0.5 ? server-key Specify a RADIUS client server-key vrf Virtual Routing/Forwarding parameters <cr> 3850-1(config-locsvr-da-radius)#client 10.129.0.5 server-key Cisco123 3850-1(config-locsvr-da-radius)#auth-type ? all Matches when all attributes match any Matches when all sent attributes match session-key Matches with session key attribute only 3850-1(config-locsvr-da-radius)#auth-type any 3850-1(config-locsvr-da-radius)#exit
Before you move on, you need to make sure 802.1x globally enable on your 3850. “dot1x system-auth-control” command will do this for you.
3850-1(config)#dot1x system-auth-control
In summary here are the config lines we have added so far.
3850-1#sh archive config differences nvram:startup-config system:running-config !Contextual Config Diffs: +aaa new-model +dot1x system-auth-control +aaa group server radius RAD-GRP +server name ISE-DEV +aaa authentication dot1x LTU-DOT1X group RAD-GRP +aaa authorization network LTU-AUTH group RAD-GRP +aaa accounting network LTU-DOT1X start-stop group RAD-GRP +aaa server radius dynamic-author +client 10.129.0.5 server-key Cisco123 +auth-type any +aaa session-id common +radius server ISE-DEV +address ipv4 10.129.0.5 auth-port 1812 acct-port 1813 +key Cisco123
Now we will configure ISE to add this 3850 as client for that RADIUS server. You can add individual devices by navigating to “Administration > Network Resources > Network Devices”. In this example I have used “Default Device” so I do not want to individually add these devices. I have used “Cisco123” which is the shared-key used in 3850 configuration.
 Also to test, I have configured a local user called “user1” with password “Cisco123” by navigating to “Administration > Identity Management > Identities > User” as shown below.
Also to test, I have configured a local user called “user1” with password “Cisco123” by navigating to “Administration > Identity Management > Identities > User” as shown below.
 By default most of the EAP protocols are allowed by ISE. You can verify the allow protocol list by navigating “Policy > Policy Elements > Results > Authentication > Allowed Protocols > Default Network Access”
By default most of the EAP protocols are allowed by ISE. You can verify the allow protocol list by navigating “Policy > Policy Elements > Results > Authentication > Allowed Protocols > Default Network Access”
 Then you can define the authentication method for WLAN users. I have defined a new rule for dot1x called “LTU-DOT1x”
Then you can define the authentication method for WLAN users. I have defined a new rule for dot1x called “LTU-DOT1x”
 You should select allow protocol as “Default Network Access” & save the policy.
You should select allow protocol as “Default Network Access” & save the policy.
Let’s configure the SSID called “3850” for dot1x authentication. Remember that once you create a new SSID it will be automatically config with WPA2/AES with dot1x. We will point to “LTU-DOT1X” authentication method list we created.
wlan 3850 17 3850
client vlan WLN-STD-6
security dot1x authentication-list LTU-DOT1X
no shutdown
Since we created WLAN-ID greater than 16, will create the AP group and map SSID to the required vlan interface. Finally add the AP on to the AP group as shown below.
3850-1(config)#ap group 3850 3850-1(config-apgroup)#wlan 3850 3850-1(config-wlan-apgroup)#vlan WLN-STD-6 ! 3850-1#ap name L3502-1 ap-groupname 3850 Changing the AP's group name will cause the AP to reboot. Are you sure you want to continue? (y/n)[y]: y
Now if you connect to the SSID with the credential we created on ISE, you should be able to join the network.
 You can monitor the client connection details via ISE or 3850 CLI.
You can monitor the client connection details via ISE or 3850 CLI.
3850-1#sh wireless client summary Number of Local Clients : 3 MAC Address AP Name WLAN State Protocol -------------------------------------------------------------------------------- 04f7.e4ea.5b66 L3502-1 17 UP 11n(5) 2c54.2dea.f4ea L3502-1 17 AUTHENTICATING 11a a088.b435.c2f0 L3502-1 17 UP 11n(5) 3850-1#show wireless client mac-address a088.b435.c2f0 detail Client MAC Address : a088.b435.c2f0 Client Username : user1 AP MAC Address : 2c3f.382b.5700 AP Name: L3502-1 AP slot : 1 Client State : Associated Wireless LAN Id : 17 Wireless LAN Name: 3850 BSSID : 2c3f.382b.570f Connected For : 1512 secs Protocol : 802.11n - 5 GHz Channel : 64 Client IIF-ID : 0xc9c900000000a6 ASIC : 0 IPv4 Address : 10.141.99.247 IPv6 Address : Unknown Association Id : 2 Authentication Algorithm : Open System Status Code : 0 Client CCX version : 4 Client E2E version : 1 Re-authentication Timeout : 297 (1801) Input Policy Name : unknown Input Policy State : None Output Policy Name : unknown Output Policy State : None 802.1P Priority Tag : Not supported WMM Support : Enabled U-APSD Support : Disabled Power Save : ON Current Rate : m15 Supported Rates : 6.0,9.0,12.0,18.0,24.0,36.0,48.0,54.0,6.0,9.0,12.0,18.0,24.0,36.0,48.0,54.0 Mobility State : Local Mobility Move Count : 0 Security Policy Completed : Yes Policy Manager State : RUN Policy Manager Rule Created : Yes NPU Fast Fast Notified : Yes Last Policy Manager State : L2AUTHCOMPLETE Client Entry Create Time : 1461570 seconds Policy Type : WPA2 Authentication Key Management : 802.1x Encryption Cipher : CCMP (AES) Management Frame Protection : No Protected Management Frame - 802.11w : No EAP Type : PEAP Interface : WLN-STD-6 VLAN : 1410 Quarantine VLAN : 0 Access VLAN : 1410 WFD capable : No Manged WFD capable : No Cross Connection capable : No Support Concurrent Operation : No Client Capabilities CF Pollable : Not implemented CF Poll Request : Not implemented Short Preamble : Not implemented PBCC : Not implemented Channel Agility : Not implemented Listen Interval : 90 Fast BSS Transition : Not implemented Fast BSS Transition Details : Client Statistics: Number of Bytes Received : 459653 Number of Bytes Sent : 17967 Number of Packets Received : 4204 Number of Packets Sent : 336 Number of EAP Id Request Msg Timeouts : 0 Number of EAP Request Msg Timeouts : 0 Number of EAP Key Msg Timeouts : 0 Number of Data Retries : 4 Number of RTS Retries : 0 Number of Duplicate Received Packets : 2 Number of Decrypt Failed Packets : 0 Number of Mic Failured Packets : 0 Number of Mic Missing Packets : 0 Number of Policy Errors : 0 Radio Signal Strength Indicator : -49 dBm Signal to Noise Ratio : 46 dB Assisted-Roaming Prediction List: Nearby AP Statistics: L3502-1(slot1) antenna0: 7 seconds ago -59 dBm antenna1: 7 seconds ago -52 dBm
Below reference document guides you if you want to do a similar thing via GUI
Cisco Doc ID 116600
Related Posts
1. Getting Started with 3850
2. WLAN configs with 3850 – Part 1
3. 3850 Password Recovery
4. Converged Access Mobility
5. 3850- Flexible Netflow
6. Wireshark Capture in 3850



Interesting configuration.
I have a question concerning ISE. Is it free to use in a lab environnement ?
Is there a kind of demo license or something similar ?
Thanks
You can use evaluation copy of ISE which is valid for 90 days. I have used it for my lab environment.
HTH
Rasika
You could also use Aruba’s ClearPass Radius on a 90 day trail to compare it to ISE. As for the 3850 doing wireless outside of a few APs or a lab – the architecture doesn’t make much sense. Add up the roaming time and do a packet trace of the flow between the anchor switch you first connect to an AP on and any other switch with APs – especially ones outside the mobility domain and it starts to look pretty ridiculous. Stick with centralized controllers or go cloud based.
Hi Chris,
Thanks for the feedback.. We do have clearpass Radius for our Guest Wireless. Never know it will be replaced by ISE down the track.(within 1-2 years).
We are 99% cisco shop & not sure whether any other vendor solution will fit in to it considering the size of the environment.
Regarding the CA architecture, I do not agree with you..(Yes I understand Cisco & Aruba are highlighting drawbacks of each other). End of the day based on the value, these products bring to customer, they will choose the vendor.
Rasika
Hi Nayarasi,
We are deploying a Guest Wireless with Clearpass, but we cannot get it working 😦
We have 5760 controller and we are going yo use ClearPass as the Radius server for authentication and CoA. The problem is that the CoA seems not bee working between the controller and the radius.
We get an url-redirect back from the Clearpass (see below), but the client is never redirected to that url.
Feb 18 09:15:36.263: RADIUS: Cisco AVpair [1] 77 “url-redirect=https://clearpass01.domain.com/guest/test_login.php?mac=60:67:20:f6:41:a0”
Do you have any ideas?
I don’t know if this blogg could be used for that, but I’ve been with that many days and I have no clue what could it be.
Thanks and congratulations for your blogg.
Marco
Hi,
I was just wondering can I use the 3850 WLC as a stand alone local user account?
Example
User connects to SSID
User enters Username and Password
3850 WLC checks it’s local database finds the user
SSID approves the user to join
Is this possible or do you always have to point your 3850 to an external RADUIS like ISE?
Cheers
Eddy
I do not think 3850 itself could act as RADIUS server.
HTH
Rasika
Hi Nayarasi
Thank you for your reply and thanks for a great blog! really enjoy reading it!
Pingback: WLC Enable on Cisco 3850 | hiteshlodhi
Hi Nayarasi,
Will switch 3850 wireless controller supports multiple SSID (e.g.Guest, and Office)? It doesn’t seem like I can change the switch port mode access to trunk mode. As the switch give me an error ” Command rejected: Conflict with Capwap”.
Thank you.
Yes, it will support multiple SSID. Since this design only support Local mode APs, only you require is “Access Mode” switch configuration.
Since AP establish CAPWAP back to switch, you do not want to terminate wireless traffic at the AP (which require dot1q to support multiple SSID)
HTH
Rasika
we have three 3850 that are doing the wireless controller feature built in to the code.two of those 3850 ‘s are working so good , but one of those 3850’s is having issue with the client connecting to wireless.if i am rebooting that switch client will start connecting again,then suddenly they will stop connecting until he reboots again.so,what could be the reason for this .send me some alternate helpful solution .
What is the IOS-XE version you run on your 3850 ?
Hope all are running with identical image version ?
Rasika
Thank you, its working now .
Glad to hear it.
Anyone know if you can run the access points on an extended switch off of the c3850
I do not think so.
Hi Gary,
I tried this a 3850 switch going into an extended switch it will work you just have to carry the VLAN across between the switches. I would not recommend this but if your in a tight squeeze the AP doesn’t have to terminate on the 3850 switch to work.
one unrelated note. you can use just ‘sh arc c d’ as by default it will give you running vs startup diff so no need to specify it. this also works on devices that do not have the archive feature configured. i always use this before and after making config changes as it gives you a nice summary of what you configured