Tags
Here is the 5th & final post of our WPA3 series. We will cover WPA3-Enterprise in this post which is going to be the replacement for WPA2-Enterprise. WiFi Alliance lists WPA3-Enterprise mode requirements in WPA3 Specification 2.0 (Dec 2019) document. There are 3 modes of operation in WPA3-Enterprise
- WPA3-Enterprise only mode
– When a BSS is configured in WPA3-Enterprise only mode, PMF shall be set to required (MFPR bit in the RSN Capabilities field shall be set to 1 in the RSNE transmitted by the AP)
– A WPA3-Enterprise STA shall negotiate PMF when associating to an AP using WPA3-Enterprise only mode - WPA3-Enterprise transition mode
– When WPA2-Enterprise and WPA3-Enterprise transition Mode are configured on the same BSS (mixed mode), PMF shall be set to capable (MFPC bit shall be set to 1, and MFPR bit is by default set to 0 in the RSN Capabilities field in the RSNE transmitted by the AP)
– A WPA3-Enterprise STA shall negotiate PMF when associating to an AP using WPA3-Enterprise transition mode - WPA3-Enterprise 192-bit mode
– When WPA3-Enterprise 192-bit Mode is used by an AP, PMF shall be set to required (MFPR bit in the RSN Capabilities field shall be set to 1 in the RSNE transmitted by the AP).
– When WPA3-Enterprise 192-bit Mode is used by a STA, PMF shall be set to required (MFPR bit in the RSN Capabilities field shall be set to 1 in the RSNE transmitted by the STA).
– Permitted EAP cipher suites for use with WPA3-Enterprise 192-bit Mode are:
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
ECDHE and ECDSA using the 384-bit prime modulus curve P-384
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
ECDHE using the 384-bit prime modulus curve P-384
RSA ≥ 3072-bit modulus
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
RSA ≥ 3072-bit modulus
DHE ≥ 3072-bit modulus
When you configure FT (Fast BSS Transition or 802.11r) in WPA3-Enterprise only or WPA3-Enterprise transition mode ( 1 & 2 modes listed previously), STA shall select the AKM on a BSS in priority order given below
1. FT Authentication using IEEE Std 802.1X (SHA 256) 00-0F-AC:3
2. Authentication using IEEE Std 802.1X (SHA256) 00-0F-AC:5
3. Authentication using IEEE Std 802.1X 00-0F-AC:1
Below shows the different AKM values defined in IEEE-802.11 REVmd ( Revision of 802.11-2016 standard which is going to be 802.11-2020). Note that AKM 8 & 9 used with SAE (WPA3- Personal use AKM 8), AKM 1,3,5,11 (WPA3-Enterprise only or WPA3-Enterprise transition), AKM 12,13 (WPA3-Enterprise 192-bit) & AKM 18 for Enhanced Open (OWE).
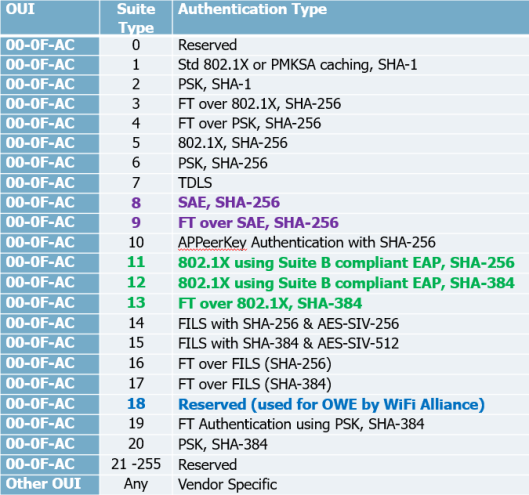
You notice some AKM refer “Suite B” a set of cryptographic algorithms (to provide 128 bit and 192 bit security strength) defined by NSA (National Secuirty Agency) in 2005. NSA replaced Suite B with CNSA (Commercial National Security Algorithm Suite – to provide min 192 bit security) in 2018. WPA3-Enterprise 192-bit mode is using AES-256-GCMP encryption and use CNSA approved cipher suites listed below.
AES-256-GCMP : Authenticated Encryption
HMAC-SHA-384 for key derivation & key confirmation
ECDH and ECDSA using 384-bit elliptic curve for key establishment & authentication
In deploying WPA-Enterprise only mode, you can simply enable PMF (Protected Management Frame) in your WPA2-Enterprise SSID, that would be technically WPA3-Enterprise only mode.
If you want to enable WPA3-Enterprise Transition mode, then you can set PMF optional in your SSID configuration, so PMF capable client negotiate it and other clients join SSID without PMF. This is the practical way of enabling WPA3-Enterprise in today’s network unless you want to create a seperate SSID for WPA3-Enterprise.
If you want highest secuirty, then you can go with WPA3-Enterprise 192-bit mode. In that case, you have to use AES-256-GCMP as encryption and either AKM 12 (802.1X, SHA-384) or 13 (FT over 802.1X, SHA-384) in order to provide 192 bit security overall.
In this post we will explore WPA3-Enterprise 192-bit configurations. I have used Cisco IOS-XE based controller (9800-CL running with IOS-XE 17.3.1) & Cisco ISE (v2.7) as RADIUS server. Here is the basic topology for this post (Note that AP is connected to a physical switch and CAPWAP back to WLC, for simplicity not shown those physical switches).
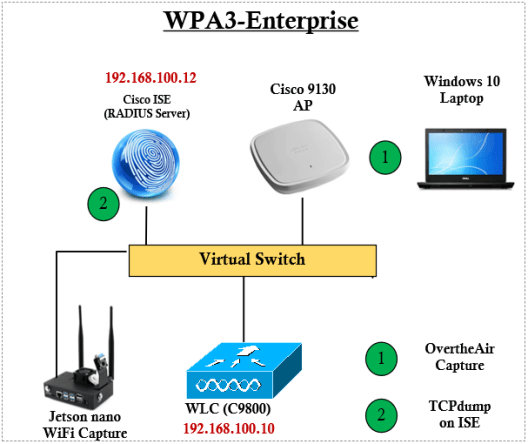
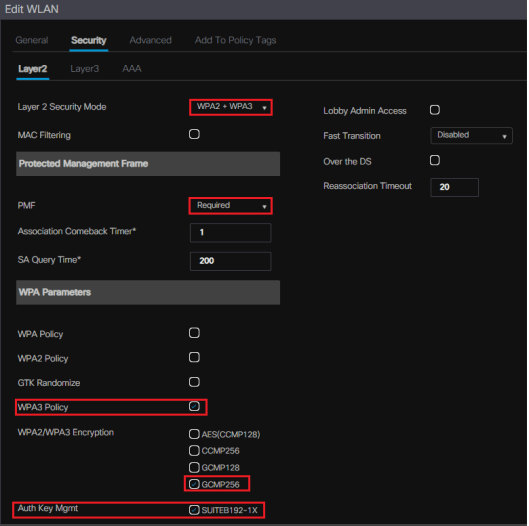
If you want to use WPA3-Enterprise 192 bit mode, you have to choose GCMP256 as encryption method and AKM as “SuiteB192-1X” as shown below.
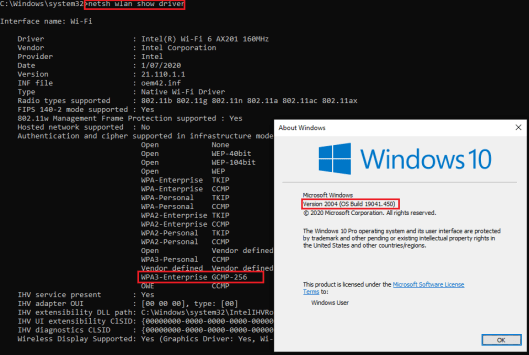
I have used Windows 10 client with May 2020 update (v2004), You require to upgrade to that in order to support WPA3-Enterprise mode & Enhanced Open (OWE). You can verify supported security methods of your WiFi driver by using “netsh wlan show driver” command on Windows CLI.
You have to create a manual profile in order to configure your client to use WPA3-Enterprise security method. You will notice, you cannot change the Encryption type to GCMP-256 even you select “WPA3-Enterprise” as security type.
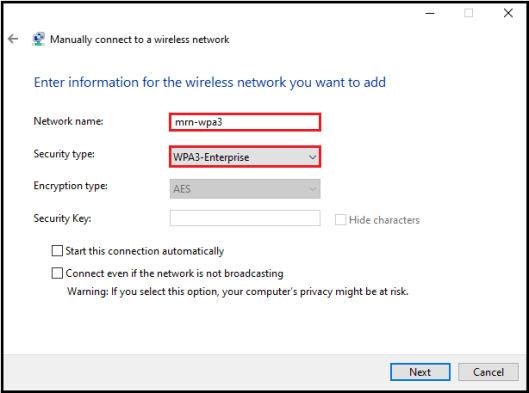
You have to select “WPA2-Enterprise” & leave Encryption type to “AES” in this step and proceed.
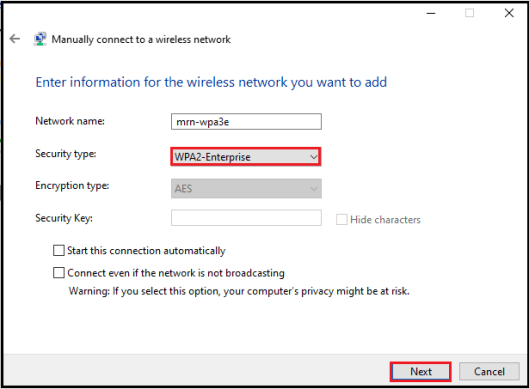
Once you click “Next” you should able to change the connection settings of this profile.
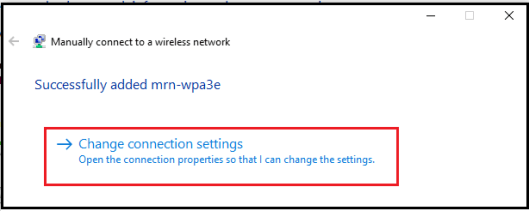
In the “Security” setting, you can change the security type to “WPA3-Enterprise” and it will automatically select Encryption type as “GCMP-256“. In my case, I have selected the authentication method “Smart Card or other Certificate” in order to use EAP-TLS (Tried to use PEAP and it gave me an error msg saying it is not supported).
You have to select a Trusted root certificate authority applicable to your client certificate by click on the “Setting” button. Also, you can modify certain parameters under the “Advanced Setting” section prior to close that network profile configuration.
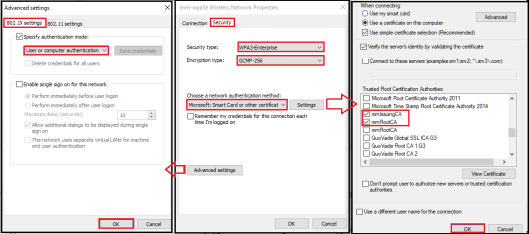
Then you can connect to your client to configured SSID. You have to choose appropriate certificate for that. I have used Microsoft CA in my lab setup and already installed a user certificate (issued to dmg@mrn.local) on my windows laptop. I used Cisco ISE (v 2.7.x) as RADIUS server and configured for basic 802.1X authentication (No special configs required on RADIUS server). You can verify your client profile configuration using “netsh show wlan profiles” command
C:\Windows\system32>netsh wlan show profiles name="mrn-wpa3e" Profile mrn-wpa3e on interface Wi-Fi: ======================================================================= Applied: All User Profile Profile information ------------------- Version : 1 Type : Wireless LAN Name : mrn-wpa3e Control options : Connection mode : Connect manually Network broadcast : Connect only if this network is broadcasting AutoSwitch : Do not switch to other networks MAC Randomization : Disabled Connectivity settings --------------------- Number of SSIDs : 1 SSID name : "mrn-wpa3e" Network type : Infrastructure Radio type : [ Any Radio Type ] Vendor extension : Not present Security settings ----------------- Authentication : WPA3-Enterprise Cipher : GCMP-256 Security key : Absent 802.1X : Enabled EAP type : Microsoft: Smart Card or other certificate 802.1X auth credential : Machine or user credential Cache user information : No Cost settings ------------- Cost : Unrestricted Congested : No Approaching Data Limit : No Over Data Limit : No Roaming : No Cost Source : Default
Then you can connect your client to WPA3-Enterprise SSID and you can check client connectivity properties

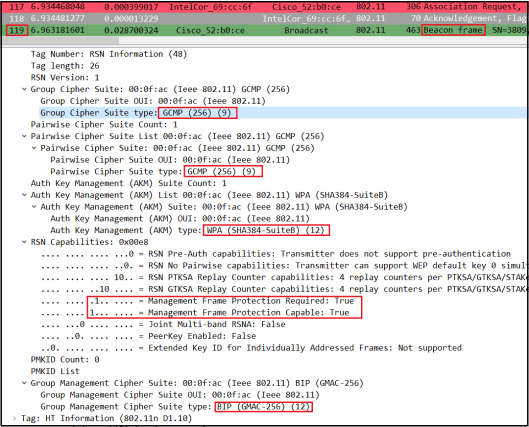
Here is the over the air packet capture. You cand download entire packet capture (mrn-wpa3e-192-overtheair.pcapng). If you look at a Beacon frame, you will see AP advertise its security capability under RSNE. Note that both Group Cipher & Pairwise Cipher is AES-256-GCMP (Suite Type value 9) for data encryption. AKM value is SHA-384 which provides 192-bit security. For Management Frame Protection (MFP), it uses BIP-GMAC-256 (Type value 12)
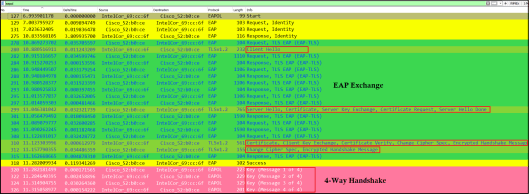
You can filter EAP Exchange & 4 Way Handshake messages using “eapol” display filter in wireshark. You will see standard TLS 1.2 negotiation followed by 4-Way Handshake to derive unicast & broadcast encryption keys (PTK/GTK)
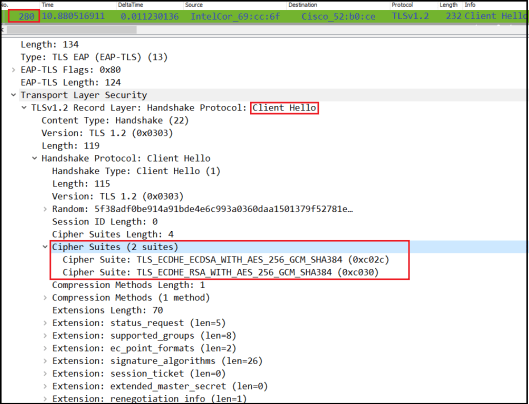
If you look at “Client Hello” details (frame #280), you will see client listed two TLS cipher suites that supports AES_256_GCMP as the encryption method, SHA-384 for message integrity.
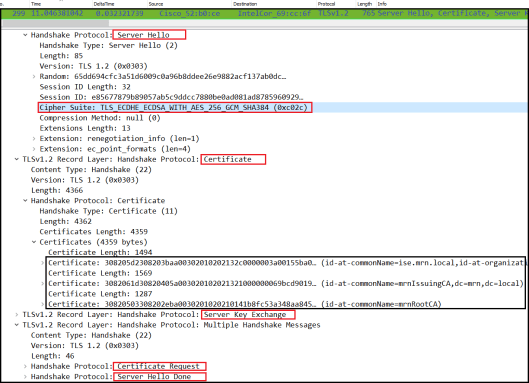
here the Server Hello frame (#299) that Authentication Server selected “ECDHE_ECDSA_WITH_AES_256_GCMP_SHA384” as TLS cipher suite.
Here is the Client Certificate detail in frame#310
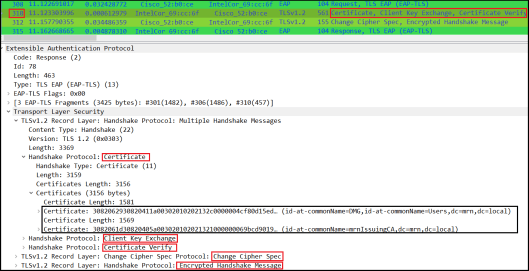
In Cisco presentations, it says that Authenticator use RADIUS AVP 188 (WLAN-AKM-Suite) to inform Auth server that SSID configured with 192-bit security. However, I could not see such AVP value in my testing where 9800 WLC inform Cisco ISE that AVP in those RADIUS request messages.
Here is the packet capture (ise-wpa3e-tcpdump.pcap) taken from ISE end (Operations -> Troubleshoot -> General tools -> TCP Dump). I wouod expect to see it in initial Access Request message (frame#1) send by WLC (100.10) to ISE (100.12)
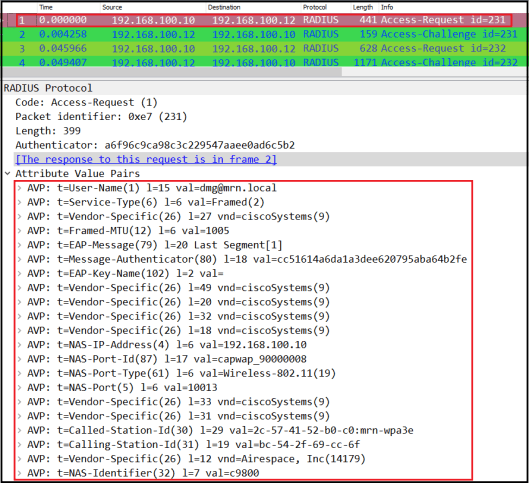
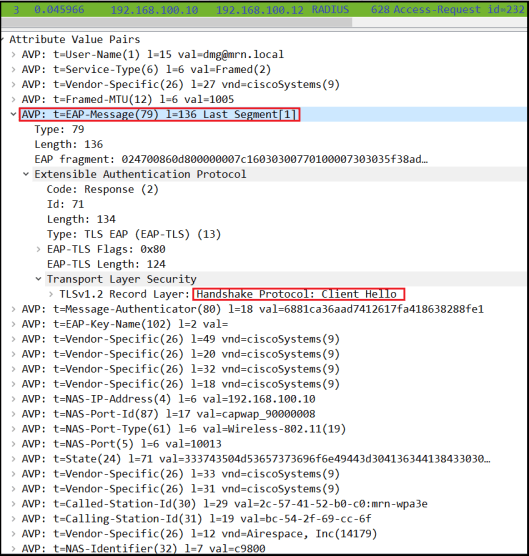
If you look at frame#3 in that capture, it is the “Client Hello” message encapsulate into RADIUS by WLC and forward it to ISE.
You can delete wireless SSID profile by simply forget SSID or using “netsh wlan delete profile” command as shown below
C:\Windows\system32>netsh wlan delete profile name="mrn-wpa3e" i=*
Profile "mrn-wpa3e" is deleted from interface "Wi-Fi".
You can find which product support WPA3-Enterprise using WiFi Alliance webpage product finder. Example below show how to filter WPA3-Enterprise supported computer & Accessories. (Noticed Intel AX210 – certified recently for WiFi6E – 6GHz band)
Be familiar with this latest security enhancements and test it in your environment. When we go to 6GHz, you will see only WPA3 and Enchance Open going to be supported (No transition modes, No WPA2 and no WPA). Here is a WPA3 micro course I developed for WiFiTraining if you are interested to learn all these new security bit more in detail.
RELATED POSTS
1. Enhanced Open
2. Enhanced Open Transition Mode
3. WPA3 Personal
4. WPA3 Personal Transition Mode
5. WPA3 Lessons
References
1. Wireless Security Enhancement by Stephen Orr – Mobility Field Day 5 (July 2020)
2. WPA3,OWE & DPP by Hemant Chaskar – WLPC Phoenix 2019 (Feb)
3. Advancements in Wireless Secuirty – BRKEWN 2006 by Stephen Orr – CiscoLive 2020 Barcelona (Jan)
4. WPA3 Deployment Guide – Cisco

What are the config changes required in the freeradius setup to be able to handle WPA3-Enterprise SSIDs?
Hi Arpan,
On RADIUS server no special configs required.
HTH
Rasika
Be aware that you can’t have WPA2/WPA3 mixed mode SSID and expect all clients that support WPA2 only to connect… We just ran into an issue with basically all Apple iPhones and iPads unable to connect to PSK wifi in WPA2/3 mixed.
Good to know.. hope Apple can fix it in later software..
Hi Rasika,
Your WPA3-Enterprise 192 bit mode settings select ‘WPA2+ WPA3’ at Layer 2 Security Mode and ‘GCMP256’ at Encryption. Can a Client with WPA2-Entprise + Encryption AES-CCMP connect to it successfully?
Hi Aris, Yes you can advertise multiple AKM (Authenticated Key Management) methods in same SSID. It is called mixed mode deployment. Note that some security compromises occur as broadcast/multicast traffic has to encrypt using lowest common standard that support all clients in the cell.
HTH
Rasika
I created a CA using openssl on ubuntu and put the CA on Windows10.
However, there is no response from the radius server. Please tell me how to create a certificate.
In my cased I used Windows Server as CA.
I created a certificate using openssl on ubuntu. And I put the certificate in windows 10.
But on ubuntu’s Radius server there is no response.
Did you create the CA certificate incorrectly? Please tell me how to create a CA certificate.
Hello, with WPA3-Enterprise 192bit is there any support for FT (802.11r)? I see in hostapd that this is somewhat supported however cannot see any from vendors etc Cisco WLAN platform.
I am assuming that the only difference is the FT keys being expanded from 256bit to 384bit but unsure.
AKM12 & AKM13 for 192 bit support. AKM13 is with FT support. I have to do some testing with AK
HTH
Rasika
Any Updates towards this? Also Could you say WPA3-Enterprise-only mode is equivalent to/same as WPA2-Enterprise with PMF? If not, Please could you say the difference.
WPA3-Enterprise mode is equivalent to WPA2-E with PMF. From WiFi Alliance certification point of view, they specifically verify if it support AKM value 5 (802.1X with SHA-256) with PMF.
HTH
Rasika
Hi, can you share xml format for wpa3 enterprise. So query is before connecting profile using netsh rootca & user ca should be trusted on the client.
I am trying connect my laptop using the same architecture and hardware but I am getting message “Can’t connect the network” and logs on WLC logs give message “80 2.11 association error
Hi Nishant,
I would capture over the Air & check exactly what’s going on.
Rasika
Hi
what to configure if we need 00:0F:AC(1) in our AKM ?
For Eg: wpa2+ccmp in encryption gives WPA (SHA256) (5) in AKM.
Under AKM, just configure 802.1X-SHA1 which will give AKM of 1.
802.1X-SHA256 will be the AKM value 5
HTH
Rasika
Rasika,
Did you have any success connecting iphones/ipads (latest HW and IOS) on WPA3 – Enterprise Or even WPA2-Enterprise with 11w? It seems there is some general compatibility with ssid that have .1x and 11w. It will be great if you can share your results.
Hi
Thank you for the reply.
I am trying to configure WPA3-enterprise transition but am unable to fulfill wifi alliance(WFA)’s criteria for it.
Kindly refer to below mentioned criteria according to WFA for certification:
WPA3-Enterprise transition mode
1)An AP shall enable at least AKM suite selectors 00-0F-AC:1 (IEEE 802.1X with SHA-1) and 00-0F-AC:5
(IEEE 802.1X with SHA-256) in the BSS
2)A STA shall allow at least AKM suite selectors 00-0F-AC:1 and 00-0F-AC:5 to be selected for an association
3)An AP shall set MFPC to 1, MFPR to 0
4)A STA shall set MFPC to 1, MFPR to 0
One question about Wi-Fi6E + 802.1x:
If Wi-Fi6E need 802.1x, how the cryptographic algorithms should be set in AP? Only Suite B?
Hi Roger,
AKM value 5 or 12 is for WPA3-Enterprise. If you need 192 bit security (Suite-B) then only you select that option, but 95% of the time we do not use 192-bit mode security in typical corporates
HTH
Rasika
I have a 3504 controller with 8.10.185 with 9120 and 9115 APs
When I try to configure
Layer2 Security as WPA2+WPA3
Security Type Enterprise
Policy WPA3
Encryption Cipher GCMP256
FT Disable
PMF Required
SuiteB192-1X is checked
Then the WLAN is not getting beaconing
If I change Encryption Cipher to CCMP AES then it beacons but then SuiteB192 is not present
What am I missing here? Is it a Cisco Issue or a config issue?
Please help
which mean it does not support GCMP-AES-256, might be something to do with AireOS code.
Pingback: CTS 320: WPA3-Enterprise Part 2
Pingback: They’re giving me the 9800!! – Let's Ginger-Fi it!