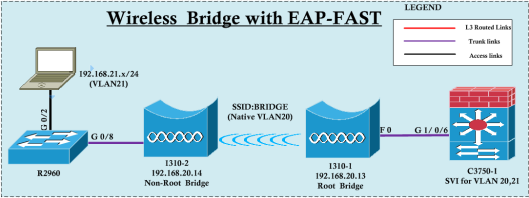
In this post we will see how to configure a wireless bridge (Root & Non-Root Bridge) with EAP-FAST security. Here is the basic topology for the post & I have used two 1310 AP with 12.4(25d)JA software version.
Here is the G1/0/6 Config of C3750-1 switch. Since wireless bridge has to carry multiple vlan traffic (in my case 20-21) it has to configure as a trunk port.
hostname C3750-1 ! ip dhcp excluded-address 192.168.21.1 192.168.21.50 ip dhcp excluded-address 192.168.21.254 ip dhcp pool VLAN21 network 192.168.21.0 255.255.255.0 default-router 192.168.21.254 ! interface Vlan20 ip address 192.168.20.254 255.255.255.0 interface Vlan21 ip address 192.168.21.254 255.255.255.0 ! interface GigabitEthernet1/0/6 description 1310-1 (ROOT BRIDGE) switchport trunk encapsulation dot1q switchport trunk native vlan 20 switchport trunk allowed vlan 20,21 switchport mode trunk
Here is the Root Bridge configuration without any security configurations. Later on we will configure the EAP-FAST for this. Note that for native vlan (20) to be configured with bridge group 1. Also SSID configured as “infrastructure-ssid” to ensure only infrastructure device could associate to it (no normal clients)
hostname 1310-1 ! dot11 ssid BRIDGE vlan 20 authentication open infrastructure-ssid ! interface Dot11Radio0 ssid BRIDGE station-role root bridge ! interface Dot11Radio0.20 encapsulation dot1Q 20 native bridge-group 1 interface Dot11Radio0.21 encapsulation dot1Q 21 bridge-group 21 ! interface FastEthernet0.20 encapsulation dot1Q 20 native bridge-group 1 interface FastEthernet0.21 encapsulation dot1Q 21 bridge-group 21 ! interface BVI1 ip address 192.168.20.13 255.255.255.0 ip default-gateway 192.168.20.254
Here is the Non-Root Bridge Configuration
hostname 1310-2 ! dot11 ssid BRIDGE vlan 20 authentication open infrastructure-ssid ! interface Dot11Radio0 ssid BRIDGE station-role non-root bridge ! interface Dot11Radio0.20 encapsulation dot1Q 20 native bridge-group 1 interface Dot11Radio0.21 encapsulation dot1Q 21 bridge-group 21 ! interface FastEthernet0.20 encapsulation dot1Q 20 native bridge-group 1 interface FastEthernet0.21 encapsulation dot1Q 21 bridge-group 21 ! interface BVI1 ip address 192.168.20.14 255.255.255.0 ip default-gateway 192.168.20.254
With this configuration, you should see your non-root bridge associating to your root bridge.
1310-2#Nov 8 20:39:46.316: %DOT11-4-UPLINK_ESTABLISHED: Interface Dot11Radio0, Associated To AP 1310-1 001b.2a30.48b0 [None] 1310-1#sh dot11 ass 802.11 Client Stations on Dot11Radio0: SSID [BRIDGE] : MAC Address IP address Device Name Parent State 001b.2a30.48c0 192.168.20.14 bridge 1310-2 self Assoc 1310-1#sh dot11 ass 001b.2a30.48c0 Address : 001b.2a30.48c0 Name : 1310-2 IP Address : 192.168.20.14 Interface : Dot11Radio 0 Device : bridge Software Version : 12.4 CCX Version : 5 Client MFP : Off State : Assoc Parent : self SSID : BRIDGE VLAN : 20 Hops to Infra : 1 Association Id : 1 Clients Associated: 1 Repeaters associated: 0 Tunnel Address : 0.0.0.0 Key Mgmt type : NONE Encryption : Off Current Rate : 54.0 Capability : WMM ShortHdr ShortSlot Supported Rates : 1.0 2.0 5.5 11.0 6.0 9.0 12.0 18.0 24.0 36.0 48.0 54.0 Voice Rates : disabled Bandwidth : 20 MHz Signal Strength : -75 dBm Connected for : 80 seconds Signal to Noise : 24 dB Activity Timeout : 30 seconds Power-save : Off Last Activity : 1 seconds ago Apsd DE AC(s) : NONE Packets Input : 3341 Packets Output : 10247 Bytes Input : 378995 Bytes Output : 1405473 Duplicates Rcvd : 0 Data Retries : 521 Decrypt Failed : 0 RTS Retries : 12 MIC Failed : 0 MIC Missing : 0 Packets Redirected: 0 Redirect Filtered: 0
Here is the R2960 switch configuration. I have given switch management IP from vlan 20.
hostname R2960 ! interface GigabitEthernet0/2 switchport access vlan 21 switchport mode access spanning-tree portfast ! interface GigabitEthernet0/8 switchport trunk native vlan 20 switchport trunk allowed vlan 20,21 switchport mode trunk ! interface Vlan20 ip address 192.168.20.15 255.255.255.0 ! ip default-gateway 192.168.20.254
If you define a DHCP (or you can statically assign a IP for Laptop) for vlan 21, you should see Laptop will get an IP from 192.168.21.0/24 network. In my case Laptop got 192.168.21.51 IP address & I can ping it from my C3750-1 switch.
C3750-1#ping 192.168.21.51
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.21.51, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/9 ms
As long as this works you can move on to adding security for this configuration. First we will configure 1310-1(root bridge) as RADIUS server. If you using AP as radius server, you can configure either LEAP, EAP-FAST or MAC authentication methods. In this example we will disable LEAP & MAC authentications. For highest security we have used WPA2/AES.
aaa new-model aaa group server radius RAD-GROUP server 192.168.20.13 auth-port 1812 acct-port 1813 aaa authentication login EAP-METHODS group RAD-GROUP radius-server local no authentication leap no authentication mac nas 192.168.20.13 key 0 MRN-CCIEW user nonroot password nonrootpw radius-server host 192.168.20.13 auth-port 1812 acct-port 1813 key 0 MRN-CCIEW dot11 ssid BRIDGE authentication open eap EAP-METHODS authentication network-eap EAP-METHODS authentication key-management wpa version 2 interface Dot11Radio0 encryption vlan 20 mode ciphers aes-ccm
Then we can configure the Non-Root Bridge with EAP-FAST credential which we defined on the Root Bridge.
1310-2(config)#eap profile FAST 1310-2(config-eap-profile)#method ? fast EAP-FAST method allowed gtc EAP-GTC method allowed leap EAP-LEAP method allowed md5 EAP-MD5 method allowed mschapv2 EAP-MSCHAPV2 method allowed tls EAP-TLS method allowed 1310-2(config-eap-profile)#method fast 1310-2(config)#dot1x credentials FAST 1310-2(config-dot1x-creden)#username nonroot 1310-2(config-dot1x-creden)#password nonrootpw ! 1310-2(config)#dot11 ssid BRIDGE 1310-2(config-ssid)#authentication open eap EAP-METHODS 1310-2(config-ssid)#authentication network-eap EAP-METHODS 1310-2(config-ssid)#authentication key-management wpa version 2 1310-2(config-ssid)#dot1x eap profile FAST 1310-2(config-ssid)#dot1x credentials FAST ! 1310-2(config-ssid)#interface Dot11Radio0 1310-2(config-if)# encryption vlan 20 mode ciphers aes-ccm
Once you do this you should see your Non-Root Bridge associated with Root Bridge using EAP-FAST.
1310-2(config-if)# Nov 8 21:16:51.796: %LINK-3-UPDOWN: Interface Dot11Radio0, changed state to up Nov 8 21:16:52.063: %DOT11-4-UPLINK_ESTABLISHED: Interface Dot11Radio0, Associated To AP 1310-1 001b.2a30.48b0 [EAP-FAST WPAv2] 1310-1# Nov 8 21:11:42.430: %DOT11-6-ASSOC: Interface Dot11Radio0, Station 1310-2 001b.2a30.48c0 Associated KEY_MGMT[WPAv2] 1310-1#sh dot11 associations 001b.2a30.48c0 Address : 001b.2a30.48c0 Name : 1310-2 IP Address : 192.168.20.14 Interface : Dot11Radio 0 Device : bridge Software Version : 12.4 CCX Version : 5 Client MFP : On State : EAP-Assoc Parent : self SSID : BRIDGE VLAN : 20 Hops to Infra : 1 Association Id : 1 Clients Associated: 1 Repeaters associated: 0 Tunnel Address : 0.0.0.0 Key Mgmt type : WPAv2 Encryption : AES-CCMP Current Rate : 54.0 Capability : WMM ShortHdr ShortSlot Supported Rates : 1.0 2.0 5.5 11.0 6.0 9.0 12.0 18.0 24.0 36.0 48.0 54.0 Voice Rates : disabled Bandwidth : 20 MHz Signal Strength : -75 dBm Connected for : 214 seconds Signal to Noise : 24 dB Activity Timeout : 30 seconds Power-save : Off Last Activity : 1 seconds ago Apsd DE AC(s) : NONE Packets Input : 41 Packets Output : 365 Bytes Input : 4556 Bytes Output : 42485 Duplicates Rcvd : 0 Data Retries : 2 Decrypt Failed : 0 RTS Retries : 0 MIC Failed : 0 MIC Missing : 0 Packets Redirected: 0 Redirect Filtered: 0 Session timeout : 0 seconds Reauthenticate in : never
So now you wireless bridge connection is more secure. Make sure you can ping the remote client
C3750-1#ping 192.168.21.51
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.21.51, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/9 ms
Hope this is useful for you.

Hello,
Nice work again! You are my mentor 🙂
Just wondering if vlan 20 is mandatory on the wired side of the two APs, because it only serves to the radio side.
I guess it could be necessary because of the bridge interface Do0.20/Fa0.20.
Yes, to bridge the wireless traffic to wired side you require vlan20 on Root AP wired side. Since I have used vlan20 as management IP for remote switch as well that side require vlan 20 too.
HTH
Rasika
Nice work (as the rest of your site).
Seeing your network diagram, I’m just wondering if the vlan 20 couldn’t be removed from the wired side.
I understand it could be mandatory because of the bridge-group Do0.20/Fa0.20.
But couldn’t we keep the vlans 20&21 on the wireless side (20 for the bridge / 21 for the data over the bridge), and keep only vlan 21 for the wired side?
For this, I would say this is just technical curiosity 🙂
For Root Bridge (Its BVI on vlan 20) to communicate back to wired side, wired side should know about vlan 20 & as a native vlan on that trunk. So wired side should have vlan 20 defined as native on that trunk.
For remote end, for similar reason it is required( I have used remote switch management on vlan 20)
Also without passing vlan20 traffic on that trunk link, SVI for vlan20 may not come up (unless you have another switch port configured for vlan 20)
HTH
Rasika
Is wireless mobility controller turned off on the 3750?
Are these being configured as lightweight or autonomous APs?
Hi Ian,
This is Autonomous AP configuration.
No WLC functionality in 3750.
HTH
Rasika
Rasika,
Got it working now. Turned off WLC on the 3850 switch. Used file: ap3g2-k9w7-tar.153-3.JAA.tar to convert 26021i ap to autonomous. Used the button method as the session with tftp was timing out when loading the file.
Thank you
Hi Ian,
Nice to hear that…
Rasika
Android supports -at least in my phone EAP-FAST- but it is not able to authenticate. So I am a bit lost here, do I need an external radius instead of the one included in the AP? if not, what would be the recommended commands to do some debug? Can you post a valid config for that? Is it possible to have PSK and LEAP in the same SSID? (I asked that for all those clients here without LEAP support)
Hi John,
For a given SSID you can configure either 802.1X (EAP methods ) or PSK, not both.
Regarding AP as local radius it should work. Note that in this config specific to wireless bridge (2 AP talk to each other on EAP-FAST).
This post should be most applicable in your scenario
“infrastructure ssid” ” “infrastructure client” command may need to remove if it is not working as given (since you associate normal clients).
HTH
Rasika
Hi john,
With EAP-FAST, be aware that your client must be provisioned with a PAC for the authentication to succeed.
Then you must manually import the PAC in your Android client, or check if it supports auto-provisioning.
HTH,
Andre.
Thanks Andre for checking these & responding…
Rasika
Hi
great blog post
1- can i do the same setup with point-to-multi point?
2- can i do the same with WLC ? which AP mode ? is there any limitation if i use WLC ?
1. Yes, you can. Keep in mind Root Bridge bandwidth is shared among Non-Root Bridges.
2. Yes, with WLC, APs has to be in MESH mode. I haven’t got any experience with MESH mode deployment to explain any limitations in detail.
HTH
Rasika
Hi Rasika. You have very useful info here ! Thanks for sharing your knowledge !
I’m trying to do similar setup, but with EAP-TLS and external Radius (Microsoft NPS).
I was able to make it work with PEAP and MS-CHAPv2. Basically the non-root bride AP is able to authenticate to NPS using PEAP on windows 2012 NPS server.
But my customer is requesting a higher security scenario, by using certificate authentication on non-root bridge AP, to NPS server that is configured as EAP-TLS, but it doesn’t work. I’ve installed CA cert and enrolled AP with cert from same CA(with both Server and Client authentication).
I’ve seen cisco example on how to configure WGB with WLC ans ACS. But can’t find a good example on how to make it work with two bridged AP and NPS and EAP-TLS. Maybe it’s not possible.
I would’nt mind to use local Radius on AP if EAP-TLS is supported, but I think it is not.
Any suggestion are welcome !
Best Regards,
Dominic
Very helpful demo. Thank you.
Just have one question about the native vlan or the management vlan.
If on both side I have separate networks, how could I prevent this native vlan from leaking to each other’s network? In your example, if vlan 20 is the management vlan, could we just another wlan for the radio?
Hi Eric,
You can’t put them into two different network. Management IP subnet/vlan of APs should be same on both end.
HTH
Rasika
Hi Rasika,
I followed this guide for one of my sites that needs to have an AP on a floor with no cabling wirelessly bridged to the nearest non-bridge AP connected to the backbone. Unfortunately as soon as I finished configuring the non-root bridge, it crashed my entire network at the site – could no longer ping any switches, AP’s or clients site wide and all services stopped working. I had to reboot the non-root bridge AP so that it reverted to it’s previous config for everything to normalize.
What did I do wrong? I can’t seem to find any information or anyone that has experienced this problem on the web.
Dean
Typo above — Meant to say as soon as I configured to ROOT bridge, it crashed everything. Not the non-root bridge. And the AP I had to reboot was the ROOT bridge, for everything to normalize.
Hi Dean,
I responded to your CSC thread, let’s keep it troubleshoot
Rasika
Dear Expert I have a wireless practice topic it say infrastructure SSID bridge link between AP1(which is acting as the root AP)and potential WGBs(only AP2 for now).
About this “potential WGBs(only AP2 for now)”. what is mean solution?
In AP1 root-bridge dot11 1 shoud add infrastructure-client command??
and AP2 Workgroup-bridge should add infrastructure-client command ?? or not ?? or only add AP1 is ok??
please help me thanks a lot.
You have to configure it on AP1, in order to transmit multicast/broadcast frames to WGB reliably. Have a look below post
This post also explain purpose of that command.
http://wirelessccie.blogspot.com/2010/09/workgroup-bridge-wgb-cli-commands.html
HTH
Rasika
can we do WGB in cisco mobility express supporting access point
if AP in Mobility Express mode, then you can use it as parent AP where your WGB come and connect.
You cannot run WGB & Mobility Express on the same AP
HTH
Rasika