Tags
In the previous post we looked at H-REAP modes with WPA2-PSK. In this post we will see how to configure H-REAP (for Local Authentication) with external RADIUS server.
I have slightly modified my previous topology by adding one more H-REAP in brach office. So here is the diagram for this post.
H-REAP to work with External RADIUS server in Local Authentication mode you have to configure H-REAP to communicate with external RADIUS. We have used ACS as external RADIUS server.
I will go through specific configuration related to external radius and basic configuration will not shown here. We have already created two users (user1 & user2) in ACS in a previous post (Read PEAP EAP-FAST with ACS5.2 & H-REAP Modes of Operation before this) & “data” WLAN created.
In CAT4, Fa1/0/13 & fa1/0/14 configured as trunk ports (as H-REAP carry multiple vlan traffic) with native vlan 121. Mgt IP vlan of the H-REAP should be native vlan across this trunk.
interface FastEthernet1/0/13 switchport trunk encapsulation dot1q switchport trunk native vlan 121 switchport mode trunk spanning-tree portfast trunk ! interface FastEthernet1/0/14 switchport trunk encapsulation dot1q switchport trunk native vlan 121 switchport mode trunk spanning-tree portfast trunk
“data” WLAN configured for Local Authentication & Local Switching in WLC(see below)
In ACS5.2 you can add H-REAP-01 & H-REAP-02 as network resources. This is required when AP work in local authentication mode, H-REAP send the request to configured backup server (in our case we have only one ACS & we will configure it on H-REAP). Failure will simulate shutting down the WLC connected switchport in Head Office. Below show the ACS configuration required to add HREAP.
Once you configured ACS, you have to configure H-REAP with ACS server IPs. You can configure it via WLC CLI or GUI method. First we look at CLI method. First you have to find H-REAP details via WLC CLI as shown below.
(WLC1) >show ap sum Number of APs.................................... 2 Global AP User Name.............................. Not Configured Global AP Dot1x User Name........................ Not Configured AP Name Slots AP Model Ethernet MAC Location Port Country Priority ------------------ ----- -------------------- ----------------- ---------------- ---- ------- ------ H-REAP-02 2 AIR-LAP1252AG-N-K9 54:75:d0:dd:a4:88 default location 1 AU 1 H-REAP-01 2 AIR-CAP3502I-N-K9 70:81:05:03:7c:ef default location 1 AU 1
You can issue CLI commands into APs connected to controller by “config ap < CLI COMMAND> <AP NAME> ” syntax. In our case you can do this as follows. I have used the same key defined on ACS on H-REAP.
(WLC1) >config ap h-REAP ? radius Config H-REAP backup Radius Server in standalone mode vlan Enables/Disables VLAN on the H_REAP. (WLC1) >config ap h-REAP radius ? auth Authentication Server (WLC1) >config ap h-REAP radius auth ? set Set H-REAP backup Radius Server delete Delete H-REAP backup Radius Server (WLC1) >config ap h-REAP radius auth set ? primary Primary Radius Server secondary Secondary Radius Server (WLC1) >config ap h-REAP radius auth set primary ? <IP_Addr> Radius Server IP address (WLC1) >config ap h-REAP radius auth set primary 192.168.100.2 ? <auth_port> Authentication port number (WLC1) >config ap h-REAP radius auth set primary 192.168.100.2 1812 ? <secret> Radius Server secret (WLC1) >config ap h-REAP radius auth set primary 192.168.100.2 1812 cisco ? <Cisco AP> Enter the name of the Cisco AP. (WLC1) >config ap h-REAP radius auth set primary 192.168.100.2 1812 cisco H-REAP-01 (WLC1) >config ap h-REAP radius auth set primary 192.168.100.2 1812 cisco H-REAP-02
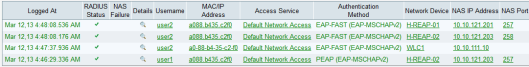
Now you can test this using AnyConnect client. First will connect to “data” SSID & see the authentication success on ACS. As you can see H-REAP is using ACS as primary RADIUS & straightaway it goes to Local Auth (even though central Auth available via WLC). In practical scenario, we configure Head Office ACS as primary server & another server as backup for branch H-REAP to reach in case of WAN failure.
In order to do this via WLC GUI you can create an H-REAP group and assign AP into that group. H-REAP Group can be administratively easy to manage large number of H-REAP as you can add/remove AP from the group rather go to individual AP & change the settings.To facilitate fast roaming (CCKM or OKC) you have to create H-REAP group
you can delete the configured RADIUS information using following CLI command.
(WLC1) >config ap h-REAP radius auth delete primary H-REAP-01 (WLC1) >config ap h-REAP radius auth delete primary H-REAP-02
You can define a H-REAP group under Wireless tab.
You can configure RADIUS server information within the H-REAP group & you can add APs into this group.
I could not see a option to set secret key. I think by default it use the key set between WLC & ACS. If you want to override it you have to use the CLI command “config ap h-REAP radius auth set primary 192.168.100.2 1812 cisco H-REAP-01″. Here is the ACS authentication logs when user is connected to H-REAP
Then I shutdown the WLC connected switchport (G1/0/1 on CAT2). You can see below msg on H-REAP console that it goes to standalone mode.
H-REAP-02# *Mar 11 18:11:10.999: %LWAPP-3-CLIENTEVENTLOG: Switching to Standalone mode *Mar 11 18:11:11.043: %DTLS-5-SEND_ALERT: Send FATAL : Close notify Alert to 10.10.111.11:5246 *Mar 11 18:11:11.087: %WIDS-5-DISABLED: IDS Signature is removed and disabled. *Mar 11 18:11:11.087: %CAPWAP-5-CHANGED: CAPWAP changed state to DISCOVERY Translating "CISCO-LWAPP-CONTROLLER"...domain server (255.255.255.255) Translating "CISCO-CAPWAP-CONTROLLER"...domain server (255.255.255.255)
You can verify client connectivity in this situation by using AnyConnect client. Here is the ACS authentication log this time.
Now you can check roaming of a client between H-REAP-01 & H-REAP-02. I would simulated this by turn off AP where client associated & force them to move to next AP (sorts of roaming). I use ICMP ping to see how may packets drops when moving HREAP-01 to HREAP-02. Here is the output & you can see there are 2 packet drops.
This is because we have not configured any fast roaming mechanisms(CCKM or OKC) on this WLAN. If you see L2 security it was configured for just 802.1x. As you can see below client get fully authenticated by H-REAP-02 once client is moved into that AP which takes noticeable time.
Let’s enable CCKM on the wlan “data”. I have selected “802.1x + CCKM” as that would be the most practical way of configuring it. If you just enable “CCKM” only CCKM compatible devices can join the network. Make sure WLC is back online & both H-REAPs are on to start with. From 7.0.116.0 code onwards OKC(Opportunistic Key Caching) is enabled when you configure an H-REAP group, which helps for non-CCKM client for fast roaming.
You can check OKC key cache info using “show capwap reap pmk” on AP CLI. As my windows PC in not cisco client it will use OKC.
H-REAP-01#sh capwap reap pmk PMK Cache Entries:: HW Address Life Time(in sec) BSSID Source a088.b435.c2f0 86322 5475.d03e.80be OKC (Controller) Total number of PMK cache entries = 1 Total number of OKC entries = 1 ! H-REAP-02#show capwap reap pmk PMK Cache Entries:: HW Address Life Time(in sec) BSSID Source a088.b435.c2f0 86292 5475.d03e.80be OKC (Controller) Total number of PMK cache entries = 1 Total number of OKC entries = 1
If it is CCKM client you can use “show capwap reap cckm” CLI command. I have my 7921 joined to this WLAN to get some CCKM client key info.
H-REAP-02#sh cap reap cckm
CCKM Cache Entries:
HW Address Life Time(in sec) BSSID
001b.d458.e61a 86187 a0cf.5b9e.e82e
Total number of cache entries = 1
Now will do the same test by shutting down the H-REAP-01 where my PC associated with. As you can see this time I saw only 1 packet drop, reduces roaming time from one AP to another. I have to learn this fast roaming stuff in detail as I have no clear idea difference between two mechanism (CCKM & OKC)
There is one more topic I need to cover on H-REAP, which is local authentication (only LEAP or EAP-FAST supports) when primary RADIUS is not available. Will see how that work in a later post.
Related Posts
1. Office Extend – Overview
2. Configuring OEAP
3. How does OEAP work ?
4. H-REAP Modes of Operation
5. OEAP – Multiple Remote LANs



Great post Rasika. Question though:
When you simulated the ‘failure’. Did you take down the WAN link or just the WLC? I’m assuming if you took down the WAN link then Radius authentication would not have worked.
Everytime I see ‘local authentication’, I think of having a design of a local radius server vs external.
After reviewing, I see that the ‘variable’ is that its not going through the WLC, but rather straight from the AP itself. Regardless of where the Radius server itself is located (local to AP or external across WAN).
Hi Nolan,
Yes, in this scenario (my example) If I take down WAN link external RADIUS would fail. Therefore I simulated a failure removing the link to WLC.
Per documentation on http://www.cisco.com/en/US/products/ps10315/products_tech_note09186a0080736123.shtml#HREAPGROUPS we need HREAP group to support CCKM/OKC roam.
But, if the wlan is configured for only 802..1x, then HREAP group for CCKM roam is useless, correct?
Correct me if I am wrong in interpreting this article, we need wlan on 802.1x + CCKM and HREAP group with AAA server added to support CCKM fast roam on hreap AP’s?
Hello Rasika,
From configuration standpoint what is the difference between Local Authentication and Central Authentication for H-REAP when using Radius?
Is there a difference as both will use one appointed IP of the Radius Servers?
Hi Florin,
If you are using RADIUS, then for local authentication you should have Local RADIUS server at brach (so even if WAN link is down you can do local auth)
If you are using Central auth, then when WAN link goes down you can’t do anymore new authentication
(since RADIUS is not reachable)
Hope that clarifies your query
Rasika
I enabled Local Authentication (PEAP) and it’s not working. After some reading, I found out the reason: requests are sourced by AP and this AP is not registered with the Radius Server. Makes sense.
Also I read that using FlexConnect Groups could save the day for the Local Authentication and not require the previous AP&RADIUS Server registration.
Is that true? If YES, how’s this possible? Supposing AP works in standalone mode and Local Authentication is enabled, BUT there is no registration on the RADIUS server for the authenticating AP, is this AP use from its configuration the WLC IP?
I use the same configuration but get an error on the ACS ” 5411 EAP session timed out” I have restarted ACS services w no luck. Any suggestions? I am able to get users authenticated with AP is connected mode.