In this post we will see how to configure QoS for wired & wireless ports based on its role.I have taken two example of VoIP phone connected switchprot (wired port) & AP connected switchport (wireless port).
Here is our CA topology & I will focus on 3850-2 switch for this QoS configuration. IOS-XE 3.3.1 is used for this post & behavior may be different if you are using an earlier version of software code.
 I have configured two switch-ports (G1/0/11 & 12) in 3850-2 switch for VoIP phones as shown below
I have configured two switch-ports (G1/0/11 & 12) in 3850-2 switch for VoIP phones as shown below
interface GigabitEthernet1/0/11 description VOIP-1 switchport access vlan 13 switchport mode access switchport voice vlan 989 spanning-tree portfast ! interface GigabitEthernet1/0/12 description VOIP-2 switchport access vlan 13 switchport mode access switchport voice vlan 989 spanning-tree portfast
Now let’s see make a call between these two phones & see how QoS parameters change. I have configured below SAPN session & my monitoring PC (BackTrack) connected to G1/0/47 of this switch.
3850-2#sh run | in session monitor session 1 source interface Gi1/0/11 monitor session 1 destination interface Gi1/0/47 encapsulation replicate ! 3850-2#sh run int g1/0/47 interface GigabitEthernet1/0/47 end
Here is the packet captures of signaling & RTP media packets coming from VoIP-1 phone connected to G1/0/11. Similarly Packets coming from VoIP-2 should have these classification when it comes to G1/0/12.

 Now If we are look at packet going to VoIP-1 (only RTP traffic since signalling go back to CUCM). As you can see traffic going to VoIP-1 has EF (or Priority 5 in dot1q header) which is same as incoming values from VoIP-2. This is very important thing to remember in this 3850 platform, which is by default QoS values (DSCP or CoS) received by a wired switchport will be trusted & pass-through to another wired switchport without a change.
Now If we are look at packet going to VoIP-1 (only RTP traffic since signalling go back to CUCM). As you can see traffic going to VoIP-1 has EF (or Priority 5 in dot1q header) which is same as incoming values from VoIP-2. This is very important thing to remember in this 3850 platform, which is by default QoS values (DSCP or CoS) received by a wired switchport will be trusted & pass-through to another wired switchport without a change.
 Now let’s see how this work when make a call between wireless phone to wired phone. To do this we will create a open authentication wlan called “3850” & map it to vlan 1410 under the AP group where L3602-1 configured for. (I used no broadcast-ssid since I am doing this in office environment & do not want to visible to normal users). Also I will uesd iPhone5 to illustrate QoS mapping changes as well.
Now let’s see how this work when make a call between wireless phone to wired phone. To do this we will create a open authentication wlan called “3850” & map it to vlan 1410 under the AP group where L3602-1 configured for. (I used no broadcast-ssid since I am doing this in office environment & do not want to visible to normal users). Also I will uesd iPhone5 to illustrate QoS mapping changes as well.
3850-2(config)#wlan 3850 17 3850 3850-2(config-wlan)# no broadcast-ssid 3850-2(config-wlan)# client vlan WLN-STD-6 3850-2(config-wlan)# radio dot11a 3850-2(config-wlan)# no security wpa 3850-2(config-wlan)# no shutdown 3850-2#show ap groups Site Name: default-group Site Description: WLAN ID WLAN Name Interface ---------------------------------------------------- AP Name Ethernet MAC Location ----------------------------------------------------------- Site Name: SPG1-PW00 Site Description: WLAN ID WLAN Name Interface ----------------------------------------------------- 21 LTUWireless WLN-STD-6 AP Name Ethernet MAC Location ----------------------------------------------------------- L3702-1 7cad.74ff.2bc6 default location L3602-1 4c00.82df.a4c1 default location 3850-2(config)#ap group SPG1-PW00 3850-2(config-apgroup)#wlan 3850 3850-2(config-wlan-apgroup)#vlan 1410
You can verify wireless client connectivity details as below. iPhone5 detail highlighted in purple color.
3850-2#show wireless client summary Number of Local Clients : 1 MAC Address AP Name WLAN State Protocol -------------------------------------------------------------------------------- 04f7.e4ea.5b66 L3602-1 17 UP 11n(5) 2c54.2dea.f4ea L3602-1 17 UP 11a 3850-2#show wireless client mac-address 04f7.e4ea.5b66 detail Client MAC Address : 04f7.e4ea.5b66 Client Username: N/A AP MAC Address : f84f.57e3.1460 AP Name: L3602-1 AP slot : 1 Client State : Associated Wireless LAN Id : 17 Wireless LAN Name: 3850 BSSID : f84f.57e3.146e Connected For : 2851 secs Protocol : 802.11n - 5 GHz Channel : 36 Client IIF-ID : 0xf2a50000000025 ASIC : 0 IPv4 Address : 10.141.96.9 IPv6 Address : Unknown Association Id : 2 Authentication Algorithm : Open System Status Code : 0 Session Timeout : 0 Client CCX version : No CCX support Input Policy Name : unknown Input Policy State : None Output Policy Name : unknown Output Policy State : None 802.1P Priority Tag : Not supported WMM Support : Enabled U-APSD Support : Disabled Power Save : ON Current Rate : m7
If you do a wireless packet capture you would see the wireless frames coming from this iPhone5. I am using Jabber Voice (v9.1.6.21640) as the voice client. Here is a RTP packet coming from iPhone5. As you can see WMM-UP value is 5 even though actual IP packet DSCP is EF.In fact this should mark as priority 6 as per 802.11e standard, but most of these devices not correctly mark UP value.(if it is 7925G it is marked UP as 6 🙂 ). In CA, when AP mapping DSCP values to outer CAPWAP, it will NOT based on the UP value, but simply copy the original packet DSCP (you can change this using UP to DSCP mapping table)
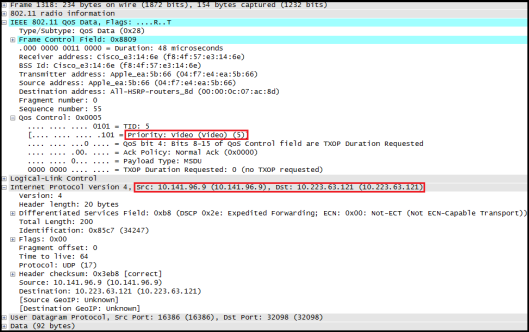 Now let’s take a look at the packet capture at G1/0/2 wireless port while we are making a call between iPhone5 to VoIP-2.
Now let’s take a look at the packet capture at G1/0/2 wireless port while we are making a call between iPhone5 to VoIP-2.
interface GigabitEthernet1/0/2 description L3602-1 switchport access vlan 1610 switchport mode access spanning-tree portfast ! interface GigabitEthernet1/0/47 end ! monitor session 1 source interface Gi1/0/2 monitor session 1 destination interface Gi1/0/47
Here is the capture output (at G1/0/2) of a signalling packet & RTP media traffic coming from iPhone5 to 7965 wired phone. As you can see the outer CAPWAP DSCP value is EF & CS3 respectively, This is simply copy from the original packet DSCP onto outer CAPWAP header. Also note that UP value are 5 & 0 respectively, but that is not in use when derive the outer CAPWAP (This is a major difference in CA compare to CUWN where it will derive based on WMM-UP value)
Also note that I have removed default “untrust” behavior of this switch platform when traffic traverses wireless to wired or vice versa. If you do not do this outer CAPWAP DSCP will be re-written to BE (0x00) at this point.
3850-2(config)#no qos wireless-default-untrust
 Now if you look at G1/0/12 packet capture you will see what QoS values goes when it received by VoIP phone. As you can see WCM/Switch has re-written the 802.1q header CoS value & original packet DSCP based on the UP values (This is something I did not expect, but capture prove it is)
Now if you look at G1/0/12 packet capture you will see what QoS values goes when it received by VoIP phone. As you can see WCM/Switch has re-written the 802.1q header CoS value & original packet DSCP based on the UP values (This is something I did not expect, but capture prove it is)
Below capture shows VoIP phone getting the packet with DSCP AF41 (instead of EF) & 802.1q CoS value of 4.
 Here is the signaling packet going out of trunk port (G1/0/48), since UP value came with 0, WCM rewritten the 802.1p to 0, then switch port rewrite original packet DSCP to 0 based on that.
Here is the signaling packet going out of trunk port (G1/0/48), since UP value came with 0, WCM rewritten the 802.1p to 0, then switch port rewrite original packet DSCP to 0 based on that.
 So it is important to classify your traffic Based on a corporate QoS policy, rather trusting DSCP (or WMM-UP value for wireless frames), since there is no consistency of these different clients.
So it is important to classify your traffic Based on a corporate QoS policy, rather trusting DSCP (or WMM-UP value for wireless frames), since there is no consistency of these different clients.
In a future post we will see how to classify traffic in order to get same treatment for wired & wireless traffic across the network.
Related Posts
1. 3850 QoS – Part 1 (QoS Touch Points)
2. 3850 QoS – Part 2 (Queuing Models)
3. 3850 QoS – Part 4 (Wireless QoS Mapping)
4. 3850 QoS – Part 5 (Traffic Classification)


Pingback: 3850 QoS – Part 3 (Port Specific QoS Role) | ytd2525
Hi, Great article. I tried to disable the default behavior of the switch, see below. But its not accepting the command.
Switch(config)#no qos wireless-default-untrust
‘qos wireless-default-untrust’ command cannot be disabled
Which version of IOS-XE you are running ? I am using 3.3.1. Try that & see, it should work
HTH
Rasika
Pingback: Cisco iOS | KB