Cisco enabled WGB feature on Wave2 APs (only for 2800/3800/1560 series) from AireOS 8.8.x release onward. Traditionally WGB feature supported only on Autonomous mode in IOS based APs. There are not autonomous images available for COS based APs (Click OS APs – 1800/2800/3800/4800).
In this post, we will configure 3802 as WGB with 802.1X (PEAP). Here is the topology for this post. 802.1X SSID configured with Central switching. WGB and wired client behind it get IP addresses via DHCP from the central site (192.168.99.x/24)

Here is the 3802 image version being used in this testing.
AP3802#show version
cisco AIR-AP3802I-Z-K9 ARMv7 Processor rev 1 (v7l) with 1028252/557172K bytes of memory.
Processor board ID FGL2201A3U2
AP Running Image : 8.10.122.0
Primary Boot Image : 8.10.122.0
Backup Boot Image : 8.10.121.0
.
Radio Driver version : 9.0.5.5-W8964
Radio FW version : 9.1.8.1
NSS FW version : 2.4.28
If you follow my previous post on WGB with PEAP on Autonomous AP, you see config steps are shown below
- Configure a Trust Point on AP
crypto pki trustpoint MRN_TRUST enrollment terminal subject-name CN=WGB revocation-check none rsakeypair WGB 2048
- Upload Root CA for configured Trust Point
WGB#crypto pki authenticate MRN_TRUST Enter the base 64 encoded CA certificate. End with a blank line or the word "quit" on a line by itself -----BEGIN CERTIFICATE----- . . -----END CERTIFICATE----- quit - Configure 802.X credential profile
dot1x credentials MRN-CRD username xxx password xxxx pki-trustpoint MRN_TRUST
- Configure EAP Profile
eap profile MRN-PRO method peap
- Configure SSID and map EAP/802.1X Profile
dot11 ssid mrn-wpa2e authentication open eap MRN_TRUST authentication key-management wpa version 2 dot1x credentials MRN-CRD dot1x eap profile MRN-PRO infrastructure-ssid
- Change Radio station-role to WGB and assign SSID
interface Dot11Radio1 encryption mode ciphers aes-ccm ssid mrn-wpa2e station-role workgroup-bridge
Before you configure WGB settings on 3802, you have to change AP mode to WGB. AP will be reloaded & then you can configure WGB specific configurations.
AP3802>enable AP3802#ap-type ? capwap Switch to CAPWAP AP type cloud Switch to cloud AP type mobility-express Switch to Mobility Express AP type workgroup-bridge Switch to Workgroup Bridge(WGB) AP type AP3802#ap-type workgroup-bridge WGB is a wireless client that serve as nonroot ap for wired clients. AP is the Master/CAPWAP AP, system will need a reboot when ap type is changed to WGB. Do you want to proceed? (y/N): y
Once converted to WGB, you can do configurations simply start command with the “configure” keyword. You can see different configuration options available shown below
AP3802#configure ? ap AP commands for IPv4/6 Configuration boot Set boot parameters clock Manage the system clock crypto Encryption module dot11Radio Dot11 radio interface dot1x IEEE 802.1X global configuration commands eap-profile EAP global configuration commands ntp Configure NTP security security information ssh Configures secure shell operation ssid-profile Configure SSID profile information wgb Workgroup-bridge configuration
It is important to configure accurate time, especially if you are using 802.1X. You can do it by using “configure clock” CLI command. It is a good idea to syn it with a NTP server
AP3802#configure clock set Set the time and date timezone Configure time zone AP3802#configure clock set 14:21:19 7 4 2020 Sat Jul 4 14:21:19 AEST 2020 AP3802#show clock *14:21:26 AEST Sat Jul 4 2020 AP3802#configure ntp server 192.168.100.1
You can configure Trust Point and associated parameters as shown below. In this case enrollment type is chosen as “terminal”. By using the “authenticate” option you can load the CA root certificate on to WGB.
AP3802#configure crypto pki trustpoint MRN_TRUST allow-expired-cert Allow expired certificates to be accepted authenticate Get the CA certificate auto-enroll Configure auto-enroll delete Delete a CA trustpoint enroll Request a certificate from a CA enrollment Enrollment parameters import Import certificate key-size Private key size subject-name Subject Name AP3802#configure crypto pki trustpoint MRN_TRUST enrollment terminal ! AP3802#configure crypto pki trustpoint MRN_TRUST authenticate Enter the base 64 encoded CA certificate. ....And end with the word "quit" on a line by itself.... -----BEGIN CERTIFICATE----- -----END CERTIFICATE----- quit Certificate has the following attributes: MD5 Fingerprint=26:5A:98:E9:99:6A:3A:4A:80:47:80:B1:1F:37:8F:5CSHA1 Fingerprint=4D:84:64:C9:34:0F:0F:FB:8F:23:E0:A6:96:14:CF:9B:49:1B:EF:D4 PKI trustpoint configuration has been saved successfully
You can verify certificate details as shown below (not shown the complete output)
AP3802#show crypto pki trustpoint
Crypto PKI trustpoints are:-
================================================================
Trustpoint name : MRN_TRUST
Enrollment method : Terminal
CA-Cert file : /storage/wbridge_pki_cert/MRN_TRUST/MRN_TRUST_ca.pem
Client-Cert file : /storage/wbridge_pki_cert/MRN_TRUST/MRN_TRUST_client.pem
Subject : C=AU,ST=VIC,L=MERNDA,O=MRN,OU=IT,CN=wgb.mrn.local,emailAddress=wgb@mrn.local
Key size : 2048
AP3802#show crypto pki trustpoint MRN_TRUST certificate CA Certificate: Certificate: Data: Version: 3 (0x2) Serial Number: 14:1b:8f:c5:3a:34:8a:a8:45:d3:8d:56:91:64:81:8e Signature Algorithm: sha256WithRSAEncryption Issuer: CN=mrnRootCA Validity Not Before: Aug 31 16:09:05 2019 GMT Not After : Aug 31 16:19:04 2029 GMT
You can configure 802.1X credential profile as shown below. You can delete a configured profile using the “delete” keyword after the credential profile name using the same config line.
AP3802#configure dot1x credential WORD Specify a profile name AP3802#configure dot1x credential MRN-CRD delete Delete the dot1x credential profile username Configure 802.1X username AP3802#configure dot1x credential MRN-CRD username wgb password Configure 802.1X password AP3802#configure dot1x credential MRN-CRD username wgb password xxxx
Next, you can configure an EAP-Profile & specify EAP method you would like to use and attach trust point to that EAP profile. You have to link your dot1x credential profile configured under the previous step.
AP3802#configure eap-profile
WORD Specify a profile name (max 32 characters)
AP3802#configure eap-profile MRN-PRO
delete Delete the EAP profile
dot1x-credential Configure 802.1X credentials profile
method EAP method type
trustpoint Attach CA trustpoint
AP3802#configure eap-profile MRN-PRO method
fast fast method
leap leap method
peap peap method
tls eap-tls method
AP3802#configure eap-profile MRN-PRO method peap
!
AP3802#configure eap-profile MRN-PRO trustpoint
default To use MIC certificate
name To use CA trustpoint
AP3802#configure eap-profile MRN-PRO trustpoint name
WORD Trustpoint Name
AP3802#configure eap-profile MRN-PRO trustpoint name MRN_TRUST
AP3802#configure eap-profile MRN-PRO dot1x-credential MRN-CRD
You can verify your EAP Profile configuration as shown below. By using the “all” keyword you can verify both dot1x credential & eap profile configurations.
AP3802#show wgb eap profile all Shows both EAP and dot1x profile details <cr> AP3802#show wgb eap profile all EAP Profiles are:- ==================================== Profile Name : MRN-PRO Method : PEAP Trustpoint : MRN_TRUST Dot1x Credential : MRN-CRD Dot1x Profiles are:- ==================================== Dot1x Credential : MRN-CRD Username : wgb
Next, you can configure SSID with necessary security methods (Open, PSK, EAP). You can configure PMF and 802.11r if needed. My configuration is simply enabled WPA2 for EAP
AP3802#configure ssid-profile WORD <Enter ssid profile name> AP3802#configure ssid-profile 1X delete Delete the ssid profile said Configure radio service set parameters AP3802#configure ssid-profile 1X ssid mrn-wpa2e authentication authentication method AP3802#configure ssid-profile 1X ssid mrn-wpa2e authentication eap Dot1x method open open method psk Pre-shared key method AP3802#configure ssid-profile 1X ssid mrn-wpa2e authentication eap profile EAP profile configuration AP3802#configure ssid-profile 1X ssid mrn-wpa2e authentication eap profile MRN-PRO key-management key management AP3802#configure ssid-profile 1X ssid mrn-wpa2e authentication eap profile MRN-PRO key-management dot11r 802.11r Fast BSS Transition dot11w 11w PMF Client Configuration wpa2 allow WPA Version 2 clients AP3802#configure ssid-profile 1X ssid mrn-wpa2e authentication eap profile MRN-PRO key-management wpa2 AP3802#configure dot11radio 1 encryption mode ciphers aes-ccm
Finally, you can map SSID profile to Radio interface while configuring it for WGB mode. You can enable/disable radio interface when you do configuration modification on radio interface to take effect.
AP3802#configure dot11radio 1
antenna Configure dot11 radio antenna settings
disable Disabile the selected radio interface
enable Enable the selected radio interface
encryption Configure dot11 encryption parameters
mode Mode of the radio
AP3802#configure dot11radio 1 mode
root-ap Root access point or bridge
uwgb Universal Client
wgb Workgroup-bridge
AP3802#configure dot11radio 1 mode wgb
ssid-profile SSID Profile to be mapped
AP3802#configure dot11radio 1 mode wgb ssid-profile
WORD <Enter the configured ssid profile name>
AP3802#configure dot11radio 1 mode wgb ssid-profile 1X
AP3802#configure dot11radio 1 enable
With this configuration, your client should be able to connect to your SSID (assuming your WLC configured properly with 802.1X SSID)
You can use “show wgb < >” CLI command to verify connectivity details from WGB itself.
AP3802#show wgb ?
bridge Bridge Forwarding/Filtering Database [verbose]
dot11 IEEE 802.11 show information
dot11v 802.11v info
eap Shows EAP information
forwarding WGB Forwarding
mobile Current mobile station
ssid show configured and connected SSID details
statistic Packet statistics
wifi WGB frameware wifi0
You can verify connected SSID details using “show wgb said” CLI command
AP3802#show wgb ssid
Configured SSIDs details:
SSID-Profile SSID Authentication
=======================================================
1X mrn-wpa2e DOT1X
Connected SSIDs details:
Radio ID : 1
Radio Mode : WGB
BSSID : 2C:57:41:52:B0:CB
SSID : mrn-wpa2e
Authentication : DOT1X
You can verify the WGB IP address using “show wgb dot11 associations” CLI command.
AP3802#show wgb dot11 associations
Uplink Radio ID : 1
Uplink Radio MAC : 00:A7:42:BF:CD:6F
SSID Name : mrn-wpa2e
Parent AP Name : AP9130-2
Parent AP MAC : 2C:57:41:52:B0:CB
Uplink State : CONNECTED
Auth Type : DOT1X
EAP Method Name : PEAP
Key management Type : WPA2
Channel : 100
IP : 192.168.99.151/24
Default Gateway : 192.168.99.1
DNS Server1 : 192.168.100.101
Domain : mrn.local
IPV6 : ::/128
Dot11 type : 11ac
Assoc timeout : 5000 Msec
Auth timeout : 5000 Msec
Dhcp timeout : 60 Sec
RSSI : 29
From WLC end, you can verify Here is the WLC end client detail
(vwlc) >show client summary
Number of Clients................................ 2
Number of EoGRE Clients.......................... 0
MAC Address AP Name Slot Status WLAN Auth Protocol Port Wired Tunnel Role
----------------- ---------- ------------- ----- ---- ---------------- ---- ----- ------- ----------------
00:a7:42:bf:cd:6f AP9130-2 1 Associated 19 Yes 802.11ac(5 GHz) 1 N/A No Local
d4:81:d7:bb:15:b3 AP9130-2 1 Associated 19 Yes N/A 1 N/A No Local
(vwlc) >show client detail 00:a7:42:bf:cd:6f
Client MAC Address............................... 00:a7:42:bf:cd:6f
Client Username ................................. WGB
Client Webauth Username ......................... N/A
Hostname: .......................................
Device Type: .................................... Cisco-Device
AP MAC Address................................... 2c:57:41:52:b0:c0
AP Name.......................................... AP9130-2
AP radio slot Id................................. 1
Client State..................................... Associated
User Authenticated by ........................... RADIUS Server
Client User Group................................ WGB
Client NAC OOB State............................. Access
Workgroup Bridge................................. 1 client(s)
Wireless LAN Id.................................. 19
Wireless LAN Network Name (SSID)................. mrn-wpa2e
Wireless LAN Profile Name........................ wpa2e
WLAN Profile check for roaming................... Disabled
Hotspot (802.11u)................................ Not Supported
Connected For ................................... 23547 secs
BSSID............................................ 2c:57:41:52:b0:cb
Channel.......................................... 100
IP Address....................................... 192.168.99.151
.
Policy Type...................................... WPA2
Authentication Key Management.................... 802.1x
Encryption Cipher................................ CCMP-128 (AES)
Protected Management Frame ...................... No
Management Frame Protection...................... No
EAP Type......................................... PEAP
FlexConnect Data Switching....................... Central
Here is the Wired Client detail behind WGB
(vwlc) >show client detail d4:81:d7:bb:15:b3
Client MAC Address............................... d4:81:d7:bb:15:b3
Client Username ................................. N/A
Client Webauth Username ......................... N/A
Hostname: .......................................
Device Type: .................................... Dell-Device
AP MAC Address................................... 2c:57:41:52:b0:c0
AP Name.......................................... AP9130-2
AP radio slot Id................................. 1
Client State..................................... Associated
User Authenticated by ........................... None
Client User Group................................
Client NAC OOB State............................. Access
Workgroup Bridge Client.......................... WGB: 00:a7:42:bf:cd:6f
Wireless LAN Id.................................. 19
Wireless LAN Network Name (SSID)................. mrn-wpa2e
Wireless LAN Profile Name........................ wpa2e
WLAN Profile check for roaming................... Disabled
Hotspot (802.11u)................................ Not Supported
Connected For ................................... 23651 secs
BSSID............................................ 2c:57:41:52:b0:cb
Channel.......................................... 100
IP Address....................................... 192.168.99.152
Gateway Address.................................. 192.168.99.1
Netmask.......................................... 255.255.255.0
If you compare IOS based AP to Click OS-based AP (wave 2 AP), you notice Wave2 APs support newer encryption methods (128/256 bit AES with CCMP/GCMP). During AP boot up you can see the support of that encryption methods verified.
[*07/04/2020 05:18:40.5336] Preparing to set HW specs [*07/04/2020 05:18:40.5339] FIPS enc aes-ccmp Verified [*07/04/2020 05:18:40.5340] FIPS dec aes-ccmp Verified [*07/04/2020 05:18:40.5341] FIPS enc aes-ccmp-256 Verified [*07/04/2020 05:18:40.5342] FIPS dec aes-ccmp-256 Verified [*07/04/2020 05:18:40.5343] FIPS enc aes-gcmp Verified [*07/04/2020 05:18:40.5344] FIPS dec aes-gcmp Verified [*07/04/2020 05:18:40.5345] FIPS enc aes-gcmp-256 Verified [*07/04/2020 05:18:40.5347] FIPS dec aes-gcmp-256 Verified
If you capture wireless traffic when WGB is associate with 802.1X SSID, you will see it is using TLS 1.2 (RFC 5246) when it establishes a secure tunnel for inner EAP exchanges. With traditional IOS APs (eg 3702) you will only see TLS 1.0 (RFC 2246) support. In that way, these latest AP provide better security when it uses as WGB.
Here is the packet capture (mrn-3802-wgb-peap.pcapng) of my 3802 in WGB mode connecting to “mrn-wpa2e” SSID. Pls note it is filtered for WGB mac address & excluding control frames for simplicity.

In the “Client Hello” message coming from WGB listed all those cipher suites supported (55 listed in that frame#13)

In my case RADIUS server (Cisco ISE) dictate to use one of the cipher suites for TLS tunnel establishment. Refer “Server Hello” message in frame#22. You can see “TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (0xc02c)” selected by the RADIUS server as TLS Cipher Suite. It uses ECDHE for Key Exchange with ECDSA signing algorithm. AES-256-GCMP use for encryption and SHA384 for Message Integrity

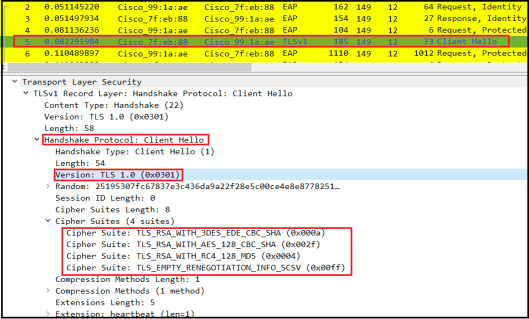
Here is what you see with a traditional IOS AP as WGB (3702 in my case) where it only support TLS 1.0. As you can see in “Client Hello” it only supports RSA for Authenticated Key exchange, AES-128-CBC is the highest encryption cipher (weaker encryption RC4 & 3DES supported too) & SHA-1 for message integrity.
You can see all configurations using “show configuration” or “show run” CLI command as shown below.
AP3802#show running-config AP Name : AP3802 AP Mode : WorkGroupBridge CDP State : Enabled Watchdog monitoring : Enabled SSH State : Enabled AP Username : admin Session Timeout : 900 NTP server ip : 192.168.100.1
Radio and WLAN-Profile mapping:-
====================================
Radio ID Radio Mode SSID-Profile SSID Authentication Method Dot1x UserName
--------------------------------------------------------------------------------------------------------------------------------------
0 RootAP DEFAULT_SSID NA
1 WGB 1X mrn-wpa2e DOT1X PEAP WGB
Radio configurations:-
===============================
Radio Id : 0
Admin state : DISABLED
Mode : RootAP
Radio Id : 1
Admin state : ENABLED
Mode : WGB
Dot11 type : 11ac
Encryption mode : AES128
WGB specific configuration:-
====================================
WGB Radio Id : 1
Mode State : Enable
SSID Profile : 1X
UWGB Radio Id : NA
Mode Enable : NA
SSID Profile : NA
MAC Address : NA
Rx Beacon Missing Count : 0
Packet retries Value : 64
RSSI Threshold Value : -70 dBm
Threshold timeout : 20 sec
HSR-Scan status : Disable
Auth response timeout : 5000 Msec
Assoc response timeout : 5000 Msec
WGB channel scan timeout : 40 Msec
Dhcp response timeout : 60 Sec
EAP timeout : 3000 Msec
Bridge table aging-time : 300 Sec
Probe pak data rate type : NA
Probe pak data rate : 0
Antenna Band Mode : Dual
Broadcast tagging : Disable
Total SSID profiles configured are:
===========================================
SSID-Profile : 1X
SSID Name : mrn-wpa2e
SSID Profile path : /data/platform/wbridge/1X
Auth type : DOT1X
EAP Method : PEAP
Dot1x username : WGB
Key management : WPA2
EAP Profiles are:-
====================================
Profile Name : MRN-PRO
Method : PEAP
Trustpoint : MRN_TRUST
Dot1x Credential : MRN-CRD
Dot1x Profiles are:-
====================================
Dot1x Credential : MRN-CRD
Username : wgb
Crypto PKI trustpoints are:-
================================================================
Trustpoint name : MRN_TRUST
Enrollment method : Terminal
CA-Cert file : /storage/wbridge_pki_cert/MRN_TRUST/MRN_TRUST_ca.pem
Client-Cert file : /storage/wbridge_pki_cert/MRN_TRUST/MRN_TRUST_client.pem
Subject : C=AU,ST=VIC,L=MERNDA,O=MRN,OU=IT,CN=wgb.mrn.local,emailAddress=wgb@mrn.local
Key size : 2048
*** End of WBridge configurations ***
You can refer to this configuration guide for applicable commands for WGB in a Wave2 AP.
I will do a bit more testing with EAP-TLS on WGB and do a post in the near future.
RELATED POSTS
1. WGB with PEAP
2. Wireless & Wired Clients behind WGB
3. IOS AP-WGB with Multiple VLAN

Could you tell me how to packet capture in wireless.I can see your wireless capture is so clearly.
Thanks a lot
Hello,
There is may ways to do it.
If you have a Mac, you can do it very easilty with AirTool freeapplication
https://www.adriangranados.com/apps/airtool
Here is nice video channel by my friend Eddie (watch EP1-4)
You can use Cisco AP in sniffer mode too
HTH
Rasika
HI Rasika,
Thanks a lot!
I wanted to verify that the WGB AP using ME mode or if you connect the AP to the controller and then set it’s mode to bridge to be able to configure WGB from the CLI.
No, WGB is not in ME mode.
Standard CAPWAP mode 3802 conneted to a WLC
Rasika
Can I connect a single device the AP or must it be connected to a switch and my single device plugged into the switch?
Hi Todd, You can do either way, if you have only single device, then you can plug it directly to AP ethernet. If you have more than 1 devices then use a switch. 20 is the max wired devices you can use with WGB
HTH
Rasika
Can this be accomplished with a C-9130 AP?
Not at the moment, it’s only supported in 2802/3802/1562 models
Hello, having an AP 1562D as ME-Root AP and another 1562D as Mesh-AP, does this option support motion (crane)? or does it have to be with the WGB feature, instead of Mesh-AP?
1) – VLANs == Switch Layer 2 == MAP (1562D) == motion == ME-RAP (1562D) == Switch Layer 2
2) – VLANs == Switch Layer 2 == WGB (1562D) == motion == ME-CAPWAP (1562D) == Switch Layer 2
Hi Felix, I do not think these supported in ME (Mobility Express) mode.
If you use WGB (as you put in option 2) you should be able to get it working.
HTH
Rasika
HI Nayarasi,
Great post as always and I love your page 🙂
I was also reviewing WGB config on older AireOS APs and COS APs, I see some terminologies and I was wondering if you can help me to understand them.
WGB mode vs WGB client.
COS APs support WGB mode but not WGB client, while AireOS APs support WGB client (no more WGB infrastructure)
What exactly is difference between WGB mode and WGB client?
Thanks,
Den
Hi!
Great post as well and I love following your page 🙂
I wanted to ask if there is any difference between WGB mode vs WGB client since IOS based APs support WGB client and COS APs support WGB mode, but not WGB client.
Hi Sir,
Hope you are doing very well!, Thank you, i was able to implement WGB with multiple VLAN behind its switch, it requires the following settings to be enabled on WGB Switch and WLC.
WGB Switch-
1.) switch mode trunk – WGB interface (Native VLAN optional)
WLC-
1.) Enable Aironet IE
2.) Enable WGB VLAN client
3.) Enable Broadcast forwarding
4.) Create an interface group adding all the VLAN require (so first create the interface with VLAN taggings and add that interface to the interface group).
5.) add this interface group to the WLAN profile (SSID).
6.) Add the WLAN SSID to the AP group to radiate the SSID.
Thank you Sir,
Aadil – You’re student 🙂
Hi Aadil, Good to hear from you after very long time and I am glad you doing Cisco wireless 🙂 , Where are you based in SL now a days ?
Regarding what you describe closely match with this post
Keep in touch
HTH
Rasika
Will this work utilizing a mobility express controller? I have a single 2802/3802 AP that will be the AP and the ME controller. I will have another 2802/3802 AP as the WGB. Will this work?
Thanks
Jason
Hi Jason, Yes that should work.
Rasika
Hello Rasika,
I’ve been trying to configure my 3802 using PSK and EAP-PEAP and both fails, after I enable the dot11Radio I’m getting this error:
WGB#configure dot11 1 mode wgb ssid-profile 1X
[*10/13/2020 11:52:56.4566] % Failed to start uplink due to Radio 1 is down
[*10/13/2020 11:52:56.4566]
[*10/13/2020 11:52:56.4586] WGB radio configuration has been saved successfully
[*10/13/2020 11:52:56.4586]
WGB#
WGB#configure dot11Radio 1 enable
WGB#[*10/13/2020 11:53:04.6624] DOT11_CFG[1]: Starting radio 1
[*10/13/2020 11:53:04.7902] **Alert: Initial Fw mode wgb Fw mode after cmdset hostap
[*10/13/2020 11:53:04.7987] DOT11_DRV[1]: Started Radio 1
[*10/13/2020 11:53:04.8448] NTP_SERVER_INFO server IP: 192.168.1.100
[*10/13/2020 11:53:04.8716] /opt/cisco/bin/capwapd: opening click/fromhost_srcr6/ether failed!: No such file or directory
[*10/13/2020 11:53:05.2752] chatter: tohost_apphostintf1 :: ToHost: device ‘apphostintf1’ went down
[*10/13/2020 11:53:05.2831] chatter: tohost_apphostintf1 :: ToHost: device ‘apphostintf1’ came up
[*10/13/2020 11:53:05.3232] chatter: tohost_apphostintf1 :: ToHost: device ‘apphostintf1’ went down
[*10/13/2020 11:53:05.3313] chatter: tohost_apphostintf1 :: ToHost: device ‘apphostintf1’ came up
[*10/13/2020 11:53:05.9220] DOT11_DRV[1]: Stopped Radio 1
[*10/13/2020 11:53:05.9463] DOT11_DRV[1]: DOT11_DRV[1]: set_channel Channel set to 36
[*10/13/2020 11:53:05.9705] 13 Oct 11:53:05 ntpdate[15321]: no servers can be used, exiting
[*10/13/2020 11:53:06.4169] DOT11_DRV[1]: Started Radio 1
[*10/13/2020 11:53:07.2749] DOT11_DRV[1]: Stopped Radio 1
[*10/13/2020 11:53:07.2992] DOT11_DRV[1]: DOT11_DRV[1]: set_channel Channel set to 36
[*10/13/2020 11:53:07.7470] DOT11_DRV[1]: Started Radio 1
WGB#[*10/13/2020 11:53:08.8843] DOT11_UPLINK_DRIVER[1]: WGB uplink mode started
[*10/13/2020 11:53:09.1724] chatter: tohost_apphostintf1 :: ToHost: device ‘apphostintf1’ went down
[*10/13/2020 11:53:09.1802] chatter: tohost_apphostintf1 :: ToHost: device ‘apphostintf1’ came up
[*10/13/2020 11:53:09.2550] Radio configuration has been saved successfully
[*10/13/2020 11:53:09.2550]
[*10/13/2020 11:53:12.1777] DOT11_UPLINK_SCAN: SSID is NOT matching
[*10/13/2020 11:53:15.3180] DOT11_UPLINK_SCAN: SSID is NOT matching
[*10/13/2020 11:53:18.4575] DOT11_UPLINK_SCAN: SSID is NOT matching
[*10/13/2020 11:53:21.8441] DOT11_UPLINK_SCAN: SSID is NOT matching
[*10/13/2020 11:55:12.6637] DOT11_UPLINK_SCAN: Scanning again in 5 Seconds
[*10/13/2020 11:55:17.6898] DOT11_UPLINK_SCAN: SSID is NOT matching
[*10/13/2020 11:55:21.0056] DOT11_UPLINK_SCAN: SSID is NOT matching
…
Regardless if I try to use PEAP or PSK I’m getting the same problem. I’m not sure why I can’t connect to any of my WAPs.
This is my configuration:
WGB#show wgb ssid
Configured SSIDs details:
SSID-Profile SSID Authentication
=================================================================================
1X WNet DOT1X
PSK PSK PSK
Connected SSIDs details:
Radio ID : 1
Radio Mode : WGB
BSSID : 00:00:00:00:00:00
SSID : PEAP_SSID
Authentication : DOT1X
WGB#
WGB#show wgb dot11 associations
Uplink Radio ID : 1
Uplink Radio MAC : 00:A2:11:22:33:44
SSID Name : PEAP_SSID
Uplink State : SCAN_START
Auth Type : DOT1X
EAP Method Name : PEAP
Key management Type : WPA2
Channel : 0
IP : 0.0.0.0
IPV6 : ::/128
Dot11 type : NA
Assoc timeout : 5000 Msec
Auth timeout : 5000 Msec
Dhcp timeout : 60 Sec
RSSI : 0
Also I would like to know, based on the Cisco documentation I need to configure an IP for the WAP using the command configure ap ddress ipv4 … This is a requirement?
Finally I have a WLC 5520 running an older version (8.5.140.0), do I need to have same version code?
Thanks for all your help. BTW your webpage is the best Wireless page I’ve ever seen.
Hi Pablo,
Is it possible to start a thread in Cisco support community,
https://community.cisco.com/t5/wireless-and-mobility/bd-p/5956-discussions-getting-started-wireles
It is easier to get input from others and that would be more helpful for everyone else.
Yes, I am checking my blog comments, but if you like to have faster response CSC forum is the best.
Thank you for compliments about my blog
KIT
Rasika
Hello Rasika,
Did you get my question?
Thanks
Yes, I saw it. Pls post it in CSC forum
https://community.cisco.com/t5/wireless-and-mobility/bd-p/5956-discussions-getting-started-wireles
Rasika
Hello Rasika,
Awesome guide.
I followed the process and found out that if the WGB doesn’t have a Client certificate installed (only the CA), the EAP exchange will fail even for PEAP. I noticed you had already a client cert installed on the WGB. Was that cert installed before into the AP?
Hi Edgar,
For PEAP it does not require a client certificate installed on WGB. Only Root Certificate required for RADIUS server cert validation.
For TLS, yes. However I was not able to get TLS working in this setup yet.
HTH
Rasika
hi Rasika,
does version 8.10.122 comes together with the 3802 aps by default? if not how can it be upgraded? thanks
chris
Once you register 3802 to a WLC, it will get the image of that WLC software version.
HTH
Rasika
Hi- do you have any instructions on using a 2802i as a UWGB for an ssid authenticating with WPA2 PSK?
Thanks
Charlie
Hi Charlie, I haven’t play much further to what I did on that post. If I do, will share
Rasika
I’m basically interested in two commands.
1. Is assigning an interface as root ap necessary for a PSK SSID?
(cisco-wave2-ap)#configure dot11Radio radio-int mode root-ap
2. For the mac address portion of the command, are they looking for the mac address of the wired ethernet port of the client? Or the mac address if the parent AP?
(cisco-wave2-ap)#configure dot11Radio radio-int mode uwgb mac-addr ssid-profile ssid-profile-name
Thanks
Hey Rasika Nayanajith,
How are you doing? I hope you are well.
Great post as well and I love following your page.
Rasika Nayanajith, I would like to know if the Cisco Access Point AIR-AP1562E-Z-K9 with software version 17.7.1.11 (Details bellow) configured as WGB support AAA configuration for user authenticate via TACACS or RADIUS?
Thank you in advanced for support.
Details for Access Point Version (Show Version)
cisco AIR-AP1562E-Z-K9 ARMv7 Processor rev 1 (v7l) with 1028224/594556K bytes of memory.
Processor board ID FGL2432L6VA
AP Running Image : 17.7.1.11
Primary Boot Image : 17.7.1.11
Backup Boot Image : 0.0.0.0
Primary Boot Image Hash:
Backup Boot Image Hash:
1 Gigabit Ethernet interfaces
2 802.11 Radios
Radio Driver version : 9.0.5.5-W8964
Radio FW version : 9.1.8.1
NSS FW version : 2.4.28
Base ethernet MAC Address : 3C:13:CC:E6:AC:6E
Part Number : 73-100839-07
PCA Assembly Number : 000-00000-00
PCA Revision Number :
PCB Serial Number : FOC24282LLB
Top Assembly Part Number : 068-100610-03
Top Assembly Serial Number : FGL2432L6VA
Top Revision Number : A0
Product/Model Number : AIR-AP1562E-Z-K9